- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Re: M4300 SFP Port Trunking Issues
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
I recently purchased 2 new M4300 and form a stack. After stacking the SW, I started to setup the switch as normal, the management VLAN, IP, the rest of vlan, subnet of those VLAN. Since it is a core SW for us, I didn't assign ports to each vlan except the defult vlan. Instead, I setup trunking on port 2- 8 (SFP), and was planning to connect these ports the other layer 2 sw in each floor.
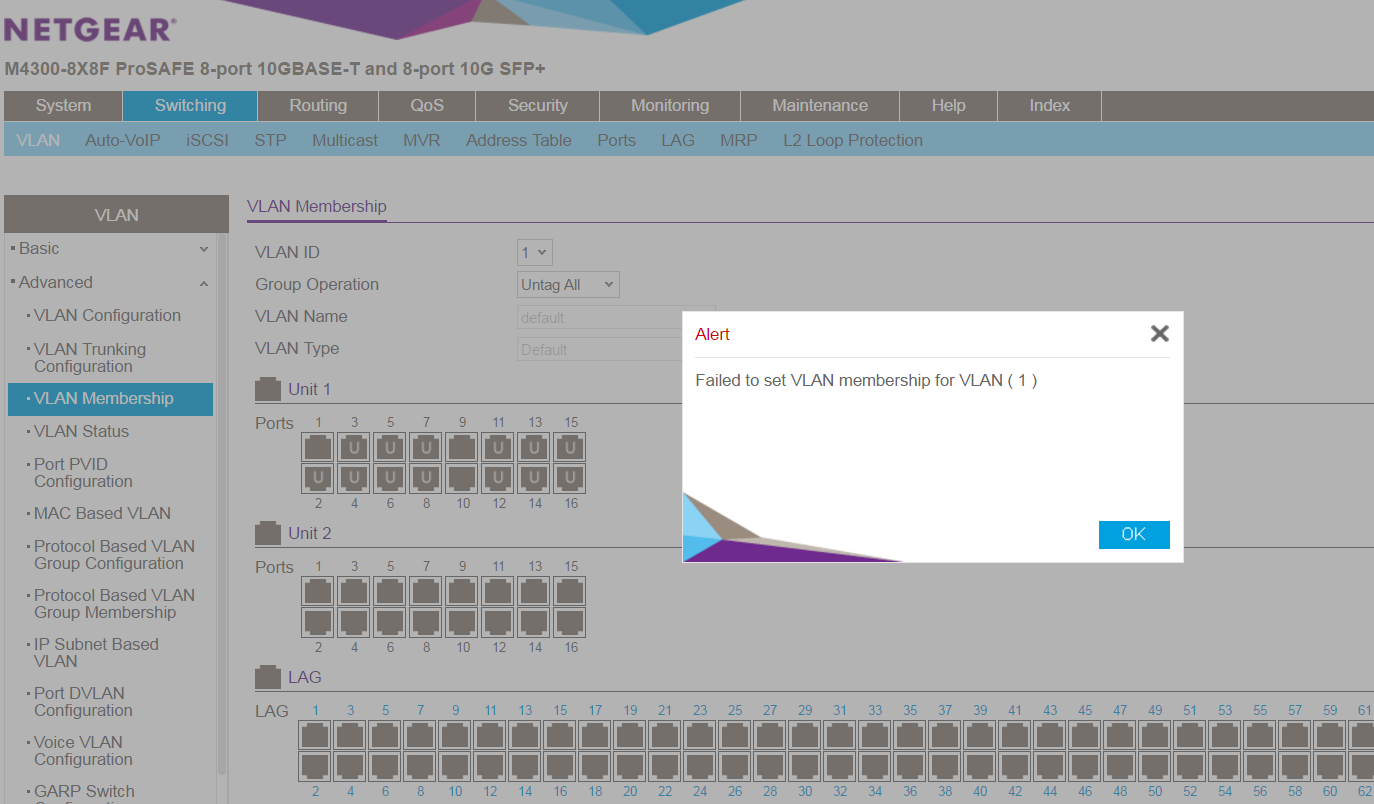
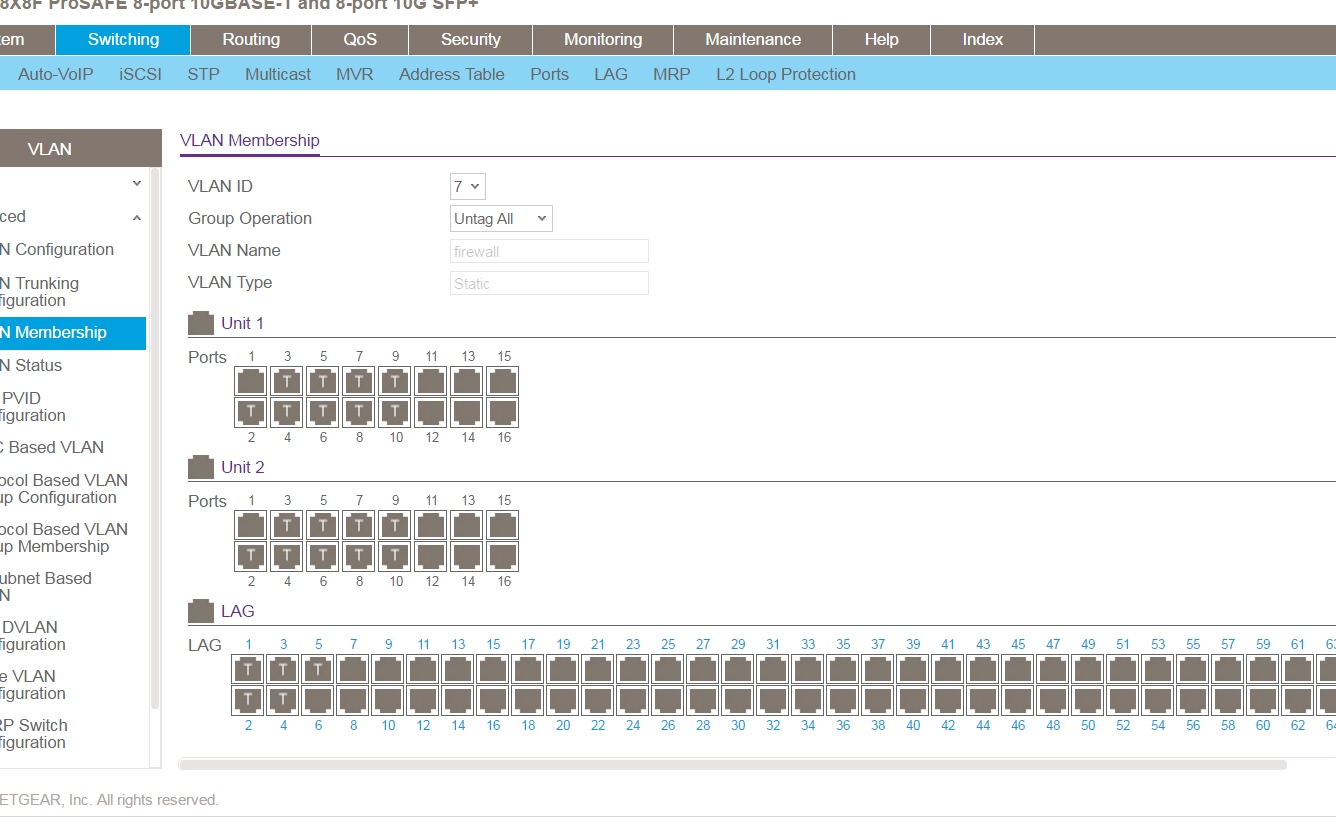
after I finished the setup on trunking, I found that the port were labeled as "U" which means it is an untag port rather than "T" and it was not expected! So I had a test on port 9 and 10 (which is not SFP port), and found that it was normal marked with "T" label. I tried to click on the SFP port and make it "T", but when I applied the setting, the label was changed back to "U". So, Could anyone give me a hints? Thank you.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Kelvin,
It's a good news that the failover problem resolved.![]()
Let's carry on the VRRP scenario.
I have checked the maintenance file just you sent to us.
1) Congratulation!The address (192.168.100.2 ) is the virtual IP address of VRRP on Firewall.
Because this IP have same prefix mac-address header just like (00:00:5E:00:xx:xx).
It's the standard of VRRP for mac-address behavior.
2) Good finding! The "Link state detection” is very useful for VRRP status.
