- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Re-creating an RSPAN VLAN on an M4100-50G switch
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello everyone,
I would like assitance in re-creating an RSPAN VLAN on an M4100-50G switch.
Background information:
We have a firewall that we are monitoring network traffic on. On a previous setup, the firewall was connected to a Cisco SG300-10 10Gigabit managed swtich. The purpose of this switch was to port-mirror the traffic so that we could monitor the network. Initially, the mirrored port was plugged into one server only, a server running Ntop-NG. We then wanted to take the same traffic and have it monitored by two more servers; one being an raw packet capture server, OpenFPC and the other an IDS/IPS server running software called Scirius by Stamus Networks. At first, we thought of using a 100Mbit hub to duplicate the network traffic coming from the mirrored switchport on the Cisco unit, but we did not have any in our stash of old equipment.
I then stumbled upon an old article on the web, http://blog.ine.com/2008/02/05/turning-switch-into-hub/. It focused on Cisco gear and stated that it may be possible to use a network switch and make it act like a hub by using the RSPAN VLAN feature, if supported, and setting ports to use that same RSPAN VLAN as the native VLAN. We do not have any enterprise Cisco gear, however, we do have Netgear managed switches that are very comparable. I tried to setup four ports on a Netgear M4300-52G-PoE+ to mimic what was stated in the article and to my surprise, it worked! I created a VLAN 500, enabled it as an RSPAN VLAN, and set ports 0/45 - 0/48 to be tagged ports as well as set the PVID to be VLAN 500. The mirrored port from the Cisco switch was then plugged into port 0/47 on the Netgear switch and all three network monitor server were plugged in to the other switch ports. All servers could now see the same network traffic! Yay!
Now, trying to do some server room clean up, we have swapped the Cisco SG-300 switch to a CyberData 3-port USB Gigabit port mirroring switch (an active network tap) and moved the server connections to a Netgear M4100-50G network switch located in the same rack as the servers. I am trying to duplicate the RSPAN VLAN setup as was on the Netgear M4300 switch; same VLAN ID of 500, RSPAN enabled, and using the same ports 0/45 - 0/48, however, I am not able to get it to work. No network traffic seems to be duplicated as before.
Is there something different that I may have missed in setting up this other switch?
Any help would be greatly appreciated! Thank you!
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi jg75996,
Could you disable STP mode for port 0/45~0/48 on M4100 and try again?
Web GUI go to 'Switching'-->'Ports'-->'Configuration', then select port 0/45~0/48, set STP Mode to 'Disable'.
All Replies
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi jg75996,
Welcome to the community! ![]()
For RSPAN feature, there is three switch role, working as 'source Switch', 'intermediate Switch' and 'destination Switch'. And there is different configuration for different role switch.
So what is the role for M4100 and M4300?
Below is the example for RSPAN configuration:
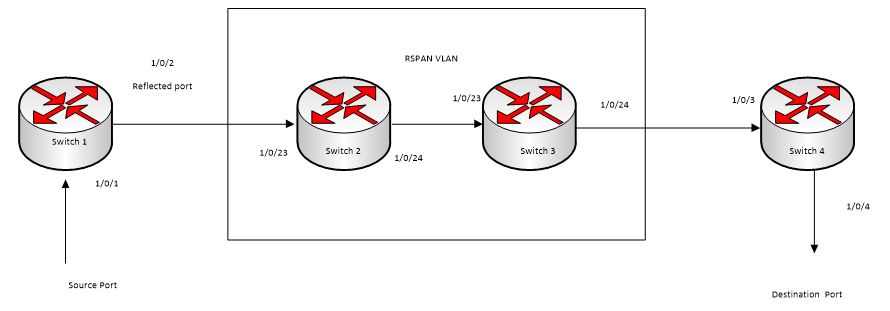
RSPAN
Mirroring is very useful to monitor traffic to/from the port by copying the traffic to the probe port for analysis. But usually mirroring is limited to be working on one switch, RSPAN(remote switched port analyzer) extends it by enabling RSPAN. The mirrored packets are carried over all of participating switches.
The Figure above illustrates an example RSPAN. The switch 1 is the source switch 1, switch 2 and switch 3 are intermediate switch. The switch4 is the destination switch.
The ports connected towards the destination switch (switch 4) must be configured with tagging (with the vlan id as RSPAN VLAN). These ports are configured with the RSPAN VLAN participation as well. Only one RSPAN VLAN is supported.
On the source switch 1, the traffic received/transmitted on source ports (1/0/1) is tagged with the RSPAN VLAN and transmitted on the configured reflector port. The reflector port(1/0/2) is the physical interface that carries the mirrored traffic towards the destination switch (switch 4).
