NETGEAR is aware of a growing number of phone and online scams. To learn how to stay safe click here.
Forum Discussion
rusman
May 28, 2017Tutor
R9000 block ssl-vpn connection ( port 443)
Hi All, i have issue with connecting to SSL VPN on port 443, i have R9000 router, i use firmware v1.0.1.36 When i tryed to connect to my work with Cisco Anyconnect that use port 443 i get denied....
- Jun 02, 2017
Hi All,
Just to Update,
Reload the router and SSL VPN worked correctly.
May be was some issue with MTU like TheEther say...
Will continues to monitor if it will happen again will update.
Thanks for you all for trying to help.
Ruslan.
FURRYe38
May 28, 2017Guru - Experienced User
What is the ISP Modem and model?
Set up any Port Fowarding rules set up on the router?
Might disable any wan side protection features and test.
rusman
May 29, 2017Tutor
Hi,
thanks for reply.
ISP Modem is D-link ( bridge mode)
no Port Fowrading rules exist on the router.
R9000 don't have any option to disable protetion.
i think the algorith that R9000 use to recognize DDOS is incorrect.
Ruslan.
- rusmanMay 29, 2017Tutor
we can see on the packet capture that was take from the router,
R9000 Reset the connection after get response from remote peer 84.XXX.XXX.XXX
Source 31.XX.XXX.XXX
i think if i will restart the router everything wil work correctly...but i don't belive is such solutions.:)
few weeks ago everything worked correctly.
If need more info update me.
Thanks.
Ruslan.
- TheEtherMay 29, 2017Guru
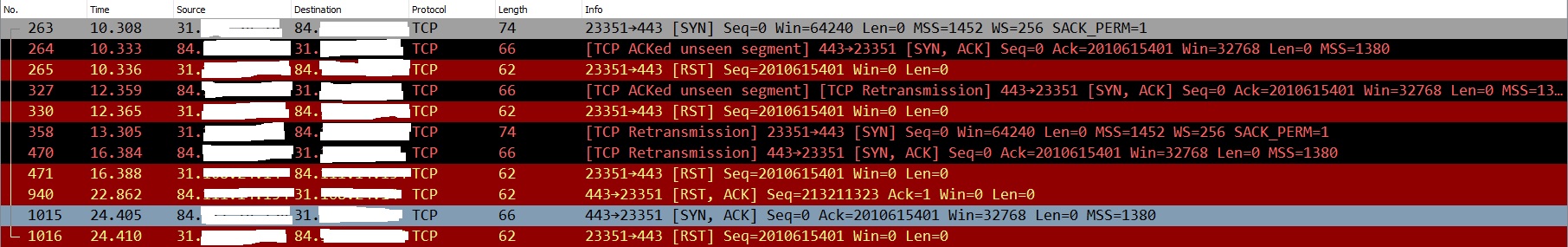
Oh boy, the Wireshark trace is a tale of dueling TCP RST exchanges.
You can see in frame 264 that the remote peer has replied with the wrong ACK number (2010615401) in response to the local host's TCP SYN request in frame 263. Wireshark flags this as ACKed unseen segment. The local host immediately sends a TCP RST (Reset) to tear down the connection in frame 265.
The remote peer retransmits frame 264 again as frame 327 in spite of the TCP RST in frame 265. It's almost as if the remote peer didn't receive the RST. The local host sends another RST in frame 330. The remote peer does this two more times in frame 470 and 1015. Each time the local host sends a RST in 471 and 1016.
Frame 940 is where we see a RST out of the blue from the remote peer. This RST doesn't seem to match up with any of the other frames. Frame 940 is probably what Netgear is flagging as a RST Scan.
Based on the above, it seems to me that the remote peer at 84.xxx.xxx.xxx is not behaving properly, although I guess we can't rule out the possibility that the router is totally mangling the traffic. It would be interesting to see simultaneous Wireshark captures from both sides of the router (i.e. WAN and LAN). This would provide insight into what the router is doing to the traffic pre- and post-NAT.
- rusmanMay 29, 2017Tutor
Hi The Ether,
thanks for answer,
of course i can provide LAN and WAN capture on the router,
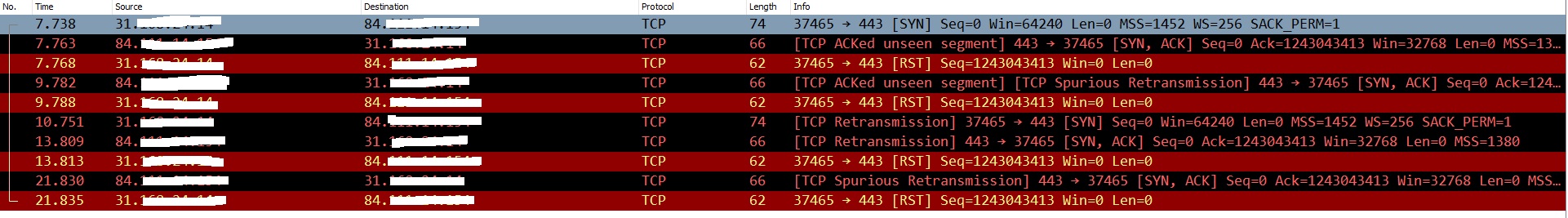
please see picture below:
WAN:
My Home IP:31.XXX.XXX.XXX
Remote Peer: 84.XX.XXX.XXX
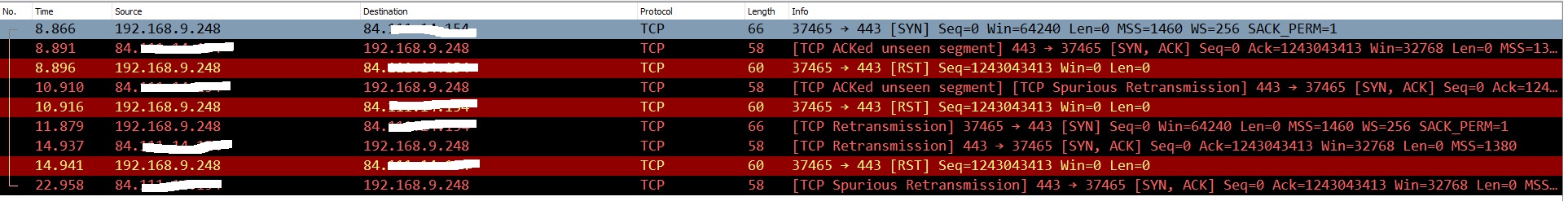
LAN:
PC:192.168.9.248
Remote Peer: 84.XXX.XXX.XXX
Of couse i have acces to remote peer it's Cisco ASA Firewall,
same pc 4G or modem directly connected i can succesfully conect to vpn.
i also added some files from R9000 ( basic_debug_log,console.log)
May be it will help.
Thanks for help,
Ruslan.