So we need to set the IP for heartbeat on each Firewall that could monitor VRRP all the time.
But 192.168.100.1 is not the heartbeat address for Firewall that is VLAN interface on M4300-Stack.
So Could you set an IP address on Firewall A and B that is not VRRP protocol.
Such as:
192.168.100.10 /24 on Firewall A.
192.168.100.20 /24 on Firewall B.
Then,
Set Link state detection IP address to 192.168.100.20 on Firewall A.
Set Link state detection IP address to 192.168.100.10 on Firewall B.
That will make Firewall detect each other with this configuration.
3) Could you share me the configuration page or command on your Firewall about LAG/Port/IP address/VRRP configuration?
The private message is RECOMMENDED.
I'm not very professional on Firewall of other company.
Just want to help analyze.![]()
Look forward to your reply.
Regards,
Daniel.
All Replies
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Hi KelvinFu
Welcome the community!
We are going to help you. At first glance without other indications from you, it seems you have a conflict between the Access Port / Trunk Port - Native VLAN configuration, and the more 802.1Q-like Untagged / Tagged Ports - PVID configuration. Our M4300 Managed switch series offers both ways, either in Web interface (GUI) and in CLI (local console, Telnet or SSH). You may want to revisit your configuration on the other side: did you configure these ports 1 to 8 in Access port mode before? they should be Trunk ports instead.
Could you copy and paste your running config file portion with VLAN database and VLAN port membership? This will offer fastest way to resolution to all of us in the Community. You are right, that in Port general mode, your trunk ports should show T since they are all supposed to carry tagged VLAN traffic.
Thanks in advance,
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Hi Laurent,
Thx for the reply, since i'm off from work, I will upload the file on Moday. before I have the runnnig for you, I would like to share more info to you first.
We have a HA design by enabling VRRP in Firewall and stacking in Layer 3 Core SW, also we have Layer 2 access SW in each floor and connect it to both Core stack member.
In this stage, we are not starting on the configurion of Layer 2, instead we focus on Layer 3.
We have totally 7 VLAN in core sw
1 - default - 192.168.200.0/24 - 192.168.200.1 as vlan interface (I assumed this is the native vlan as same as cisco? so i don't have check on it since i'm not very familiar with the CLI)
2 - vlan 2 - 192.168.0.0/24 - 192.168.0.1 as vlan interface
3 - vlan 3 - 192.168.1.0/24 - 192.168.1.1 as vlan interface
4 - vlan 4 - 192.168.2.0/23 - 192.168.2.1 as vlan interface
5 - vlan 5 - 192.168.4.0/23 - 192.168.4.1 as vlan interface
6 - vlan 6 - 192.168.6.0/24 - 192.168.6.1 as vlan interface
7 - vlan 7 - 192.168.100.0/30 - 192.168.100.1 as vlan interface (connect to VRRP firewall group, port 9 to firewall A, and port 10 to firewall B)
I then set port 2-10 as a trunking port by using CLI, port 1 in both units are connected by stacking cable. After the setting was finished, I verified the ports on WebGUI to make sure it was being trunked, but with no luck, port 2-8 was label as "U" while 9-10 are nromal to be marked as "T", the only difference between 9-10 and 2-8 is that 9-10 are ethernet port while 2-8 are SFP port. When I saw this abnormal thing, I manually marked the port 2-8 to "T" and clicked apply. Then....it wasn't applied as you knew and changed back to "U". The switches are brand new, so I didn't have another setting before this, also I had reset the switch to factory default before I made those change. So I don't think I did have configure on those ports.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Unit 1
!Current Configuration:
!
!System Description "M4300-8X8F ProSAFE 8-port 10GBASE-T and 8-port 10G SFP+, 12.0.2.6, 1.0.0.7"
!System Software Version "12.0.2.6"
!System Up Time "2 days 22 hrs 7 mins 47 secs"
!Additional Packages QOS,Multicast,IPv6,IPv6 Management,Stacking,Routing
!Current SNTP Synchronized Time: SNTP Last Attempt Status Is Not Successful
!
hostname "CoreSW-1"
set gvrp adminmode
enable password f6f136b1793bd7a9da7f3edfac514c690156a6088107f654742867e597514667e20688da5f2057335dc3da47d4d669ad616f9d416d4a700979e4146ee8f43119 encrypted
serviceport protocol none
serviceport ip 10.251.251.251 255.255.255.0 0.0.0.0
vlan database
vlan 2-7
vlan name 2 "Server"
vlan name 3 "CCTV"
vlan name 4 "Operation"
vlan name 5 "Academic"
vlan name 6 "Public"
vlan name 7 "RoutingZone"
vlan routing 1 1
vlan routing 2 2
vlan routing 3 3
vlan routing 4 4
vlan routing 5 5
vlan routing 6 6
vlan routing 7 7
vlan association subnet 192.168.0.0 255.255.255.0 2
vlan association subnet 192.168.1.0 255.255.255.0 3
vlan association subnet 192.168.2.0 255.255.254.0 4
vlan association subnet 192.168.4.0 255.255.254.0 5
vlan association subnet 192.168.6.0 255.255.255.0 6
vlan association subnet 192.168.100.0 255.255.255.0 7
vlan association subnet 192.168.200.0 255.255.255.0 1
exit
configure
stack
member 1 6
member 2 6
exit
switch 1 priority 1
switch 2 priority 2
slot 1/0 6
set slot power 1/0
no set slot disable 1/0
slot 2/0 6
set slot power 2/0
no set slot disable 2/0
username "admin" password 0cc141558cdf3fe2475b8528c2d8d41e00d1351e56d2f2984581aac7521798d7d1ad50eebe599947ee39125507c38a81f3ac18f4f7f2c9a0608cd2c56607cbf1 level 15 encrypted
line console
exit
line telnet
exit
line ssh
exit
snmp-server sysname "CoreSW-1"
!
ip access-list Public-ACL
deny ip 192.168.6.0 0.0.0.255 192.168.0.0 0.0.0.255
deny ip 192.168.6.0 0.0.0.255 192.168.1.0 0.0.0.255
deny ip 192.168.6.0 0.0.0.255 192.168.2.0 0.0.1.255
deny ip 192.168.6.0 0.0.0.255 192.168.4.0 0.0.1.255
permit ip any any
exit
interface 1/0/1
vlan participation auto 1
exit
interface 1/0/2
bandwidth 10000000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
routing
ip mtu 1500
exit
interface 1/0/3
bandwidth 10000000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
vlan tagging 1
routing
ip mtu 1500
exit
interface 1/0/4
bandwidth 1000000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
routing
ip mtu 1500
exit
interface 1/0/5
bandwidth 10000000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
routing
ip mtu 1500
exit
interface 1/0/6
bandwidth 100000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
routing
ip mtu 1500
exit
interface 1/0/7
bandwidth 10000000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
routing
ip mtu 1500
exit
interface 1/0/8
bandwidth 100000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
routing
ip mtu 1500
exit
interface 1/0/9
switchport mode access
switchport access vlan 7
switchport trunk allowed vlan 1-7
vlan participation auto 1
vlan tagging 3
exit
interface 1/0/10
switchport mode access
switchport access vlan 7
switchport trunk allowed vlan 1-7
vlan participation auto 1
exit
interface 1/0/11
switchport mode access
vlan pvid 7
vlan participation auto 1
vlan participation include 7
exit
interface 1/0/12
switchport mode access
vlan pvid 7
vlan participation auto 1
vlan participation include 7
exit
interface 1/0/13
switchport mode access
vlan pvid 7
vlan participation auto 1
vlan participation include 7
exit
interface 1/0/14
switchport mode access
vlan pvid 7
vlan participation auto 1
vlan participation include 7
exit
interface 1/0/15
switchport mode access
vlan participation auto 1
exit
interface 1/0/16
switchport mode access
vlan participation auto 1
exit
interface 2/0/1
vlan participation auto 1
exit
interface 2/0/2
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/3
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/4
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/5
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/6
