- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Re: FVS336Gv3 - L2TP/IPsec on Windows 10
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am in the process of testing an FVS336Gv3. I have a working site-to-site VPN with a Mikrotik device using PSK, and have another thread at the moment for instruction on how to upload cert/key for the S2S tunnel. I am now in the process of configuring an L2TP/IPsec VPN on the device. I notice there is L2TP configuration options, but did not see anywhere to specify the IPsec settings for the L2TP connection. Additionally, I have searched the forum and found an official Netgear employee post the following link as instructions on setting up the L2TP VPN:
https://drive.google.com/file/d/0B4PuVEYxkQ5oMXppNzVnT3lLUEU/view?pli=1
In the document, it says to specifically modify the WIndows registry to disable IPsec (!!!).
Is this a limitation of the device? Does it not support L2TP WITH IPsec? Because if so, that's fairly useless as a remote-access ("road warrior") style connection; not only are many of my clients using mobile devices/operating systems other than Windows (OSX and a few Linux), but that is also very insecure.
So is it possible to configure L2TP with IPsec? That is a pretty standard, well-supported VPN connection methodology, and you DO advertise the device as being capable of L2TP and IPsec.....
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So I finally got this (somewhat) figured out. I will make a mention that the official Netgear support personnel with whom I'd had an open case, wanted me to create a special login for him/her and allow the person to remotely connect to my device. In a business setting (like I am in), that is a VERY dubious requst to make, in my opinion. Of course, I could not get permission from my upper management to allow this to happen. But I digress.....
I figured I would share my configuration for those who might be interested. The configuration method is not what I would call "intuitive". The instructions below are working for me with the built-in L2TP/IPsec client in Windows 7, 8, and 10. Other clients may need different settings.
