- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
ReadyNas RN2100 hacked
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ReadyNas RN2100 hacked
So it appears that my credentials were exposed after a recent data breach from Netgear (thanks guys) and I received an email a few months back saying all my data and been stolen and I wanted to get it back is to pay crypto. Luckily for me, I only saved irrelevant files such as movies and TV shows, so I am not really interested in getting it back.
However what I want to know is, how can I secure my device to ensure the cloud account is no longer linked to my device and what is the best way to use this device moving forward? I never got any email correspondence regarding the end of life of ReadyNAS which is dissapointing but I am not finger pointing or angry, just wanting to resolve this so I can resume my movie server.
Any help is appreciated! Thank you
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: ReadyNas RN2100 hacked
@apopcontest wrote:
So it appears that my credentials were exposed after a recent data breach from Netgear (thanks guys)
I'm puzzled here. Can you confirm that the NAS is an RN2100 running 4.1.x firmware? Did you get an email from Netgear telling you there was a breach? Or are you just speculating?
The Netgear cloud services that can reach your NAS over the internet (photos and readyremote) were taken down long ago. There is no Netgear cloud account or server that is linked to your NAS.
How were the hackers able to reach your NAS? Were you forwarding ports to it?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: ReadyNas RN2100 hacked
Hello,
Currently away from where my NAS is located for a few days, I can confirm that my NAS is RN2100 running 4.1.x firmware and I do recall reading an email from Netgear informing me of a data breach, however I have had a few to be honest and I never really paid attention to them too much.
I was under the impression that ReadyNAS Cloud was only closed late last year (which I was unaware of) and I have ReadyCloud Client installed on my computer which I cannot access which I understand.
I am not sure how the hackers were able to access my NAS, I can access it using what I created at the time for my username and password which was email and an old password which I never changed, I believe this password is probably available somewhere online for people to make attempts to login using my credentials,Would this be how they were able to access my NAS?
Any recommendations on how to move forward? Do a hard reset? My concern would be that if I placed data on my NAS, a hacker would be able to access my NAS using my old credentials.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: ReadyNas RN2100 hacked
@apopcontest wrote:
I was under the impression that ReadyNAS Cloud was only closed late last year (which I was unaware of) and I have ReadyCloud Client installed on my computer which I cannot access which I understand.
Netgear branding has often re-used old names, which unfortunately creates a lot of confusion. The ReadyCloud you had installed was shut down in September 2016, so your NAS hasn't been connected to it for 7 years.
The service that was shut down in July was only for ReadyNAS running 6.x firmware. So not compatible with your NAS.
@apopcontest wrote:
I am not sure how the hackers were able to access my NAS, I can access it using what I created at the time for my username and password which was email and an old password which I never changed
Let's start from the beginning. FWIW, I don't think your NAS ever supported email format usernames, so that part of your email is a bit confusing.
What apps did you have installed on your NAS? Bittorrent perhaps?
Did you ever forward any ports in your router to the NAS?
You received an email from someone claiming to have encrypted your files. Did they specifically say they had hacked your ReadyNAS? Or just that they had encrypted files? Did you click on any links or open any attachments in that email? It's possible that the email was fake.
You are away from home, and cannot access your NAS. Have you tried accessing it while you were home? When did you lose access?
If you have access, are you able to see your shares? If so, what files are you seeing in the shares?
When you try to access frontview now (when home) are you getting an SSL version or Cipher Mismatch error? Or are you getting something else.
@apopcontest wrote:
I believe this password is probably available somewhere online for people to make attempts to login using my credentials,Would this be how they were able to access my NAS?
Not unless you had forwarded ports to the NAS to enable remote connections. Or alternatively if they compromised a PC you use to connect to the internet.
@apopcontest wrote:
Any recommendations on how to move forward? Do a hard reset? My concern would be that if I placed data on my NAS, a hacker would be able to access my NAS using my old credentials.
FWIW, I am not (yet) seeing strong evidence that the NAS was in fact hacked. There were changes in Chrome, Edge, Firefox, and Safari last year that do prevent access to Frontview. There are some workarounds, but AFAICT you don't know about them.
It is also possible that disk failures (or a NAS failure) is the actual cause of your problem. So there are other explanations to lack of access that haven't really been ruled out.
Do you only have an access problem reaching your files? Or do you actually see encrypted files on the NAS when you access it.