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/7
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/8
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/9
vlan participation auto 1
exit
interface 2/0/10
vlan participation auto 1
exit
interface 2/0/11
vlan participation auto 1
exit
interface 2/0/12
vlan participation auto 1
exit
interface 2/0/13
vlan participation auto 1
exit
interface 2/0/14
vlan participation auto 1
exit
interface 2/0/15
vlan participation auto 1
exit
interface 2/0/16
vlan participation auto 1
exit
interface lag 1
vlan participation auto 1
exit
interface lag 2
vlan participation auto 1
exit
interface lag 3
vlan participation auto 1
exit
interface lag 4
vlan participation auto 1
exit
interface lag 5
vlan participation auto 1
exit
interface lag 6
vlan participation auto 1
exit
interface lag 7
vlan participation auto 1
exit
interface lag 8
vlan participation auto 1
exit
interface lag 9
vlan participation auto 1
exit
interface lag 10
vlan participation auto 1
exit
interface lag 11
vlan participation auto 1
exit
interface lag 12
vlan participation auto 1
exit
interface lag 13
vlan participation auto 1
exit
interface lag 14
vlan participation auto 1
exit
interface lag 15
vlan participation auto 1
exit
interface lag 16
vlan participation auto 1
exit
interface lag 17
vlan participation auto 1
exit
interface lag 18
vlan participation auto 1
exit
interface lag 19
vlan participation auto 1
exit
interface lag 20
vlan participation auto 1
exit
interface lag 21
vlan participation auto 1
exit
interface lag 22
vlan participation auto 1
exit
interface lag 23
vlan participation auto 1
exit
interface lag 24
vlan participation auto 1
exit
interface lag 25
vlan participation auto 1
exit
interface lag 26
vlan participation auto 1
exit
interface lag 27
vlan participation auto 1
exit
interface lag 28
vlan participation auto 1
exit
interface lag 29
vlan participation auto 1
exit
interface lag 30
vlan participation auto 1
exit
interface lag 31
vlan participation auto 1
exit
interface lag 32
vlan participation auto 1
exit
interface lag 33
vlan participation auto 1
exit
interface lag 34
vlan participation auto 1
exit
interface lag 35
vlan participation auto 1
exit
interface lag 36
vlan participation auto 1
exit
interface lag 37
vlan participation auto 1
exit
interface lag 38
vlan participation auto 1
exit
interface lag 39
vlan participation auto 1
exit
interface lag 40
vlan participation auto 1
exit
interface lag 41
vlan participation auto 1
exit
interface lag 42
vlan participation auto 1
exit
interface lag 43
vlan participation auto 1
exit
interface lag 44
vlan participation auto 1
exit
interface lag 45
vlan participation auto 1
exit
interface lag 46
vlan participation auto 1
exit
interface lag 47
vlan participation auto 1
exit
interface lag 48
vlan participation auto 1
exit
interface lag 49
vlan participation auto 1
exit
interface lag 50
vlan participation auto 1
exit
interface lag 51
vlan participation auto 1
exit
interface lag 52
vlan participation auto 1
exit
interface lag 53
vlan participation auto 1
exit
interface lag 54
vlan participation auto 1
exit
interface lag 55
vlan participation auto 1
exit
interface lag 56
vlan participation auto 1
exit
interface lag 57
vlan participation auto 1
exit
interface lag 58
vlan participation auto 1
exit
interface lag 59
vlan participation auto 1
exit
interface lag 60
vlan participation auto 1
exit
interface lag 61
vlan participation auto 1
exit
interface lag 62
vlan participation auto 1
exit
interface lag 63
vlan participation auto 1
exit
interface lag 64
vlan participation auto 1
exit
interface lag 65
vlan participation auto 1
exit
interface lag 66
vlan participation auto 1
exit
interface lag 67
vlan participation auto 1
exit
interface lag 68
vlan participation auto 1
exit
interface lag 69
vlan participation auto 1
exit
interface lag 70
vlan participation auto 1
exit
interface lag 71
vlan participation auto 1
exit
interface lag 72
vlan participation auto 1
exit
interface lag 73
vlan participation auto 1
exit
interface lag 74
vlan participation auto 1
exit
interface lag 75
vlan participation auto 1
exit
interface lag 76
vlan participation auto 1
exit
interface lag 77
vlan participation auto 1
exit
interface lag 78
vlan participation auto 1
exit
interface lag 79
vlan participation auto 1
exit
interface lag 80
vlan participation auto 1
exit
interface lag 81
vlan participation auto 1
exit
interface lag 82
vlan participation auto 1
exit
interface lag 83
vlan participation auto 1
exit
interface lag 84
vlan participation auto 1
exit
interface lag 85
vlan participation auto 1
exit
interface lag 86
vlan participation auto 1
exit
interface lag 87
vlan participation auto 1
exit
interface lag 88
vlan participation auto 1
exit
interface lag 89
vlan participation auto 1
exit
interface lag 90
vlan participation auto 1
exit
interface lag 91
vlan participation auto 1
exit
interface lag 92
vlan participation auto 1
exit
interface lag 93
vlan participation auto 1
exit
interface lag 94
vlan participation auto 1
exit
interface lag 95
vlan participation auto 1
exit
interface lag 96
vlan participation auto 1
exit
interface lag 97
vlan participation auto 1
exit
interface lag 98
vlan participation auto 1
exit
interface lag 99
vlan participation auto 1
exit
interface lag 100
vlan participation auto 1
exit
interface lag 101
vlan participation auto 1
exit
interface lag 102
vlan participation auto 1
exit
interface lag 103
vlan participation auto 1
exit
interface lag 104
vlan participation auto 1
exit
interface lag 105
vlan participation auto 1
exit
interface lag 106
vlan participation auto 1
exit
interface lag 107
vlan participation auto 1
exit
interface lag 108
vlan participation auto 1
exit
interface lag 109
vlan participation auto 1
exit
interface lag 110
vlan participation auto 1
exit
interface lag 111
vlan participation auto 1
exit
interface lag 112
vlan participation auto 1
exit
interface lag 113
vlan participation auto 1
exit
interface lag 114
vlan participation auto 1
exit
interface lag 115
vlan participation auto 1
exit
interface lag 116
vlan participation auto 1
exit
interface lag 117
vlan participation auto 1
exit
interface lag 118
vlan participation auto 1
exit
interface lag 119
vlan participation auto 1
exit
interface lag 120
vlan participation auto 1
exit
interface lag 121
vlan participation auto 1
exit
interface lag 122
vlan participation auto 1
exit
interface lag 123
vlan participation auto 1
exit
interface lag 124
vlan participation auto 1
exit
interface lag 125
vlan participation auto 1
exit
interface lag 126
vlan participation auto 1
exit
interface lag 127
vlan participation auto 1
exit
interface lag 128
vlan participation auto 1
exit
interface vlan 1
routing
ip address 192.168.200.1 255.255.255.0
exit
interface vlan 2
routing
ip address 192.168.0.1 255.255.255.0
exit
interface vlan 3
routing
ip address 192.168.1.1 255.255.255.0
exit
interface vlan 4
routing
ip address 192.168.2.1 255.255.254.0
exit
interface vlan 5
routing
ip address 192.168.4.1 255.255.254.0
exit
interface vlan 6
routing
ip address 192.168.6.1 255.255.255.0
exit
interface vlan 7
routing
ip address 192.168.100.1 255.255.255.252
exit
ip management vlan 1 192.168.200.1 255.255.255.0
router rip
exit
router ospf
exit
ipv6 router ospf
exit
ip route 0.0.0.0 0.0.0.0 192.168.100.2
exit
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Unit 2
!Current Configuration:
!
!System Description "M4300-8X8F ProSAFE 8-port 10GBASE-T and 8-port 10G SFP+, 12.0.2.6, 1.0.0.7"
!System Software Version "12.0.2.6"
!System Up Time "2 days 22 hrs 7 mins 47 secs"
!Additional Packages QOS,Multicast,IPv6,IPv6 Management,Stacking,Routing
!Current SNTP Synchronized Time: SNTP Last Attempt Status Is Not Successful
!
