NETGEAR is aware of a growing number of phone and online scams. To learn how to stay safe click here.
Forum Discussion
cwebster
Oct 12, 2015Aspirant
How do I constrain multicast traffic to specific ports on GS716Tv3?
I can't find specific instructions to constrain multicast traffic on the GS715Tv3 smart switch. I need to force all multicast traffic to travel over a specific set of interfaces, or at least to s...
- Oct 22, 2015
To switch the the Mangement VLAN to 4.
Make sure you have 2 ports on the switch, one in VLAN1 one in VLAN4.
Set the system you are using to a static IP in the range of the switch and confirm access to the web config then change the "Management VLAN ID" to 4 and Apply. then switch the system you are using to the port or any port in VLAN 4 then you should have access, if not, wait about 60-90sec and try again becuase you may have STP on and it will block anything on the port for a bit unless its set to "Fast Link" Enabled.
Then under "IP Configuration" set the switches IP address to somthing in in IP range of VLAN4.
For Simplisicty sake, Untagged ports should only ever be in 1 VLAN at a time.
And instead of using the point and click, goto "Port PVID Configuration" and just set the VLANs there.
Set PVID and VLAN member the same for a port, based on what VLAN it needs to be in
And to confirm, do you have a cable going from switch to switch for each VLAN? You could cut down on cables and ports if you trunk/tag the ports to the next switch. then all 3 VLAN would only need 1 cable between each pair of switches, saving you atleast 4 ports on each switch.
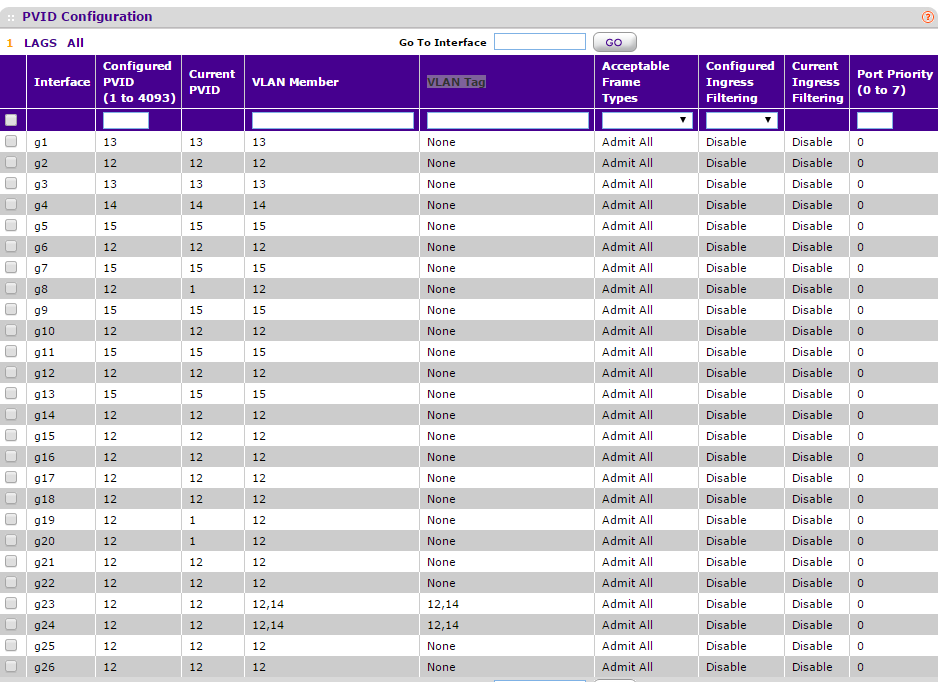
Just an example from my GS724T (ignore ports g8 and g19-20, thier Current PVID is becuase of somthing else you are not doing, LACP and Span/Monitoring):
All ports are setup for a single VLAN, my "Main LAN" is VLAN12, which the mangement VLAN is set for aswell, ports g23-24 are VLAN Trunks, they are set to tagg VLAN12 and 14 when that traffic goes out of those ports, then the switch on the other side reads the tagg and acts acordingly, this way I dont need 2 cables/ports for each of those.
DaneA
Oct 15, 2015NETGEAR Employee Retired
Hi cwebster,
As long as IGMP Snooping is configured correctly, there should be no issues with the multicast traffic crossing VLANs.
Let me also share this link I have found online. Hope this will help as reference.
Regards,
DaneA
NETGEAR Community Team
cwebster
Oct 15, 2015Aspirant
Thank you for that link Dane. The instructions were much more explanatory than those in the admin guide. I went through those same steps before but used a different querier address. I changed the querier address to that of the switch and configured vLAN 6 since that's the vLAN from which the multicast traffic originates and the one in which I wish to constrain the traffic.
I don't think it's working, though, because there are still no entries at all in IGMP Snooping Table. I expected to see the two players on vLAN 6. Shouldn't there be some MAC addresses in this list?