Be aware that I have measured AES throughput to be around 10mbps; pretty low, by today's standards, and certainly disappointing from a $200+ device (Cisco, Ubiquiti and Mikrotik offer devices that give far better VPN throughput rates, and cost half of this device). I wouldn't want to use this device with more than 4 or 5 concurrent users, and even that many might be a stretch.... Also, this guide is for PSK authentication; I haven't gotten around to configuring X509 auth.
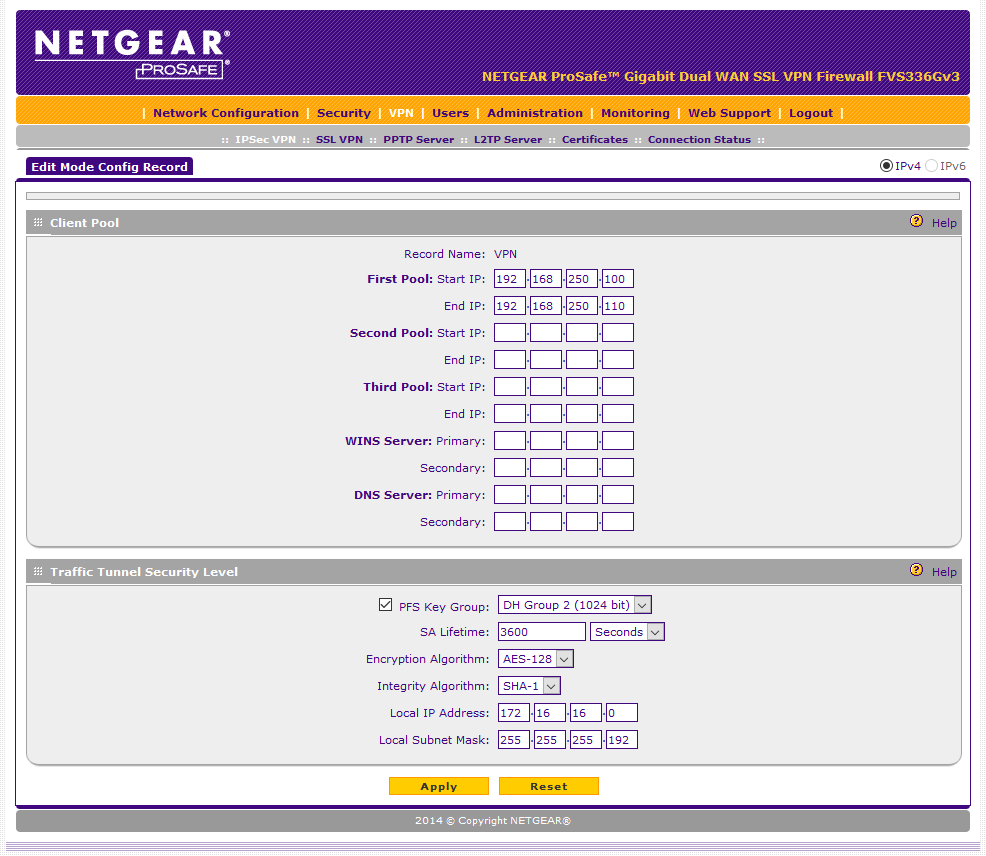
First, you need to create what is called a "Mode Config" under "VPN -> IPsec VPN -> Mode Config". These are actually the settings for the IPsec SA. I named mine "VPN":
The, create the IKE policy (in this case I named it "Remote"), and tell it to use the previous config. Make sure to set local and remote to FQDN, with the value of "fvs1_local.com" for Local and the IP 0.0.0.0 as the FQDN value for Remote (yes, it makes no sense. You would think that 0.0.0.0 should have Identifier Type "IP Address" selected, not "FQDN". Welcome to Netgear :). Also, make sure to select 3DES as the cipher on this screen; that is a limitation of the built-in Windows client - it must use 3DES for IKE. 3DES is used only for the IKE exchange messages; the actual IP traffic is encryped with the settings shown on the previous screen. I have noticed that even if you selected "AES-128" on the previous screen, Windows will upgrade to using AES-256. Not sure if that's a "feature" of Windows or of the Netgear device. :
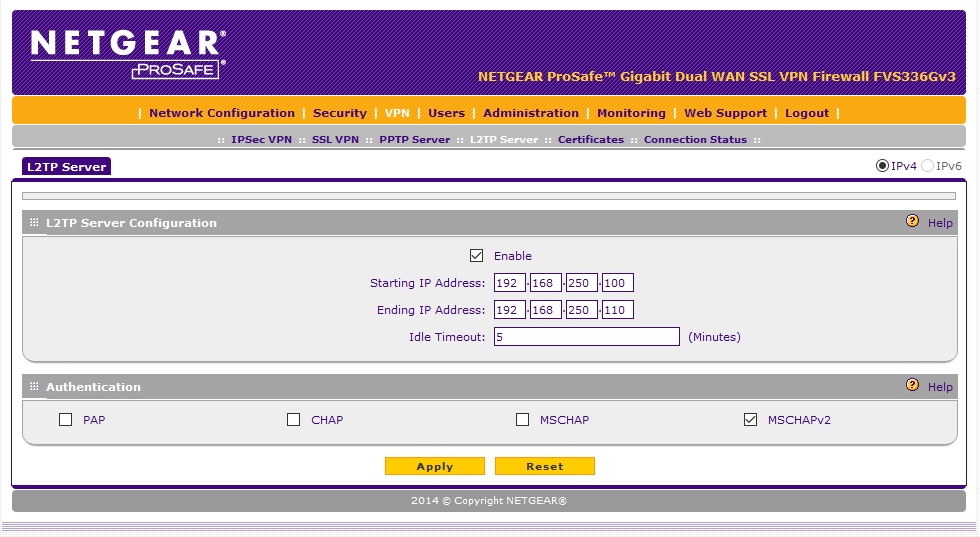
Set the L2TP server settings. Make sure to choose an IP range that is NOT within the same subnet as the Netgear's LAN. I am not sure why you are required to specify an IP range both here AND on the "Mode Config" page, and I am not sure how they interact. I just made them the same.:
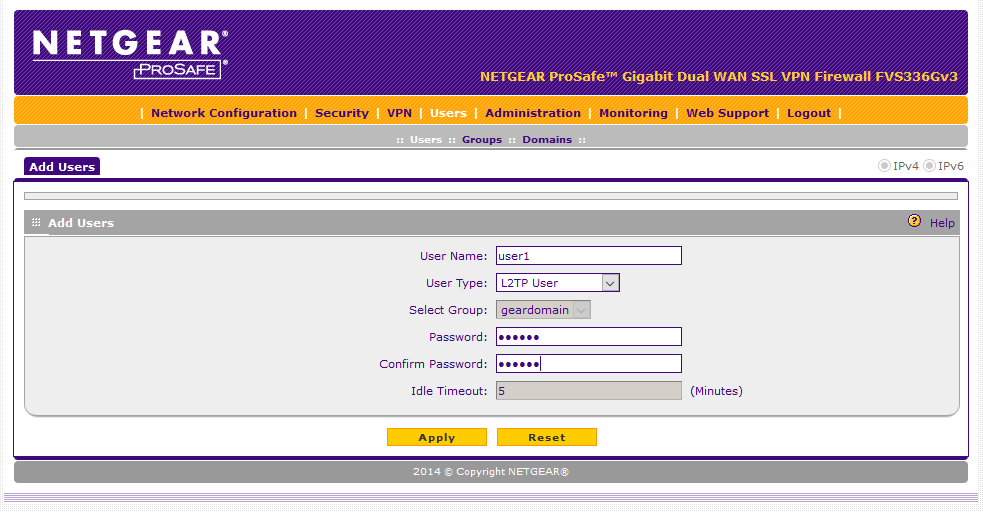
Add a user, specifying "L2TP User":
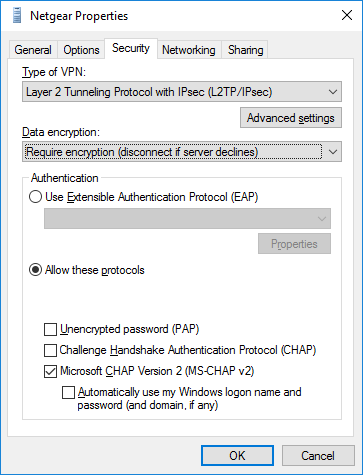