hostname "CoreSW-1"
set gvrp adminmode
enable password f6f136b1793bd7a9da7f3edfac514c690156a6088107f654742867e597514667e20688da5f2057335dc3da47d4d669ad616f9d416d4a700979e4146ee8f43119 encrypted
serviceport protocol none
serviceport ip 10.251.251.251 255.255.255.0 0.0.0.0
vlan database
vlan 2-7
vlan name 2 "Server"
vlan name 3 "CCTV"
vlan name 4 "Operation"
vlan name 5 "Academic"
vlan name 6 "Public"
vlan name 7 "RoutingZone"
vlan routing 1 1
vlan routing 2 2
vlan routing 3 3
vlan routing 4 4
vlan routing 5 5
vlan routing 6 6
vlan routing 7 7
vlan association subnet 192.168.0.0 255.255.255.0 2
vlan association subnet 192.168.1.0 255.255.255.0 3
vlan association subnet 192.168.2.0 255.255.254.0 4
vlan association subnet 192.168.4.0 255.255.254.0 5
vlan association subnet 192.168.6.0 255.255.255.0 6
vlan association subnet 192.168.100.0 255.255.255.0 7
vlan association subnet 192.168.200.0 255.255.255.0 1
exit
configure
stack
member 1 6
member 2 6
exit
switch 1 priority 1
switch 2 priority 2
slot 1/0 6
set slot power 1/0
no set slot disable 1/0
slot 2/0 6
set slot power 2/0
no set slot disable 2/0
username "admin" password 0cc141558cdf3fe2475b8528c2d8d41e00d1351e56d2f2984581aac7521798d7d1ad50eebe599947ee39125507c38a81f3ac18f4f7f2c9a0608cd2c56607cbf1 level 15 encrypted
line console
exit
line telnet
exit
line ssh
exit
snmp-server sysname "CoreSW-1"
!
ip access-list Public-ACL
deny ip 192.168.6.0 0.0.0.255 192.168.0.0 0.0.0.255
deny ip 192.168.6.0 0.0.0.255 192.168.1.0 0.0.0.255
deny ip 192.168.6.0 0.0.0.255 192.168.2.0 0.0.1.255
deny ip 192.168.6.0 0.0.0.255 192.168.4.0 0.0.1.255
permit ip any any
exit
interface 1/0/1
vlan participation auto 1
exit
interface 1/0/2
bandwidth 10000000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
routing
ip mtu 1500
exit
interface 1/0/3
bandwidth 10000000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
vlan tagging 1
routing
ip mtu 1500
exit
interface 1/0/4
bandwidth 1000000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
routing
ip mtu 1500
exit
interface 1/0/5
bandwidth 10000000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
routing
ip mtu 1500
exit
interface 1/0/6
bandwidth 100000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
routing
ip mtu 1500
exit
interface 1/0/7
bandwidth 10000000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
routing
ip mtu 1500
exit
interface 1/0/8
bandwidth 100000
set gvrp interfacemode
switchport mode trunk
switchport trunk allowed vlan 1-7
vlan participation auto 1
routing
ip mtu 1500
exit
interface 1/0/9
switchport mode access
switchport access vlan 7
switchport trunk allowed vlan 1-7
vlan participation auto 1
vlan tagging 3
exit
interface 1/0/10
switchport mode access
switchport access vlan 7
switchport trunk allowed vlan 1-7
vlan participation auto 1
exit
interface 1/0/11
switchport mode access
vlan pvid 7
vlan participation auto 1
vlan participation include 7
exit
interface 1/0/12
switchport mode access
vlan pvid 7
vlan participation auto 1
vlan participation include 7
exit
interface 1/0/13
switchport mode access
vlan pvid 7
vlan participation auto 1
vlan participation include 7
exit
interface 1/0/14
switchport mode access
vlan pvid 7
vlan participation auto 1
vlan participation include 7
exit
interface 1/0/15
switchport mode access
vlan participation auto 1
exit
interface 1/0/16
switchport mode access
vlan participation auto 1
exit
interface 2/0/1
vlan participation auto 1
exit
interface 2/0/2
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/3
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/4
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/5
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/6
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/7
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/8
set gvrp interfacemode
vlan participation auto 1
exit
interface 2/0/9
vlan participation auto 1
exit
interface 2/0/10
vlan participation auto 1
exit
interface 2/0/11
vlan participation auto 1
exit
interface 2/0/12
vlan participation auto 1
exit
interface 2/0/13
vlan participation auto 1
exit
interface 2/0/14
vlan participation auto 1
exit
interface 2/0/15
vlan participation auto 1
exit
interface 2/0/16
vlan participation auto 1
exit
interface lag 1
vlan participation auto 1
exit
interface lag 2
vlan participation auto 1
exit
interface lag 3
vlan participation auto 1
exit
interface lag 4
vlan participation auto 1
exit
interface lag 5
vlan participation auto 1
exit
interface lag 6
vlan participation auto 1
exit
interface lag 7
vlan participation auto 1
exit
interface lag 8
vlan participation auto 1
exit
interface lag 9
vlan participation auto 1
exit
interface lag 10
vlan participation auto 1
exit
interface lag 11
vlan participation auto 1
exit
interface lag 12
vlan participation auto 1
exit
interface lag 13
vlan participation auto 1
exit
interface lag 14
vlan participation auto 1
exit
interface lag 15
vlan participation auto 1
exit
interface lag 16
vlan participation auto 1
exit
interface lag 17
vlan participation auto 1
exit
interface lag 18
vlan participation auto 1
exit
interface lag 19
vlan participation auto 1
exit
interface lag 20
vlan participation auto 1
exit
interface lag 21
vlan participation auto 1
exit
interface lag 22
vlan participation auto 1
exit
interface lag 23
vlan participation auto 1
exit
interface lag 24
vlan participation auto 1
exit
interface lag 25
vlan participation auto 1
exit
interface lag 26
vlan participation auto 1
exit
interface lag 27
vlan participation auto 1
exit
interface lag 28
vlan participation auto 1
exit
interface lag 29
vlan participation auto 1
exit
interface lag 30
vlan participation auto 1
exit
interface lag 31
vlan participation auto 1
exit
interface lag 32
vlan participation auto 1
exit
interface lag 33
vlan participation auto 1
exit
interface lag 34
vlan participation auto 1
exit
interface lag 35
vlan participation auto 1
exit
interface lag 36
vlan participation auto 1
exit
interface lag 37
vlan participation auto 1
exit
interface lag 38
vlan participation auto 1
exit
interface lag 39
vlan participation auto 1
exit
interface lag 40
vlan participation auto 1
exit
interface lag 41
vlan participation auto 1
exit
interface lag 42
vlan participation auto 1
exit
interface lag 43
vlan participation auto 1
exit
interface lag 44
vlan participation auto 1
exit
interface lag 45
vlan participation auto 1
exit
interface lag 46
vlan participation auto 1
exit
interface lag 47
vlan participation auto 1
exit
interface lag 48
vlan participation auto 1
exit
interface lag 49
vlan participation auto 1
exit
interface lag 50
vlan participation auto 1
exit
interface lag 51
vlan participation auto 1
exit
interface lag 52
vlan participation auto 1
exit
interface lag 53
vlan participation auto 1
exit