The intermediate switch (switch 2 and switch3) forwards the incoming tagged traffic towards the destination switch (switch4). RSPAN VLAN should be created on the intermediate switch; the ports connected towards Source and Destination switch should have the RSPAN VLAN participation. RSPAN VLAN egress tagging should be enabled on interface on intermediate switch connected towards Destination switch.
The destination switch (switch4) accepts all the tagged (with RSPAN VLAN) packets and mirrors them on the destination port (to which the traffic analyzer is connected).
The original tag is retained at the destination switch, the mirrored traffic is seen with double tagging (inner tag is the original VLAN ID and the outer tag is RSPAN VLAN ID).
CLI: enable RSPAN on the switch
- On the source switch(switch1) the below parameters are configured:
- Source ports (i.e. the traffic on this port is mirrored)
- RSPAN VLAN (as destination)
- Reflector port
- Tx/Rx
|
(Netgear Switch) #vlan database (Netgear Switch) (Vlan)#vlan 5 (Netgear Switch) (Vlan)#exit (Netgear Switch) #config (Netgear Switch) (Config)#vlan 5 (Netgear Switch) (Config)(Vlan 5)#remote-span (Netgear Switch) (Config)(Vlan 5)#exit (Netgear Switch) (Config)#monitor session 1 mode (Netgear Switch) (Config)#monitor session 1 source interface 1/0/1 (Netgear Switch) (Config)#monitor session 1 destination remote vlan 5 reflector-port 1/0/2 (Netgear Switch) (Config)#exit (Netgear Switch) #show monitor session 1 Session Admin Probe Src Mirrored Ref. Src Dst Type IP MAC ID Mode Port VLAN Port Port RVLAN RVLAN ACL ACL ------- ------- ------ ---- -------- ------ ----- ----- ----- ------- ------- 1 Enable 1/0/1 1/0/2 5 Rx,Tx
|
2. On the intermediate switch(switch2 or switch3) the below parameters are configured:
- Add the ports to vlan with tagging
|
(Netgear Switch) #vlan database (Netgear Switch) (Vlan)#vlan 5 (Netgear Switch) (Vlan)#exit (Netgear Switch) #config (Netgear Switch) (Config)#interface 1/0/23 (Netgear Switch) (Interface 1/0/23)#vlan participation include 5 (Netgear Switch) (Interface 1/0/23)#vlan tagging 5 (Netgear Switch) (Interface 1/0/23)#exit (Netgear Switch) (Config)#interface 1/0/24 (Netgear Switch) (Interface 1/0/24)#vlan participation include 5 (Netgear Switch) (Interface 1/0/24)#vlan tagging 5 (Netgear Switch) (Interface 1/0/24)#exit |
3. On the destination switch (switch4) the below parameters are configured:
- RSPAN VLAN (as source)
- Probe port
|
(Netgear Switch) #vlan database (Netgear Switch) (Vlan)#vlan 5 (Netgear Switch) (Vlan)#exit (Netgear Switch) #config (Netgear Switch) (Config)#vlan 5 (Netgear Switch) (Config)(Vlan 5)#remote-span (Netgear Switch) (Config)(Vlan 5)#exit (Netgear Switch) (Config)#interface 1/0/3 (Netgear Switch) (Interface 1/0/3)#vlan participation include 5 (Netgear Switch) (Interface 1/0/3)#vlan tagging 5 (Netgear Switch) (Interface 1/0/3)#exit (Netgear Switch) (Config)#monitor session 1 mode (Netgear Switch) (Config)#monitor session 1 source remote vlan 5 (Netgear Switch) (Config)#monitor session 1 destination interface 1/0/4 (Netgear Switch) #show monitor session 1 Session Admin Probe Src Mirrored Ref. Src Dst Type IP MAC ID Mode Port VLAN Port Port RVLAN RVLAN ACL ACL ------- ------- ------ ---- -------- ------ ----- ----- ----- ------- ------- 1 Enable 1/0/4 5
|
Hope it helps!
Regards,
EricZ
NETGEAR employee
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hello EricZ,
Thank you for the information on how RSPAN is utilized in a three switch role.
The switch models that I have mentioned have the following roles:
For the M4300-52G-PoE+, there are 7 switches configured in a stack and they are housed in a standalone rack. They act as our core switch, with connections going to workstations, VoIP phones, NAS boxes, routers and other network appliances.
The M4100-50G is our "server" switch and is located in a server rack that is on the other side of the network room. This switch is uplinked to the M4300 switchstack via a trunk line.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi jg75996,
Thanks for your immediately response. Now we clear your two switch working role.
Could you kindly answer more questions as below:
1. In your network topology, which switch is working as source switch for RSPAN? Which port traffic you want to mirror?
2. In your network topology, which switch is working as destination switch for RSPAN? Which port you want to receive the mirror traffic?
And if these two problem is clear, we can check the configuration further more.
Thanks.
