- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Today I saw this on reddit:
https://www.reddit.com/r/synology/comments/18jofdu/nas_hit_by_ransomware_ds720/
Synology is purportedly the leader in NAS software security (at least according to NAS Compares, and other similar NAS reviewers). To see this user get nailed today gave me pause, with my now obsolete ReadyNAS boxes (RN528X, RN424, RN212).
What, if anything, can I do to increase security on these boxes? I'm quite sure I'm doing plenty of things wrong, here's the basic setup:
- 3 NAS boxes are ETH-connected to my home network (10GbE and 1GbE)
- Home network is an Orbi 960 mesh system (RBK963), which sits in front of a 1Gbps Spectrum cable modem
- On the RN528X, under Accounts, the "Users" and "Groups" have two members - Admin, and istatserver (an app I loaded but since disabled). There are no users underneath. I'm guessing this is maybe a problem, read somewhere it's a bad idea to use Admin as the primary access but don't understand why. Security issue??
- Permissions aren't set any specific way, as I have zero understanding in this area as well. I've tried messing with permissions in Windows over the years, never works the way it seemingly should and always gets me into trouble.
I don't see any provision for 2FA or other basic security measures with these boxes. I don't want to remove the devices from the home network, that defeats the purpose of having easy access to them.
Any measures I can take to improve security, short of disconnecting them from the network entirely?
I don't access these boxes remotely (any longer), since ReadyCloud bit the dust. I would like to have a way to do this going forward though... some VPN solution I guess. Any advice here would also be much appreciated.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@jimk1963 wrote:
Today I saw this on reddit:
https://www.reddit.com/r/synology/comments/18jofdu/nas_hit_by_ransomware_ds720/
This has happened before (more broadly) to Synology and I think QNAP. The vector in the past was the cloud services set up by Synology and QNAP.
So in general you do need to be cautious on how you set up remote access. Personally I use the openVPN service built into my Orbi router.
The other major vector for ransomware is through your home PCs. Since they have access to the NAS shares, ransomware on the PCs can encrypt (or destroy) files on the NAS also. If the shares can be accessed without credentials (passwords) or if passwords are saved on the PCs, then ransomware can reach the NAS very easily.
Most of these attacks include a social engineering component - for example, phishing emails that include malicious website links or attachments with embedded malware.
The strongest protection against this is to have a copy of your files that cannot be reached by the ransomware attack. I have a backup NAS on a power schedule. It can't be reached when it is powered down. If ransomware were to hit, I'd have some time to disconnect the NAS from my network before the next backup is scheduled.
Less expensive is to use USB drives for backup - connecting them when you make the backups, and disconnected them immediately afterwards.
Cloud backup is another option - several cloud backup services do have some protection against ransomware attacks, and even if that fails you should be able to roll back to file versions saved before the attack hit.
As an aside, there are other threats with similar impact - fire, flood, theft, etc. Protection from them requires some off-site storage.
@jimk1963 wrote:
There are no users underneath. I'm guessing this is maybe a problem, read somewhere it's a bad idea to use Admin as the primary access but don't understand why. Security issue??
If someone gets the admin password to your NAS, then they can log into the admin web ui. From there they can do a lot of bad stuff.
- enable ssh, and install whatever software they like on the NAS
- silently copy all your data
- destroy your volume
- ...
Also, you can also do more damage accidently from windows if you are using admin credentials than you can do if you are using a more restricted account.
All Replies
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@jimk1963 wrote:
Today I saw this on reddit:
https://www.reddit.com/r/synology/comments/18jofdu/nas_hit_by_ransomware_ds720/
This has happened before (more broadly) to Synology and I think QNAP. The vector in the past was the cloud services set up by Synology and QNAP.
So in general you do need to be cautious on how you set up remote access. Personally I use the openVPN service built into my Orbi router.
The other major vector for ransomware is through your home PCs. Since they have access to the NAS shares, ransomware on the PCs can encrypt (or destroy) files on the NAS also. If the shares can be accessed without credentials (passwords) or if passwords are saved on the PCs, then ransomware can reach the NAS very easily.
Most of these attacks include a social engineering component - for example, phishing emails that include malicious website links or attachments with embedded malware.
The strongest protection against this is to have a copy of your files that cannot be reached by the ransomware attack. I have a backup NAS on a power schedule. It can't be reached when it is powered down. If ransomware were to hit, I'd have some time to disconnect the NAS from my network before the next backup is scheduled.
Less expensive is to use USB drives for backup - connecting them when you make the backups, and disconnected them immediately afterwards.