interface lag 54
vlan participation auto 1
exit
interface lag 55
vlan participation auto 1
exit
interface lag 56
vlan participation auto 1
exit
interface lag 57
vlan participation auto 1
exit
interface lag 58
vlan participation auto 1
exit
interface lag 59
vlan participation auto 1
exit
interface lag 60
vlan participation auto 1
exit
interface lag 61
vlan participation auto 1
exit
interface lag 62
vlan participation auto 1
exit
interface lag 63
vlan participation auto 1
exit
interface lag 64
vlan participation auto 1
exit
interface lag 65
vlan participation auto 1
exit
interface lag 66
vlan participation auto 1
exit
interface lag 67
vlan participation auto 1
exit
interface lag 68
vlan participation auto 1
exit
interface lag 69
vlan participation auto 1
exit
interface lag 70
vlan participation auto 1
exit
interface lag 71
vlan participation auto 1
exit
interface lag 72
vlan participation auto 1
exit
interface lag 73
vlan participation auto 1
exit
interface lag 74
vlan participation auto 1
exit
interface lag 75
vlan participation auto 1
exit
interface lag 76
vlan participation auto 1
exit
interface lag 77
vlan participation auto 1
exit
interface lag 78
vlan participation auto 1
exit
interface lag 79
vlan participation auto 1
exit
interface lag 80
vlan participation auto 1
exit
interface lag 81
vlan participation auto 1
exit
interface lag 82
vlan participation auto 1
exit
interface lag 83
vlan participation auto 1
exit
interface lag 84
vlan participation auto 1
exit
interface lag 85
vlan participation auto 1
exit
interface lag 86
vlan participation auto 1
exit
interface lag 87
vlan participation auto 1
exit
interface lag 88
vlan participation auto 1
exit
interface lag 89
vlan participation auto 1
exit
interface lag 90
vlan participation auto 1
exit
interface lag 91
vlan participation auto 1
exit
interface lag 92
vlan participation auto 1
exit
interface lag 93
vlan participation auto 1
exit
interface lag 94
vlan participation auto 1
exit
interface lag 95
vlan participation auto 1
exit
interface lag 96
vlan participation auto 1
exit
interface lag 97
vlan participation auto 1
exit
interface lag 98
vlan participation auto 1
exit
interface lag 99
vlan participation auto 1
exit
interface lag 100
vlan participation auto 1
exit
interface lag 101
vlan participation auto 1
exit
interface lag 102
vlan participation auto 1
exit
interface lag 103
vlan participation auto 1
exit
interface lag 104
vlan participation auto 1
exit
interface lag 105
vlan participation auto 1
exit
interface lag 106
vlan participation auto 1
exit
interface lag 107
vlan participation auto 1
exit
interface lag 108
vlan participation auto 1
exit
interface lag 109
vlan participation auto 1
exit
interface lag 110
vlan participation auto 1
exit
interface lag 111
vlan participation auto 1
exit
interface lag 112
vlan participation auto 1
exit
interface lag 113
vlan participation auto 1
exit
interface lag 114
vlan participation auto 1
exit
interface lag 115
vlan participation auto 1
exit
interface lag 116
vlan participation auto 1
exit
interface lag 117
vlan participation auto 1
exit
interface lag 118
vlan participation auto 1
exit
interface lag 119
vlan participation auto 1
exit
interface lag 120
vlan participation auto 1
exit
interface lag 121
vlan participation auto 1
exit
interface lag 122
vlan participation auto 1
exit
interface lag 123
vlan participation auto 1
exit
interface lag 124
vlan participation auto 1
exit
interface lag 125
vlan participation auto 1
exit
interface lag 126
vlan participation auto 1
exit
interface lag 127
vlan participation auto 1
exit
interface lag 128
vlan participation auto 1
exit
interface vlan 1
routing
ip address 192.168.200.1 255.255.255.0
exit
interface vlan 2
routing
ip address 192.168.0.1 255.255.255.0
exit
interface vlan 3
routing
ip address 192.168.1.1 255.255.255.0
exit
interface vlan 4
routing
ip address 192.168.2.1 255.255.254.0
exit
interface vlan 5
routing
ip address 192.168.4.1 255.255.254.0
exit
interface vlan 6
routing
ip address 192.168.6.1 255.255.255.0
exit
interface vlan 7
routing
ip address 192.168.100.1 255.255.255.252
exit
ip management vlan 1 192.168.200.1 255.255.255.0
router rip
exit
router ospf
exit
ipv6 router ospf
exit
ip route 0.0.0.0 0.0.0.0 192.168.100.2
exit
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
today I was going to reset both unit to factory default again. I found that the stack config and also the unit number will remain whether I reset it to factory default. I finaly run "switch 2 renumber 1" to force it to be "default", but I don't know whehter it is correct.
erase stack-config
erase startup-config
reload
en mode and then
switch 2 renumber 1 in unit 2
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Here is my flow to setup the M4300, please correct me if I was wrong
1. change oob ip address in both switch to 10.251.251.251
2. change default vlan ip to 192.168.200.1
3. enable stack in port 1 in both switches
4. power-off both switches and connect them with the stack cable
5. power-on switch A and with until the webgui can be accessed
6. power-on switch B
7. the above steps are finished in WebGUI
8. connect my mini usb to the switch A
9. rename Switch A to CoreSW -1
10. setup password and enable password
11. create vlan 2 - 7 as I mentioned before
12. setup vlan interface
13. enable trunking in port 2-10
then i found the problems
the rest of parts are
setup GVRP
may be M-LAG I think?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Hi Kelvin,
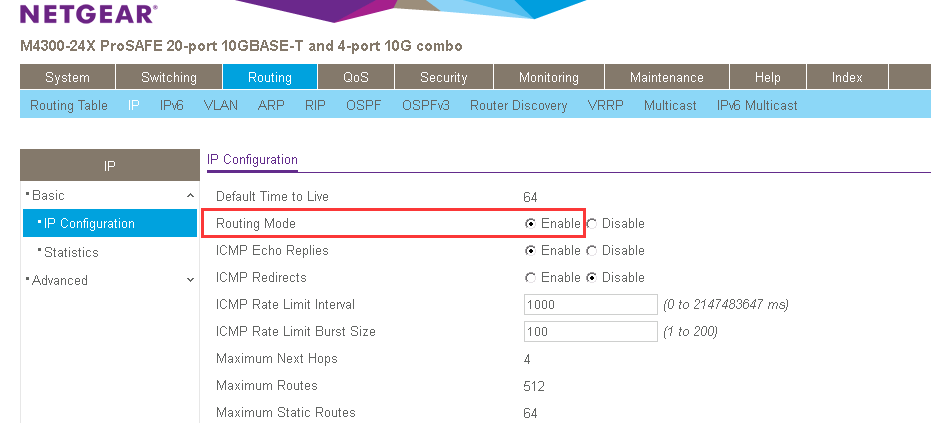
I just found the port 2-8 are "Routing mode".(command "Routing")
This means that these port will work with layer 3 mode that all packets don't have any 802.1q tag.
So the tag will always be U.
So please input "no routing" if you want to use these port as layer 2 mode.
Regards,
Daniel
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Many thx for your reply. I then followed your advise to disable the routing on the vlan interface (routing -> vlan -> vlan configuration) , but with no luck, still have error. Also, I would like to ask about the concept of the layer 3 switch. If I don't set the vlan routing on the layer 3 sw, will the traffic be routed between vlan?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
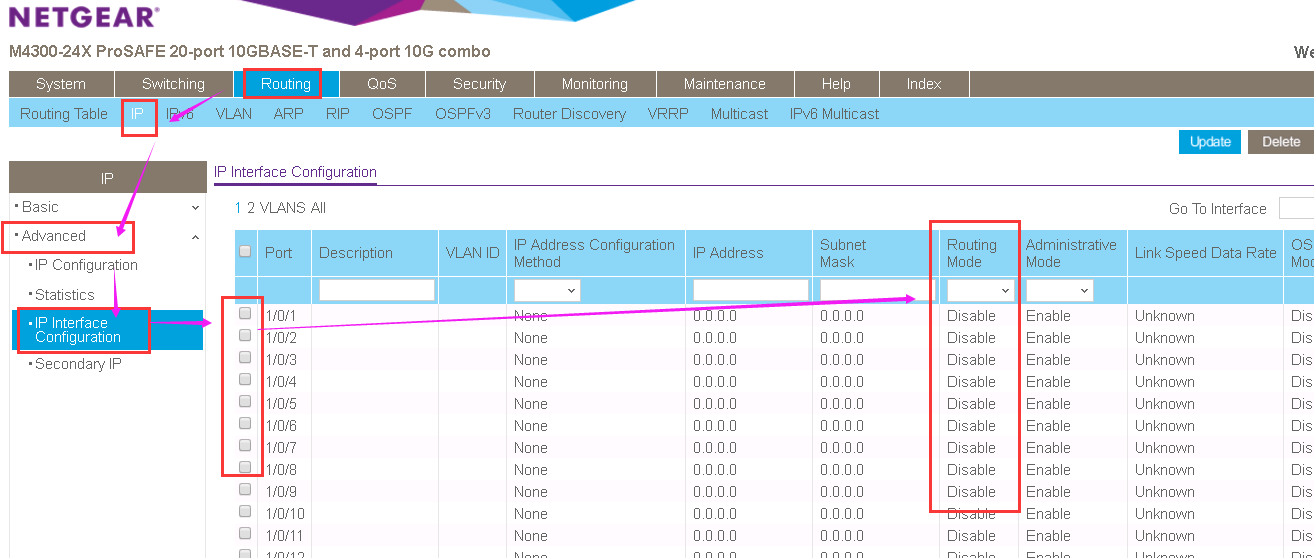
Re: M4300 SFP Port Trunking Issues
Hi Kelvin,
Please go to Routing-->IP-->Advance-->IP interface configuration.
The port routing mode can be change to disable or enable in this page.
You can get correct VLAN tag status after set port to Disable of Routing mode.
Maybe there will cause a broadcast storm after set port to layer 2 working mode(disable routing).
So please beware with loop between layer 2 network.
Otherwise, M4300 don't support MLAG function but VRRP is ready.