Finally, create a new VPN connection on Windows of type "L2TP/IPsec". By default, I had to click "Advanced Settings" and specify Pre-Shared Secret authentication; by default it is set to use certs. Make sure to use either the Netgear's WAN IP or a DNS record created for it, as the "IP Address or Hostname" field on the "General" tab:
At this point you should be able to connect. I noticed an MTU issues that was causing some websites not to load. From the Windows command line (as an Administrator), I had to run the following:
netsh int ipv4 set subinterface "Netgear" mtu=1300 store=persistent
Where "Netgear" is the name you gave to the new VPN connection in Windows. Typically, this setting should be done on the VPN server itself, rather than having to be done on each client. Unfortunately, Netgear chose not give you an option to set the tunnel MTU, and evidently left it at its default of (presumably) 1500. There is perhaps an option available to set this from the Netgear's command line; of course, there is no SSH access remotely, so command line access must be done with a DB-9 null-modem cable physically at the device.
All Replies
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: FVS336Gv3 - L2TP/IPsec on Windows 10
Hello train_wreck,
I have also answered the other thread you posted. Regarding this one, the official L2TP configuration is on our KB site (click here). This document that you have maybe a workaround for a different issue.
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: FVS336Gv3 - L2TP/IPsec?
OK, I followed that guide exactly. The connection is failing, with the following log output:
Fri Mar 18 12:26:18 2016 (GMT -0500): [FVS336GV3] [IKE] ERROR: Could not find configuration for 172.16.16.10[500] Fri Mar 18 12:26:17 2016 (GMT -0500): [FVS336GV3] [IKE] ERROR: Could not find configuration for 172.16.16.10[500] Fri Mar 18 12:26:16 2016 (GMT -0500): [FVS336GV3] [IKE] ERROR: Could not find configuration for 172.16.16.10[500]
172.16.16.10 is the IP of my Win7 machine. The Netgear's WAN is 172.16.16.44.