Cloud backup is another option - several cloud backup services do have some protection against ransomware attacks, and even if that fails you should be able to roll back to file versions saved before the attack hit.
As an aside, there are other threats with similar impact - fire, flood, theft, etc. Protection from them requires some off-site storage.
@jimk1963 wrote:
There are no users underneath. I'm guessing this is maybe a problem, read somewhere it's a bad idea to use Admin as the primary access but don't understand why. Security issue??
If someone gets the admin password to your NAS, then they can log into the admin web ui. From there they can do a lot of bad stuff.
- enable ssh, and install whatever software they like on the NAS
- silently copy all your data
- destroy your volume
- ...
Also, you can also do more damage accidently from windows if you are using admin credentials than you can do if you are using a more restricted account.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
@StephenB wrote:This has happened before (more broadly) to Synology and I think QNAP. The vector in the past was the cloud services set up by Synology and QNAP. .
Nope. Start reading and understanding about EternalBlue and Wanna Cry. The majority of RandomWare attacks cam in by unaware and careless users, blindly opening files of whatever content containing malware where it can cause most effect: Where users believe it is "secure", on any kind of shared folders.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
@schumaku wrote:
@StephenB wrote:This has happened before (more broadly) to Synology and I think QNAP. The vector in the past was the cloud services set up by Synology and QNAP. .
Nope.
I pointed out that the main vector was through the local PCs (and specifically mentioned phishing).
But there are quite a few vulnerabilities that have been uncovered over the years with QNAP cloud software, including their QNAP photo station fairly recently.
The Synology vulnerability I was thinking about was some years ago ("SynoLocker"). The vulnerability was in their DSM software, but clearly required some form of remote access to exploit. Reading through it again, it's not clear if Synology's cloud service was part of the exploit or not.
While I think both vendors are well-intentioned, I still think that using vendor-supplied "free" cloud infrastructure for remote access and file sharing is a significant risk.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
Both Synology and QNAP have experienced well documented ransomware attacks. Synology had Synolocker and then recently, whatever this user had happen to him/her.
QNAP has suffered several ransomware attacks, here’s a QNAP PR from 2021:
https://www.qnap.com/static/landing/2021/qlocker/response/da-dk/
NASCompares and others have been reporting on this for quite some time.
Haven’t reviewed the specific mechanisms these hackers used to gain access, seems to be more sophisticated than the typical phishing approaches but not sure.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
@jimk1963 wrote:
Haven’t reviewed the specific mechanisms these hackers used to gain access, seems to be more sophisticated than the typical phishing approaches but not sure.
I didn't see any reports that including phishing in those exploits.
I saw brute-force attacks on admin passwords listed in at least one of the attacks (and if a NAS manufacturer is targetted, then obviously the default admin passwords will be first on that list).
Another theme was users not updating the software regularly - in several cases QNAP and Synology had fixed security vulnerabilities months (or even years) earlier, but users hadn't bothered to install the updates.
In the specific case of ReadyNAS running OS-6:
- The version of Linux ( Debian 8 ) has been archived/deprecated, so any security fixes in the future would need to be back-ported by Netgear.
- Since Netgear has also dropped software support, they are unlikely to get timely notice of an exploit aimed at ReadyNAS products.
- Available apps are not maintained, and often the current version of popular apps can not be installed, due to out-of-date libraries. Old app versions might be missing security fixes.
I think the best strategy for ReadyNAS users is to avoid exposing their NAS to inbound internet connections. Personally I've only used my ReadyNAS for storage from some time. No apps are running on them, no ports are forwarded to them, and remote access is only done through openVPN. uPNP is disabled in my router (a basic precaution that also helps protect PCs).
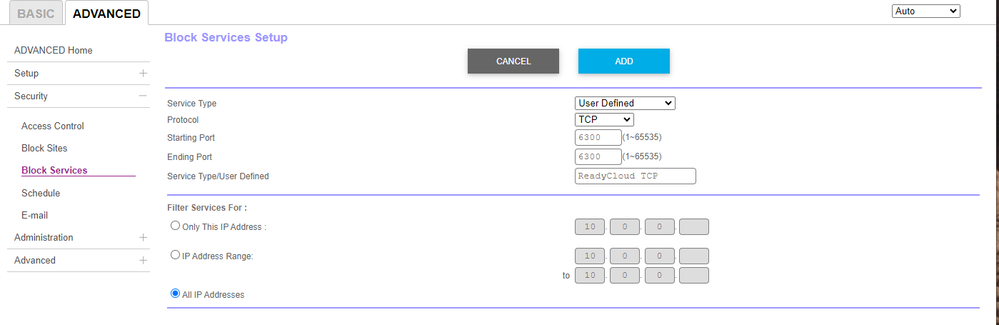
One thing I don't like is that Netgear hasn't released firmware that completely removes the ReadyCloud client from the firmware. Blocking traffic (both inbound and outbound) for port 6300 in your router might be a good precaution.