Please check configuration example from below link about VRRP function:
How do I configure the Virtual Router Redundancy Protocol (VRRP)
Or the user manual for M4300 about all function maybe you need to check:
M4300 Software Administration Manual
-->Page 156 chapter 10
Regards,
Daniel.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
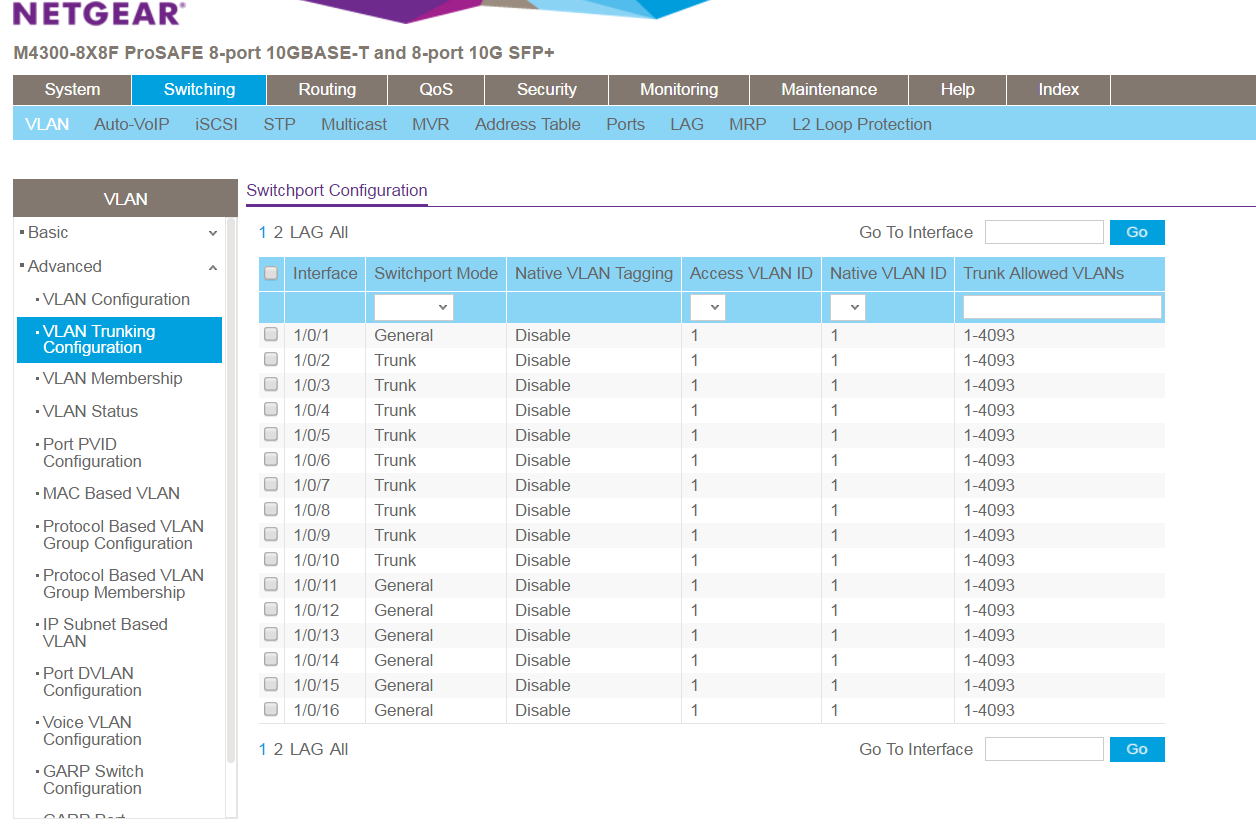
I think I found the solution, it's because the trunking setting. I reset the switch and start over again. instead making the port trunk in "switch - > vlan trunking configuration" (should be "switchport mode trunk" in CLI) , and changed the switchport mode from general to Trunk, it started to be abnormal. if I turn it on, I cannot mark the port as "T" in vlan membership. it's not about the routing I think? But this is so strange, since "switchport mode trunk" and "switchport trunk allowed vlan X" are nearly the standard command in differenct brand of switch? And I assumed that when I trunk those ports, it will be auto labelled the port as "T". In fact, It only allow either one? Since I didn't test it, i don't know which should be the correct approach to getting the trunk work?
In addition, I stacked 2 switches, one of them is standby, so I might be able to just LAG 2 ports in my layer 2 sw and do nothing in layer 3 since it seems to be a "virtual switch"?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
also, I have a test on routing config. It cannot be enabled as you mentioned or the trunk will not work. And the switchport mode cannot be set to trunk at the same time.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
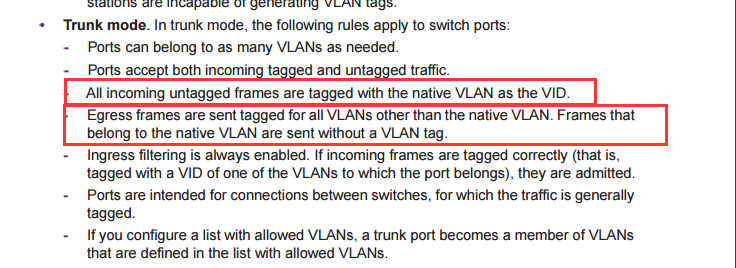
Re: M4300 SFP Port Trunking Issues
Hi Kelvin,
Please find the instruction about Trunk mode with native VLAN as below:
So you can see the VLAN member is "U" on VLAN 1 due to 1 is native VLAN.
For other VLAN (2-4093) it will be "T" due to it is allowed trunk VLAN.
For your addition question,
It work as a whole switch after M4300 get stacked.
So you might treat the stack master and standby as a whole switch which have multi port.![]()
Regards,
Daniel.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Hi Daniel,
thx for your patience~I will try to fix it by following your advise. Also, I have GS series switches in layer 2, like GS748T / GS724T etc. is it possible to connect it with SFP port to M4300? let's say, port 47 to stack master and port 48 to stack 2 (both ports are set to trunk port)
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Hi KelvinFu
Yes absolutely you can LAG ports on your M4300 stack across the master and the redundant management unit; and connect to individual Smart Managed switches GS724T or GS748T using their SFP ports each time in a LAG as well.
First, please use 1Gbps SFP GBICs on both side, since M4300 SFP+ ports must run in Gigabit mode when connecting to Gigabit-only other switches. If multimode fiber, you can use NETGEAR AGM731F 1000BASE-SX SFP transceiver.
Second, please try to use same LAG settings on both side: by default, LAGs are dynamic (LACP mode). Given Smart Managed switches only provide Layer 2 (destination MAC addresses) hashing, you should use Layer 2 hashing algorithm with your Fully Managed M4300 series stack as well. (M4300's can offer L2 / L3 / L4 hashing, but here hashing must be the same on both ends)
For M4300's, you will find LAG configuration examples (both Web GUI and CLI) in Software Administration manual on page 68.
Regards,
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
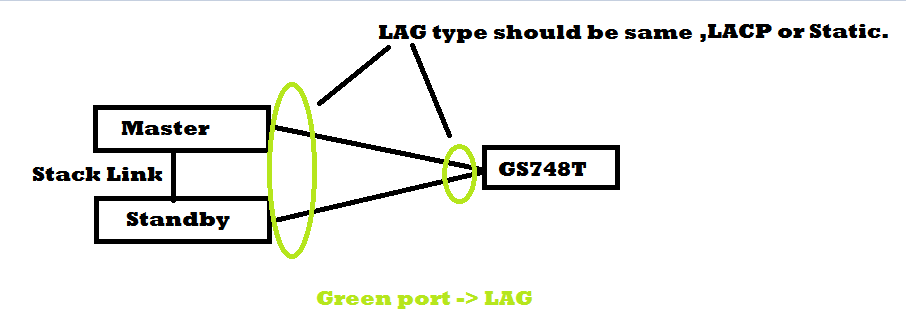
Re: M4300 SFP Port Trunking Issues
Hi Kelvin,
So you want to connect two port from GS748T to M4300 Stack as a redundancy link.
Both Port 47 or port 48 are fine to deploy your requirement.
I suggest you to create a LAG on both side and add connected port into it.