The guide you posted makes no mention of IKE... should there be an IKE or IPsec policy for connecting L2TP clients? (I would think so, as the IPsec provides encryption for the VPN traffic)
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: FVS336Gv3 - L2TP/IPsec?
Hello train_wreck,
I would suggest contacting our support team for this one. They will be able to walk you through the process and help you with the configuration.
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: FVS336Gv3 - L2TP/IPsec?
Hi train_wreck,
On behalf of JohnRo, I apologize for the inconvenience. There were new changes implemented in the NETGEAR website. Here is the correct link where you can open an online case with NETGEAR Support. Kindly state your concern and attach the logs from your FVS336Gv3 for it to be analyzed by the engineering team.
Regards,
DaneA
NETGEAR Community Team
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: FVS336Gv3 - L2TP/IPsec?
No problem DaneA. I setup a support ticket with them.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So I finally got this (somewhat) figured out. I will make a mention that the official Netgear support personnel with whom I'd had an open case, wanted me to create a special login for him/her and allow the person to remotely connect to my device. In a business setting (like I am in), that is a VERY dubious requst to make, in my opinion. Of course, I could not get permission from my upper management to allow this to happen. But I digress.....
I figured I would share my configuration for those who might be interested. The configuration method is not what I would call "intuitive". The instructions below are working for me with the built-in L2TP/IPsec client in Windows 7, 8, and 10. Other clients may need different settings.
Be aware that I have measured AES throughput to be around 10mbps; pretty low, by today's standards, and certainly disappointing from a $200+ device (Cisco, Ubiquiti and Mikrotik offer devices that give far better VPN throughput rates, and cost half of this device). I wouldn't want to use this device with more than 4 or 5 concurrent users, and even that many might be a stretch.... Also, this guide is for PSK authentication; I haven't gotten around to configuring X509 auth.
First, you need to create what is called a "Mode Config" under "VPN -> IPsec VPN -> Mode Config". These are actually the settings for the IPsec SA. I named mine "VPN":
The, create the IKE policy (in this case I named it "Remote"), and tell it to use the previous config. Make sure to set local and remote to FQDN, with the value of "fvs1_local.com" for Local and the IP 0.0.0.0 as the FQDN value for Remote (yes, it makes no sense. You would think that 0.0.0.0 should have Identifier Type "IP Address" selected, not "FQDN". Welcome to Netgear :). Also, make sure to select 3DES as the cipher on this screen; that is a limitation of the built-in Windows client - it must use 3DES for IKE. 3DES is used only for the IKE exchange messages; the actual IP traffic is encryped with the settings shown on the previous screen. I have noticed that even if you selected "AES-128" on the previous screen, Windows will upgrade to using AES-256. Not sure if that's a "feature" of Windows or of the Netgear device. :
Set the L2TP server settings. Make sure to choose an IP range that is NOT within the same subnet as the Netgear's LAN. I am not sure why you are required to specify an IP range both here AND on the "Mode Config" page, and I am not sure how they interact. I just made them the same.:
Add a user, specifying "L2TP User":
Finally, create a new VPN connection on Windows of type "L2TP/IPsec". By default, I had to click "Advanced Settings" and specify Pre-Shared Secret authentication; by default it is set to use certs. Make sure to use either the Netgear's WAN IP or a DNS record created for it, as the "IP Address or Hostname" field on the "General" tab:
At this point you should be able to connect. I noticed an MTU issues that was causing some websites not to load. From the Windows command line (as an Administrator), I had to run the following:
netsh int ipv4 set subinterface "Netgear" mtu=1300 store=persistent
Where "Netgear" is the name you gave to the new VPN connection in Windows. Typically, this setting should be done on the VPN server itself, rather than having to be done on each client. Unfortunately, Netgear chose not give you an option to set the tunnel MTU, and evidently left it at its default of (presumably) 1500. There is perhaps an option available to set this from the Netgear's command line; of course, there is no SSH access remotely, so command line access must be done with a DB-9 null-modem cable physically at the device.