Given the history, I personally would avoid apps and remote access software from any NAS vendor, and continue to use my NAS simply for storage. I run apps on a separate PC server. My backup NAS (I use a couple) are all on a power schedule, so essentially air-gapped when not performing their backups. Their schedules are staggered, so I should have time to disconnect them from the network if I find the primary NAS has been compromised.
I also use cloud backup (running on a PC) for disaster recovery - many cloud backup systems have some detection in place for ransomware, and they all should let you roll back to a previous (unencrypted) version of the files.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
Thanks @StephenB , very helpful.
Re:
I think the best strategy for ReadyNAS users is to avoid exposing their NAS to inbound internet connections. Personally I've only used my ReadyNAS for storage from some time. No apps are running on them, no ports are forwarded to them, and remote access is only done through openVPN. uPNP is disabled in my router (a basic precaution that also helps protect PCs).
Maybe a really dumb question - my NAS's are DHCP assigned on my network, connected via 10GbE or 1GbE. I'm not running any apps on the NAS units, and no ports are knowingly forwarded. Other than powering the units off (per your comments), seems a NAS is inherently at risk as long as it, and any PC, are turned on in the home since they reside on the same network. Am I missing something? I don't have any VPN set up so there's no remote access possible that I'm aware of. I looked into OpenVPN on the Orbi, not exactly straightforward. Sounded like I need to sign up for some service or establish some account to make it work.
Re:
One thing I don't like is that Netgear hasn't released firmware that completely removes the ReadyCloud client from the firmware. Blocking traffic (both inbound and outbound) for port 6300 in your router might be a good precaution.
Looking at the Orbi web GUI, it's not clear to me how to do this. There are many source types to choose from - I tried ALL, but then it wouldn't let me fill in any port numbers. I tried "Any (TCP)" and filled in 6300 for the port number, that failed also. If possible, please dumb it down for me as to how to set parameters to close this port. Finally, researching Port 6300, I didn't find anything very helpful - does closing this port have unwanted side effects? Like other software programs not working, or losing access to networked devices, etc?
I'll look into the backup service you mentioned, sounds like what I'm looking for. Something that can be slow, but reliable for disaster recovery.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
@jimk1963 wrote:
Maybe a really dumb question - my NAS's are DHCP assigned on my network, connected via 10GbE or 1GbE. I'm not running any apps on the NAS units, and no ports are knowingly forwarded. Other than powering the units off (per your comments), seems a NAS is inherently at risk as long as it, and any PC, are turned on in the home since they reside on the same network. Am I missing something?
If you did allow inbound connections to the NAS over the internet (ssh, https, ftp, torrent software, etc) then there is a possibility that the NAS could be hacked.
But I think the biggest risk by far is that a PC on the network will become infected with malware or ransomware - often involving social engineering (convincing someone to click on an malicious attachment or website). If the PC has access to NAS shares, then the infection can spread to the shares - even if the NAS operating itself is not compromised.
@jimk1963 wrote:
Looking at the Orbi web GUI, it's not clear to me how to do this. There are many source types to choose from - I tried ALL, but then it wouldn't let me fill in any port numbers. I tried "Any (TCP)" and filled in 6300 for the port number, that failed also. If possible, please dumb it down for me as to how to
This works:
Then I've done the same thing, but selecting UDP and changing the service name to ReadyCloud UDP.
@jimk1963 wrote:
I looked into OpenVPN on the Orbi, not exactly straightforward. Sounded like I need to sign up for some service or establish some account to make it work.
You do need to set up a DDNS (Dynamic DDNS) account. Netgear provides a free one (hosted by noip.com) that uses XXXXX.mynetgear.com URL. Once a month you'll get an email from noip.com asking you to confirm that you still want the URL, which isn't difficult.
The steps for that are here:
DDNS doesn't give anyone access to your network, it just assigns the URL you set up to your router, and allows you to reach the router using that URL. When your ISP changes your router's WAN address, the service will update to point to your new addess.
After you have DDNS set up, you configure OpenVPN using this guide:
Then install the client on your PC and phones using this:
- https://kb.netgear.com/31487/How-do-I-use-VPN-service-on-my-Orbi-system-with-my-Windows-client
- https://kb.netgear.com/29826/How-do-I-use-VPN-on-my-NETGEAR-router-with-my-iOS-device
- https://kb.netgear.com/29783/How-do-I-use-VPN-service-on-my-router-with-my-Android-device
- https://kb.netgear.com/25389/Enabling-VPN-service-on-a-NETGEAR-router-using-a-MAC-OS-computer
(These aren't all written for Orbi, but AFAICT the steps are the same on all Netgear routers that include OpenVPN).