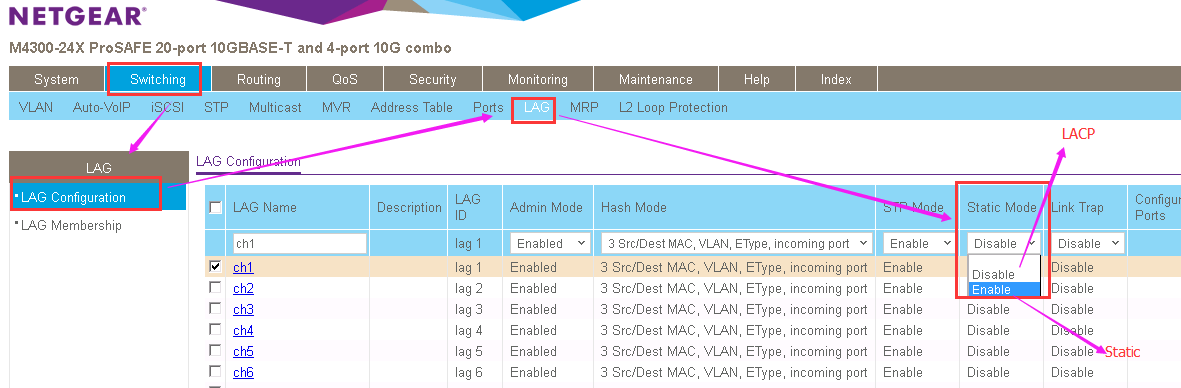
But The LAG type is LACP(dynamic) on M4300 by default and GS748T is static by default.
You need to make the LAG type to a same value as dynamic or static on both switch.(dynamic is RECOMMENDED )
Please check below document about how to creat LAG and set LAG type to dynamic and static.
-->chapter 3,page 68.
Please see my example as below:
Let us know if you have any further concern.
Regards,
Daniel.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
thx both, I will try it tomorrow !!!! ![]()
![]()
![]()
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
almost done, but I cannot ping the firewall >_<, LAG is up, but connect connect from the layer 2 switch, my pc can ping reach every vlan interface
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
should I mark port 9 / 10 to access port instead of trunk port?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Hi Kelvin,
Thanks for your update.
The VLAN configuration will only effect on LAG port after you add 1/0/9,2/0/9 into LAG 6.
So we should mark the LAG 6 into VLAN 7 with Tag or Untag (according with your Firewall support to accept Tag packets or not)
I think most of Firewall just support untag mode of layer 3 interface just like yours.
So Could you please add LAG 6 into VLAN 7 with untag mode?
You can chose one of the three ways to deploy this configuration:
1) Set LAG 6 to general mode,
Set PVID 7 on LAG 6
Add LAG 6 into VLAN 7 with untag mode (U)
2) Set LAG 6 to Access mode,
Access VLAN 7.
3) Set LAG 6 to Trunk mode.
Allowed VLAN 7
Native VLAN 7
Let us know if you get new update![]()
Regards.
Daniel.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Hi Daniel,
thx for your help, I took option 1 as my choice. but then i found that i can only ping 192.168.100.2 with the same vlan in layer 2 switch /w ip 192.168.100.3, if i plug to vlan 2 /w ip 192.168.1.3, then i cannot ping 192.168.100.2, it seems the routing problem?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Hi Kelvin,
It seems to be a routing problem.
Please check the following steps on your network:
1) The route to the special subnet on Firewall.
Such as:
192.168.0.x/24 192.168.100.1
192.168.1.x/24 192.168.100.1
192.168.2.x/24 192.168.100.1
192.168.3.x/24 192.168.100.1
192.168.4.x/23 192.168.100.1
192.168.6.x/23 192.168.100.1
Please add route for every subnet if thr firewall don't have these routes.
2) The default gateway on PC.(The gateway should be the IP address on VLAN of Stack)
Or you can add static route for every special subnet above if you don't want to set default gateway on your PC.
3) Make sure the IP routing is "enable" on Stack
Please try again after above checklist has been done.
Regards,
Daniel.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Hi Daniel,
Yes, that's the point, I've fixed it. Now I have the rest of 2 questions I think ( hopefully no more T_T)
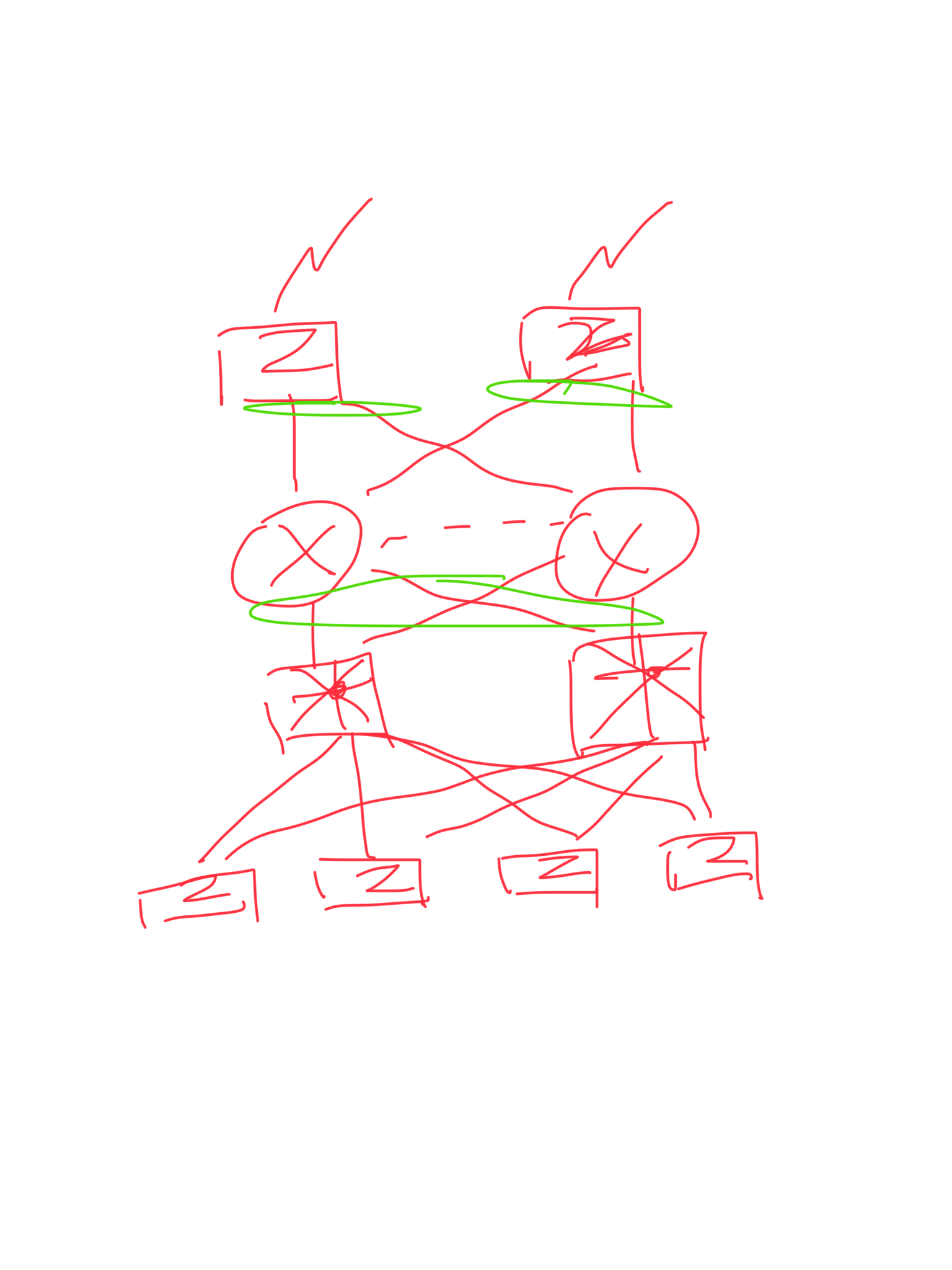
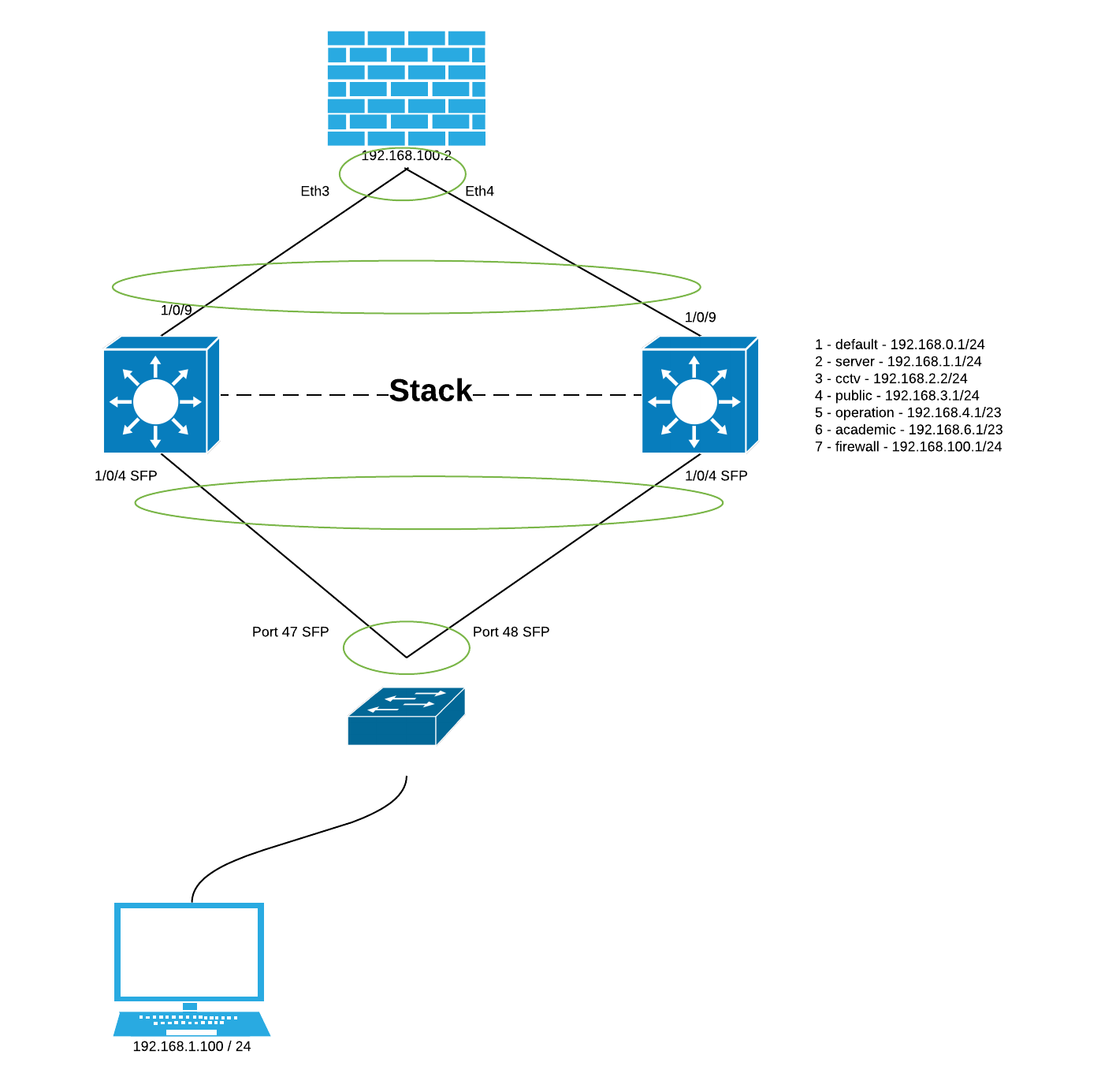
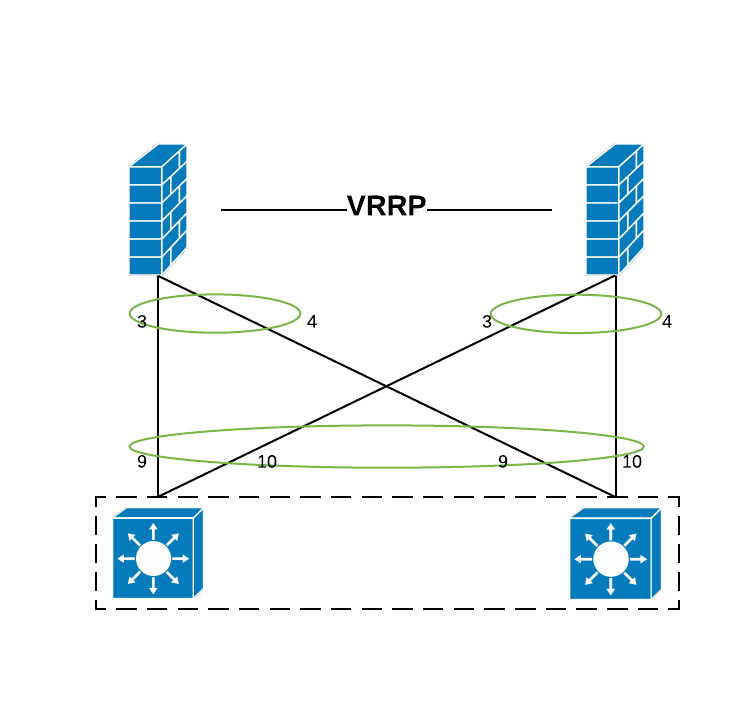
1. HA Question
I now have 2 LAG, and connect to 2 firewalls that in VRRP mode, Firewall A is active while B is standby, eth3 and eth4 are formed as active/standby LAG wiht IP: 192.168.100.2/24.
as you can see at the previous post, I have 2 LAGs in switch stack.
1/0/9 and 2/0/9 in LAG1 and connect to eth 3 / 4 (aggr 1) of Firewall A