As far as old credentials go, if you do a factory default then those credentials will no longer work with the NAS. But of course if you also use them for other devices (or accounts) you should start by changing them.
Plus access to your NAS over the internet requires more than the old credentials. Normally your router won't allow a hacker to reach the NAS. So we'd also need to understand how the alleged hacker managed to get through your router.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: ReadyNas RN2100 hacked
Sorry I don't know how to quote, so I will try and answer accordingly...
What apps did you have installed on your NAS? Bittorrent perhaps?
Did you ever forward any ports in your router to the NAS?
Not Bittorrent, I only had Plex Server installed on NAS, could they have gained access with a compromised username and password on Plex?
You received an email from someone claiming to have encrypted your files. Did they specifically say they had hacked your ReadyNAS? Or just that they had encrypted files? Did you click on any links or open any attachments in that email? It's possible that the email was fake.
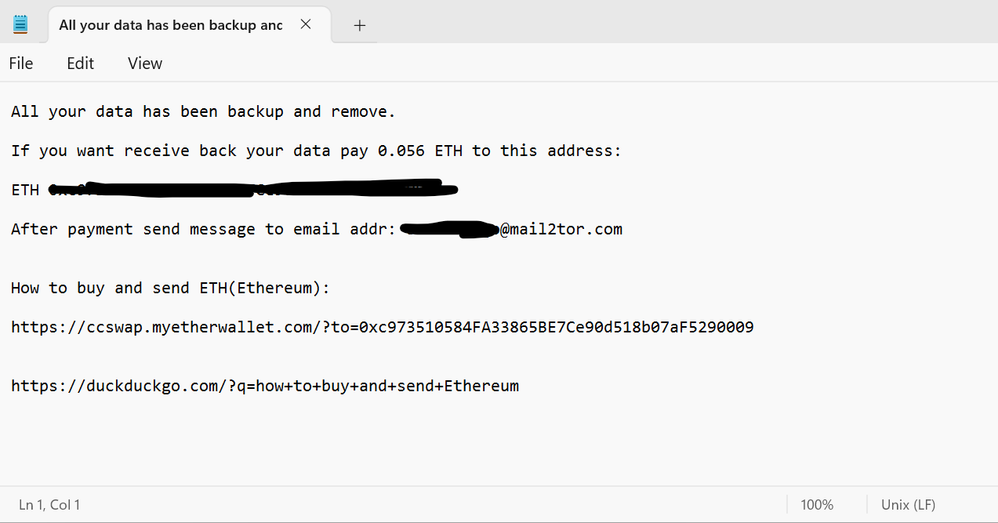
Please see this screenshot, the same message was saved on my NAS which was emailed, which I initially ignored as I was busy at the time. I have blocked out other information for the safety of others.
Not unless you had forwarded ports to the NAS to enable remote connections. Or alternatively if they compromised a PC you use to connect to the internet.
Is there a way to find this?
Here are some other screenshots for further assistance.
Moving forward, should I remove the Plex App? Hard to tell if my computer was compromised I do have paid antivirus protection on my laptop. I have been exposed to a few data breaches already but nothing too major (so far), I thought perhaps my older credentials have been sitting somewhere on the internet and someone had a crack at accessing my NAS through ReadyCloud. The only way I can access the NAS currently is by clicking on the explorer button and selecting 'Network' then when accessing the drive, I am asked to login, which I used my ReadyCloud email address and password, this is what gives me the understanding that a hacker was able to access my files using these credentials.
How do you suggest I proceed moving forward to secure the device?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: ReadyNas RN2100 hacked
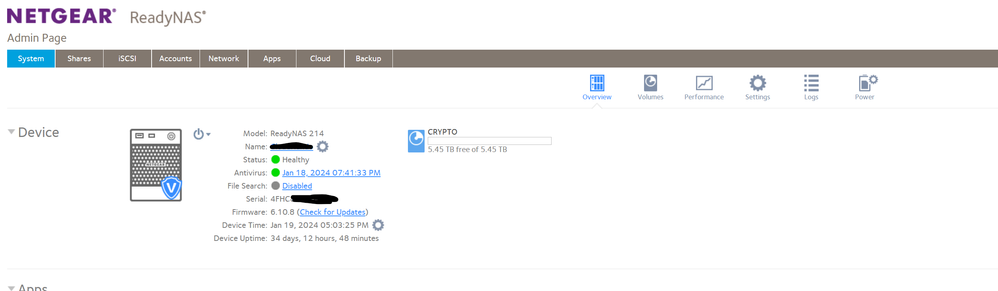
Thx for the screenshots. My replies so far assumed you had an RN2100 (as you said in your title). But you actually have an RN214, which is a completely different (and much newer) ReadyNAS platform.