Should I have configured vLAN 1 instead of 6, even though 6 is the one I want to keep the traffic on?
Regards,
Cal Webster
- DaneAOct 18, 2015NETGEAR Employee Retired
Hi cwebster,
I think one way to check if multicast traffic is being constraint within VLAN 6 is to configure port mirroring and monitor it using Wireshark. Check this article about port mirroring.
In VLAN 6, you will need to set a source port/s and a destination port for port mirroring. The source port/s is/are the VLAN 6 port/s that you want to check if multicast is being constraint and the destination port is a one port in VLAN 6 where you will connect a PC/laptop that has Wireshark installed to monitor it. Here is the article as reference guide on how to configure port mirroring on the GS716Tv3.
Here is the link where to download Wireshark. Check this link I found online as reference how to analyze IPv4 multicast traffic. Also, you may search videos online (such as YouTube, etc.) or how-to documents about Wireshark.
Regards,
DaneA
NETGEAR Community Team
- NapsterbaterOct 21, 2015Apprentice
Multicast should'nt be leaving the VLAN not matter what, IGMP or not, just like Broadcast, unless you have a) A Multicast router, or b) You have a config issue with your VLANS. IGMP only keeps multicast from going to ports/devices that have not requested the multicast traffic.
How are the VLANS configured on the ports betweeen Switch1 and Switch9, then how are they configured between Switch2 and Switch 9?
Are you Tagging the Packets/are they setup for VLAN Trunking?
or
Are they set as Access Ports/untagged and just assgined to a single VLAN.
Also VLAN Names do not matter they are for your info only, VLAN Numbers will though.
I think you have made one big single Layer 2 "broadcast" domain.
- cwebsterOct 22, 2015Aspirant
Thank you for taking time to respond Napsterbater.
I have discovered the fundamental issue causing this problem and solved it - explanation below. First, I'll address your questions.
[quote]Multicast should'nt be leaving the VLAN not matter what, IGMP or not, just like Broadcast, unless you have a) A Multicast router, or b) You have a config issue with your VLANS. IGMP only keeps multicast from going to ports/devices that have not requested the multicast traffic.
[/quote]
Exactly my point. I expected that when I configured these VLANs they would be isolated unless I plugged in a router or otherwise configured the switch to forward packets elsewhere.
[quote]
How are the VLANS configured on the ports betweeen Switch1 and Switch9, then how are they configured between Switch2 and Switch 9?
[/quote]
Switches 1 through 8 are each connected via a cable plugged into a port in each's VLAN4 and premise wiring back to Switch 9 for software development.[quote]
Are you Tagging the Packets/are they setup for VLAN Trunking?
or
Are they set as Access Ports/untagged and just assgined to a single VLAN.
[/quote]
There is no tagging or VLAN trunking. All VLAN ports are simple, untagged access ports.[quote]
Also VLAN Names do not matter they are for your info only, VLAN Numbers will though.
[/quote]
This was always my understanding of VLAN ports too, but when things were not behaving as I expected I began to wonder if Netgear was performing some kind of voodoo behind this scenes.
[quote]I think you have made one big single Layer 2 "broadcast" domain.
[/quote]
You are almost exactly correct. The problem was that, even though I configured these ports into separate VLANs, the switch left the ports also members of the default VLAN 1. The Software Administration Manual does not mention that VLAN ports must be manually removed from VLAN 1. Nor does it specify that VLAN ports must be configured with a PVID before they will work as expected.
To resolve my issues:
1. Configured the member ports with a PVID:
Switching->VLAN->Advanced->Port PVID ConfigurationSelected ports in VLAN 6 by clicking the check-box
Typed "6" in "Configured PVID" field
Selected "Enable" in the "Configured Ingress Filtering" field
Clicked [Apply] button
Did the same for VLANs 4 and 5
2. Removed ports in my new VLANs from membership in VLAN 1
Switching->VLAN->Advanced->VLAN MembershipVLAN 1 is selected by default
Clicked to change port assignments from "Untagged" (U) to unselected (blank) for ports configured in VLANs 5 and 6.
Clicked [Apply] button
Left VLAN 4 alone (see below)
Unresolved Issues:
[Background]
Each of Switches 1 through 8 are part of a series of aircraft simulators. Switch 9 is on an engineering network. VLAN 5 is used for audio subsystems and VLAN 6 is used for other I/O subsystems (sensors, switches, relays, pumps, etc.) on each simulator. VLAN 4 is the VLAN that connects all these simulators together for research and software development on Switch 9.
1. I have as yet been unable to remove VLAN 4 ports from VLAN 1 without loosing management of the switches. Switch management is done from the engineering network on VLAN 4. I've tried changing the "Management VLAN ID" to 4 then removing them from VLAN 1 but I loose access and have to reset to factory defaults and start over.