1/0/10 and 2/0/10 in LAG2 and connect to eth 3 / 4 (aggr 1) of Firewall B
LAG1 and LAG2 are in VLAN 7
Scenario 1.
unplug only eth 3 in firewall A, work well
Scenario 2.
upplug only eth 4 in firewall A, work well
Scenario 3.
unplug both eth 3 / 4 or poweroff firewall A, cannot switch to firewall B which is my expection
Scenario 4.
poweroff firewall B, work well
Since Firewalls are in VRRP protocol, i expect all traffic will be redirected to firewall B, but seems I have some conceptual mistake
2. Failover
I found that if stack master is failure, I cannot ping the vlan interface whether it is resumed or not. I have to poweroff the slave once to make it work again. is it normal?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: M4300 SFP Port Trunking Issues
Hi Kelvin,
It's all right.
Any posts is welcome ![]()
1. HA Question
For scenario 3,
Please check the VRRP status on Firewall B after you unplug both eth 3 / 4 or poweroff firewall A.
The VRRP status on Firewall B should be Master after Firewall A is down.
Please check VRRP function and configuration on Firewall A&B If above function don't work as expected.
I also have some suggest step for you to check VRRP function and configuration on Firewall:
1) VRRP need two router(Firewall) add in same virtual router group with same subnet IP address
such as:
Firewall A: 192.168.100.10 /24
Firewall B: 192.168.100.20 /24
2) A virtual IP address must be assigned in this virtual group.
such as:
Virtual IP: 192.168.100.30 /24
(you can also set virtual IP same with Firewall A or Firewall B, that will make the Firewall to be VRRP IP owner which have same address as Virtual IP)
3) All clients must set the gateway to Virtual IP instead of the IP on Firewall A or Firewall.
Such as:
PC: 192.168.100.201 /24, Gateway: 192.168.100.30.
4) Set LAG mode to LACP(dynamic)
This mode will detect&switch link status automatic when the link is down or unavailable.
(LACP mode of LAG must support on both side of Switch and Firewall as same time.).
such as:
Set LAG mode to dynamic LACP on Switch: Static mode-->Disable (Go to Switch--->LAG--->LAG configuration-->Select LAG port--->Static Mode)
Set LAG mode to dynamic LACP on Firewall A&B.(Please check manual document of firewall)
5) <*Optional>these extra function will help you to monitor and control VRRP more Reliable.
Set VRRP track interface on Firewall(if supported)
Set VRRP Router Priority and Preemption on Firewall(if supported)
2. Failover.
1) Please check the LAG configuration on both side(stack and GS748T)
All LAG member and LAG port should have same VLAN configuration.
2) Please modify the LAG type to dynamic LACP mode on stack.
such as:
Set LAG mode to dynamic LACP on Switch: Static mode-->Disable (Go to Switch--->LAG--->LAG configuration-->Select LAG port--->Static Mode)
On GS748T, the same LAG type should be configured.
Let me know if you have any update.
BTW,
Please send your maintenance to us if possible.
We can analyze your scenario more carefully with configuration file and topology.
Please follow as below step to send maintenance information.
How do I send diagnostic files from my Smart Switch to NETGEAR community moderators?
http://kb.netgear.com/app/answers/detail/a_id/31438
How do I send diagnostic files from my Managed Switch to NETGEAR community moderators?
http://kb.netgear.com/app/answers/detail/a_id/31439
Regards,
Daniel.