So there are definitely several steps needed, but the guides are pretty clear.
@jimk1963 wrote:
I'll look into the backup service you mentioned, sounds like what I'm looking for. Something that can be slow, but reliable for disaster recovery.
Getting everything uploaded initially took a few months, so it is definitely much slower than my internet connection. It has kept up once I got it initially synced.
The terms of service for my subscription is to back up one PC with unlimited storage. In my case the PC is my NAS (although the backup service is running on a Windows PC with the data volume mapped to a drive letter). I do stay within the bounds of the subscription - the PC itself isn't included in the backup, only the NAS is being backed up
I've been using it since 2012 - a couple of hiccups along the way, but so far it is working ok. Initially I ran it on my Pro 6 (my primary NAS at the time), but after a while it required more memory that the Pro 6 supported, so I switched to running it on a PC..
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
Re: DDNS setup in my Orbi, I'm getting an error as shown below when I type in my DDNS credentials and hit "Apply". Says it's unable to locate hostname. When I click "Show Status" on the router, I get the popup box shown below ("service provider is not reachable"). I tried purposely entering a bad password, the error message follows (name and/or password is incorrect). So the error below is not a username/password issue.
I'm using "NETGEAR" as the service provider, and have successfully logged into my.no-ip.com where I can see the host name I chose. It shows my host name as xxxxxxxxxxx.mynetgear.com, with an IP/Target of 76.xx.xx.xx and says "Active".
I assume I can't move onto OpenVPN steps until this DDNS link is established - correct?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
@jimk1963 wrote:
I assume I can't move onto OpenVPN steps until this DDNS link is established - correct?
It does need to work.
- Is the hostname configured in the router fully qualified? (includes the .mynetgear.com)?
- Did you try rebooting the router?
If you install the noip DUC client on a PC, does that work?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
Found a post stating NETGEAR as the service provider is dead, instead use no-ip as the service provider. Once I did that, and entered the credentials, I get a successful status ("Show Status").
Have successfully connected to OpenVPN on my iOS device it appears. The OpenVPN app shows a "Connection Stats" graph, and below that shows a private IP (192.168.254.2 ... not sure what this is ???) and for the server, it shows xxxxx.mynetgear.com and the server public IP is my ISP IP, through Port 12973 with UDP protocol.
Now I need to figure out what to do with this connection... I want to access the NAS folders using my iPhone (and eventually my windows laptop). In the past, I could use the ReadyCloud app on the iPhone to see the folders directly. Without that app, what app do I use to be able to see my Wiindows related drives/folders on iPhone? I looked at "Files", don't see anything there.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
@jimk1963 wrote:
Found a post stating NETGEAR as the service provider is dead, instead use no-ip as the service provider. Once I did that, and entered the credentials, I get a successful status ("Show Status").
Interesting, as it is still working on my Orbi. Perhaps because my account is pretty old.
@jimk1963 wrote:
shows a private IP (192.168.254.2 ... not sure what this is ???)
It's your phone's local IP address on the VPN connection.
@jimk1963 wrote:
Now I need to figure out what to do with this connection... I want to access the NAS folders using my iPhone (and eventually my windows laptop). In the past, I could use the ReadyCloud app on the iPhone to see the folders directly. Without that app, what app do I use to be able to see my Wiindows related drives/folders on iPhone? I looked at "Files", don't see anything there.
Files works.
- Select Browse
- Press the three dots in the upper right
- enter smb://nas-ip-address in the server field
- then enter your NAS credentials
You should then be able to browse your shares. Files should remember the server, so you shouldn't need to re-enter this the next time.
Note this will work at home with OpenVPN off - you only need to enable the VPN when away.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
THANKS @StephenB !
VPN into NAS works perfectly via Files on iOS.
“smb://nas-ip-address” connection info - didn’t see this step anywhere but now I can easily find references on the web.
It’s amazing how bottomless this stuff feels sometimes, even though the answers are “right there”.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Ransomware - how to prevent on RN528X and RN424 (and RN212)
@jimk1963 wrote:
VPN into NAS works perfectly via Files on iOS.
Great!
The VPN will also give you access to other devices on your home network. For instance, if you install the windows client, the laptop should be able to print to your home printer when you are remote. Though I don't think airprint will work from your iphone.