RN2100:
RN214:
The RN214 could have been connected with ReadyCloud, as it is an OS-6 platform. That would have stopped last summer when Netgear took down the service.
- Do you recall when you received that email?
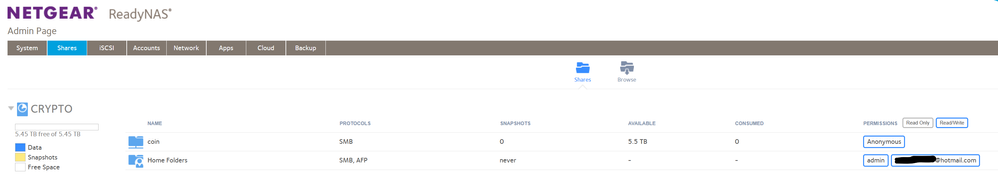
- Also, was your NAS originally named "Crypto", and did it have a share called "coin"? (I'm assuming not!)
@apopcontest wrote:
Not unless you had forwarded ports to the NAS to enable remote connections. Or alternatively if they compromised a PC you use to connect to the internet.
Is there a way to find this?
As far as port forwarding goes, you'd look for that in your router settings. Any port forwarding rules should be remted. While there,
- you should check to see if the uPNP service is enabled. If it is, then you should turn that off. It is a security risk, as it does allow any device on your home network to open up ports in your router's firewall.
- make sure the router firmware is up to date.
- If remote administration is enabled on your router, then I suggest disabling that.
- Also change the router's admin password.
What router model (and manufacturer) are you using?
You might also want to run malware scans on all your PCs. For instance, using the free download of malwarebytes.
Given the overall situation, it might be worth getting a subscription for a while, so you'd have real-time protection on your PCs.
Also, if you are using Microsoft accounts on your PCs (connected with Microsoft OneDrive), then you should also change the Microsoft passwords.
@apopcontest wrote:
How do you suggest I proceed moving forward to secure the device?
It's not just securing your NAS. You need to make sure your home network (and all devices on it) are secured.
In general, the NAS settings are all on the disks. So a factory default should bring the NAS back to its out-of-the-box state. So you'd need to set up the NAS from scratch. The ReadyNAS service (like all cloud services) would be disabled Since the service is down, you would not be able to join ReadyCloud (and shouldn't attempt it). Obviously set up different credentials.
After the initial factory default, you should update the firmware to 6.10.9 (which needs to be done manually)
Reinstalling plex is possible, but due to the deprecation of Debian 8 (the linux OS your NAS uses) earlier this year, you'd need to make some changes. This (rather long) discussion thread includes the info on what is needed.
Post 37 has the files you need to modify/add. Post 1 tells you where you need to put them.
Personally I run Plex on an always-on Windows PC, which has the media share(s) mapped to drive letters.
Risks here:
- Since you don't really know how the NAS was compromised, the same security vulnerability might remain (and might not be on your NAS at all).
- There is a very small chance that the hacker might have installed a root kit on the disks (which can be very difficult to remove).
On (2) you could just install new disks, and get rid of the old ones.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: ReadyNas RN2100 hacked
From the displayed space usage, they didn't encrypt your files, they deleted them (and the shares they were in), which is what they said they did. It's unlikely that they actually backed up your files, so I recommend you don't fall for the ransom demand -- you likely won't get anything back.
It sounds like you are saying you cannot access via the local admin account. That points to them using that account and then changing the password.
Are you running any remote access program on your PC (GoToMyPC, TeamViewer, or similar)? That can open you up to such an attack if your credentials for it are compromised and the admin password for the NAS is the default, too simple, or the same as your other compromised password.