2. I still don't see any evidence on the switch that IGMP Snooping is actually working. As I indicated in an earlier post, there is nothing in the IGMP Snooping Table after configuring IGMP Snooping and the IGMP Snooping Querier. There have been multiple sessions where multicast traffic has occurred since I first configured it so I'd expect something to show up here.
I'm fairly certain that it has had an impact on the flow of multicast traffic because, prior to discovering the solution above, configuring IGMP Snooping did seem to resolve half of the cross-talk issues.
I'll be capturing traffic on VLAN 6 (I/O Subsystems) of one of these simulators to analyze the traffic over the next few weeks in an effort to understand how this switch feature actually affects the flow of multicast, broadcast, and unicast packets.
Thanks again for responding.
Best Regards,
Cal Webster - NapsterbaterOct 22, 2015Apprentice
To switch the the Mangement VLAN to 4.
Make sure you have 2 ports on the switch, one in VLAN1 one in VLAN4.
Set the system you are using to a static IP in the range of the switch and confirm access to the web config then change the "Management VLAN ID" to 4 and Apply. then switch the system you are using to the port or any port in VLAN 4 then you should have access, if not, wait about 60-90sec and try again becuase you may have STP on and it will block anything on the port for a bit unless its set to "Fast Link" Enabled.
Then under "IP Configuration" set the switches IP address to somthing in in IP range of VLAN4.
For Simplisicty sake, Untagged ports should only ever be in 1 VLAN at a time.
And instead of using the point and click, goto "Port PVID Configuration" and just set the VLANs there.
Set PVID and VLAN member the same for a port, based on what VLAN it needs to be in
And to confirm, do you have a cable going from switch to switch for each VLAN? You could cut down on cables and ports if you trunk/tag the ports to the next switch. then all 3 VLAN would only need 1 cable between each pair of switches, saving you atleast 4 ports on each switch.
Just an example from my GS724T (ignore ports g8 and g19-20, thier Current PVID is becuase of somthing else you are not doing, LACP and Span/Monitoring):
All ports are setup for a single VLAN, my "Main LAN" is VLAN12, which the mangement VLAN is set for aswell, ports g23-24 are VLAN Trunks, they are set to tagg VLAN12 and 14 when that traffic goes out of those ports, then the switch on the other side reads the tagg and acts acordingly, this way I dont need 2 cables/ports for each of those.
- cwebsterOct 23, 2015Aspirant
Thank you again Napsterbater!
There were several "spare" ports already in VLAN 1 so on the "Port PVID Configuration" page I changed "Configured PVID" and "VLAN Member" to 4 (and only 4) and set "Configured Ingress Filtering" to Enable on one of them then clicked [Apply]. I was plugged into a VLAN 1 port at the time. Then I Went to System->IP Configuration, changed "Management VLAN ID" to 4, and clicked [Apply]. Of course I lost the connection until I plugged into the VLAN 4 only port. Then I went back to "Switching->VLAN->Advanced->Port PVID Configuration" and changed the original VLAN 4 ports, which were also VLAN 1 members, setting "Configured PVID" and "VLAN Member" to 4 (and only 4) and set "Configured Ingress Filtering" to Enable. Now everything works as expected.
Before I was hopping between the VLAN Membership and Port PVID Configuration pages to try to accomplish the same thing. I didn't realize I could do everything on the Port PVID Configuration page.
[quote]
And to confirm, do you have a cable going from switch to switch for each VLAN? You could cut down on cables and ports if you trunk/tag the ports to the next switch. then all 3 VLAN would only need 1 cable between each pair of switches, saving you atleast 4 ports on each switch.
[/quote]
The only VLAN that is connected between simulators is VLAN 4. This VLAN is used for access to the host computers for distributing software updates and engineering. VLAN 5 and 6 are completely isolated within each simulator. The Audio and IO from one simulator should never communicate with the Audio or IO of the other. You might imagine the kind of confusion and chaos this could (did) cause.
[Sim 1 Host]----[sw1-vlan4]----| |
[Sim 1 Audio]---[sw1-vlan5] | s |
[Sim 1 IO]------[sw1-vlan6] | w |
[Sim 1 Host]----[sw1-vlan6] | i | ... | t |---[Devel Svr]
[Sim 8 Host]----[Sw8-vlan4]----| c |
[Sim 8 Audio]---[sw8-vlan5] | h |
[Sim 8 IO]------[sw8-vlan6] | |
[Sim 8 Host]----[sw8-vlan6] | 9 |Interesting way you're hauling traffic between switches. There is a similar setup here with non-Netgear switches. Traffic for the main VLANs are tagged and forwarded over a pair of GBIC ports over fiber to another wing of the building.
Thank you again for the help.
Cal Webster
Related Content
NETGEAR Academy

Boost your skills with the Netgear Academy - Get trained, certified and stay ahead with the latest Netgear technology!
Join Us!