It is possible that your email account is compromised. Once somebody has access to that, they can use password recovery to get your NAS password and probably a lot more. One way they can gain access there is if your security questions' answers are something that can be found on your social media. Since gaining access that way usually means resetting the password, you can usually tell it's happened if you had to do a password reset/recovery yourself and don't know why. That's how hackers have gained access to celebrities' accounts -- their answers are easily Googled.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: ReadyNas RN2100 hacked
Thx for the screenshots. My replies so far assumed you had an RN2100 (as you said in your title). But you actually have an RN214, which is a completely different (and much newer) ReadyNAS platform.
I apologise profusely, I think I was looking at my receipt to confirm the model number of the NAS and it says 2100 funnily enough, who would've thought it was an actual product as well.
The RN214 could have been connected with ReadyCloud, as it is an OS-6 platform. That would have stopped last summer when Netgear took down the service.
- Do you recall when you received that email?
- Also, was your NAS originally named "Crypto", and did it have a share called "coin"? (I'm assuming not!)
Are you asking about the 'threat email' to pay crypto? - It arrived sometime late last year and I remember opening it because it actually named my NAS device, I assumed they got the information due to a data breach and never checked my NAS because ... frankly it only had movies and TV shows and also I was swamped at the time. Never have I named it crypto, the hacker has clearly renamed them those names.
As far as port forwarding goes, you'd look for that in your router settings. Any port forwarding rules should be remted. While there,
- you should check to see if the uPNP service is enabled. If it is, then you should turn that off. It is a security risk, as it does allow any device on your home network to open up ports in your router's firewall.
- make sure the router firmware is up to date.
- If remote administration is enabled on your router, then I suggest disabling that.
- Also change the router's admin password.
I wasn't sure if I could see any port forwarding rules but I disabled a few things, I also disabled uPNP service, apparently my firmware is up to date and I also changed the router admin password. I also deleted a Virtual Server, hope I was meant to do that. I already have McAfee Virus protection subscription on my main laptop at home.
Also, if you are using Microsoft accounts on your PCs (connected with Microsoft OneDrive), then you should also change the Microsoft passwords.
Thanks, I already change my password annually, so time has come to change it again, so I will be doing so in due course.
In general, the NAS settings are all on the disks. So a factory default should bring the NAS back to its out-of-the-box state. So you'd need to set up the NAS from scratch. The ReadyNAS service (like all cloud services) would be disabled Since the service is down, you would not be able to join ReadyCloud (and shouldn't attempt it). Obviously set up different credentials.
Thank you, I guess I will dig up how to do a factory reset, I am hoping its just a matter of pressing a physical button on the back of the NAS.
Risks here:
- Since you don't really know how the NAS was compromised, the same security vulnerability might remain (and might not be on your NAS at all).
- There is a very small chance that the hacker might have installed a root kit on the disks (which can be very difficult to remove).
Do you think its possible that a hacker may have accessed my NAS through a username and password they found and attempted to access ReadyCloud? Or could it point to actually gaining access via my router?
Could wiping the disks also remove the root kit on the disks? According to the data being mentioned via ReadyCloud interface, I have a completely empty disk.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: ReadyNas RN2100 hacked
From the displayed space usage, they didn't encrypt your files, they deleted them (and the shares they were in), which is what they said they did. It's unlikely that they actually backed up your files, so I recommend you don't fall for the ransom demand -- you likely won't get anything back.
Thanks, I had no intention of paying up and because I got the email I ignored probably somewhere in October last year, I know for a fact that those files are likely long gone.
It sounds like you are saying you cannot access via the local admin account. That points to them using that account and then changing the password.
I can confirm that I can login via the local admin account including my ReadyCloud login credentials. I have changed that password immediately, although I don't know how useful that will be.
Are you running any remote access program on your PC (GoToMyPC, TeamViewer, or similar)? That can open you up to such an attack if your credentials for it are compromised and the admin password for the NAS is the default, too simple, or the same as your other compromised password.
No I do not have any remote access software on my PC.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: ReadyNas RN2100 hacked
@apopcontest wrote:
I also deleted a Virtual Server, hope I was meant to do that.
The Virtual Server is another name for port forwarding services, so it might have been the way the hacker accessed the NAS. Do you recall if that pointed to the NAS? Do you recall creating/configuring that server?
@apopcontest wrote:Do you think its possible that a hacker may have accessed my NAS through a username and password they found and attempted to access ReadyCloud?
It is possible though it's not clear how your ReadyCloud credentials would have been leaked. Mine weren't (I didn't receive any breach emails from Netgear), and if there was a breach we'd have seen a lot of posts here about it (as many other ReadyCloud users would have been hacked). Unfortunately you don't know the timing, so we can't tell if the ReadyCloud service was taken down before the files were deleted.
The virtual server you deleted is another possibility, and IMO more likely. But if you didn't set up that server, then the hacker must have found a way to do that remotely.
Nothing against McAfee, but I still do recommend downloading MalwareBytes and doing a scan of the PC with it. You can of course remove it later. None of these scanning tools catch everything, and when your network security has been breached it is a good practice to scan with more than one. You do need to be careful on which ones you use, because some tools you find when googling are actually scams. But MalwareBytes is reputable.
@apopcontest wrote:
Could wiping the disks also remove the root kit on the disks? According to the data being mentioned via ReadyCloud interface, I have a completely empty disk.
I don't think there is likely to be a root kit.
That said, they can be hard to remove. To be clear, you do not have a "completely empty disk". Your disks are formatted and there is OS partition and a swap partition used by the NAS on each of them. Plus disks with root kits appear to be empty but are not. If you can connect the disks one at a time to a Windows PC, you can scan them for rootkits. AVAST One is a free tool you can use for this.
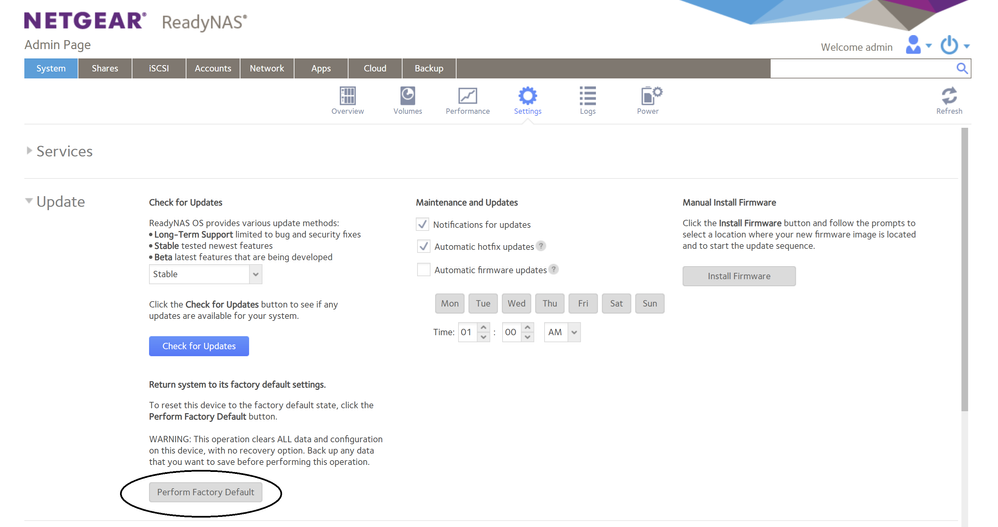
But I think you'd be ok if you just do the factory default from the web admin interface. Do this from System->Settings->Update
This will bring the NAS back to an out-of-the-box state - reformating the disks, and reinstalling the NAS software on them. You'd need to set up the NAS from scratch (recreating shares, etc). All accounts other than admin would be removed, including the ReadyCloud user account. The ReadyCloud service will also be disabled. Don't try to re-enable it - the service is taken down.
Use the normal admin account to set up the NAS (browsing to https://nas-ip-address/admin). The nas-ip-address is a placeholder, you'd need to use your real NAS IP address. You can find that in your router's attached device list. It can also be found on the NAS front panel. (Press the power button once if it is blank). The username is admin. The default password is password which of course should be changed to a strong password during setup.
I suggest downloading the hardware and software manual for your NAS
- https://www.downloads.netgear.com/files/GDC/READYNAS-100/ReadyNAS_%20OS6_Desktop_HM_EN.pdf
- https://www.downloads.netgear.com/files/GDC/READYNAS-100/READYNAS_OS_6_SM_EN.pdf
After setup, you should manually install 6.10.9 software (using the "install firmware" control on the screenshot above). 6.10.9 has some security updates.
You won't be able to re-install Plex on the NAS unless you make some other changes. You can install it on your PC, but keep the media on the NAS. That is my own approach. Either way, we can help with that after the NAS is rebuilt.