Regards,
EricZ
NETGEAR employee
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hello EricZ,
I don't plan on having one switch as source and one as destination. Just trying to replicate what I had on the M4300 originally on to the M4100.
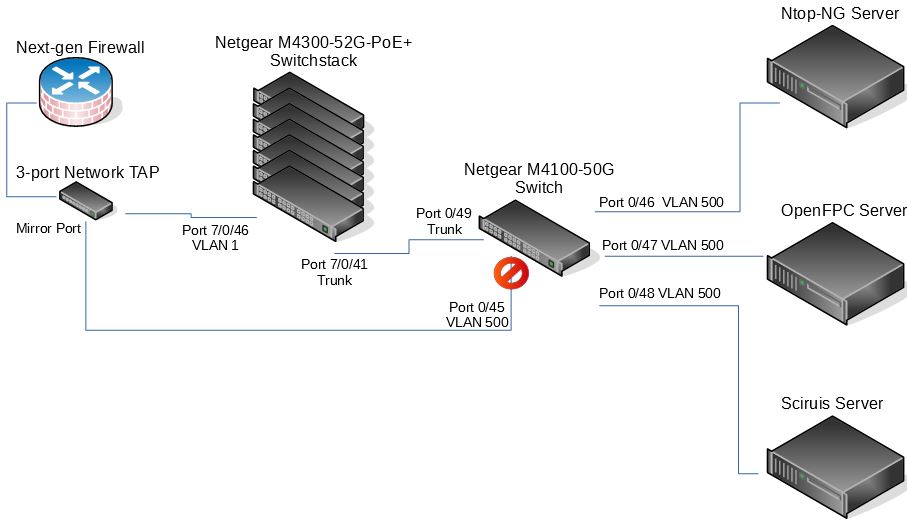
Here is the current layout of the devices involved:
What seems to be happening is that port 0/45 on the M4100 switch is discarding the packets coming from the network tap mirror port.
I think it may be that Spanning Tree is blocking the port. Most likely it is because the link coming from the tap is being detected as a loop in the network.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
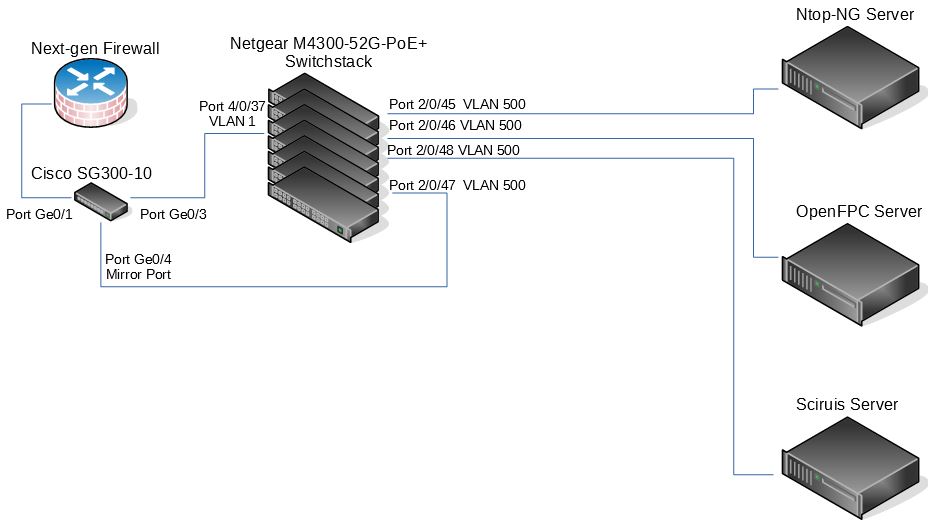
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
... and here is the old layout that was working before...
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi jg75996,
Ok, according to these two network topology, could you paste the configuration for M4300 port 2/0/45~2/0/48 and for M4100 port 0/45~0/48, we need more detailed information for further analysis.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hello EricZ,
I had already made changes to the config for the M4300 switchstack, however, I will put it back to what it was and hopefully that will help.
For the M4300, the configuration was:
!System Description "M4300-52G-PoE+ ProSAFE 48-port 1G PoE+ and 2-port 10GBASE-T and 2-port 10G SFP+, 12.0.2.6, 1.0.0.8"
!System Software Version "12.0.2.6"
!Additional Packages QOS,Multicast,IPv6,IPv6 Management,Stacking,Routing
boot auto-copy-sw
vlan database
vlan 500
vlan name 500 "RSPAN 1"
vlan routing 1 1
exit
stack
member 1 4
member 2 4
member 3 4
member 4 4
member 5 4
member 6 4
member 7 4
exit
switch 1 priority 14
vlan 500
remote-span
exit
interface 2/0/45
vlan pvid 500
vlan participation auto 1
vlan participation include 500
vlan tagging 500
exit
interface 2/0/46
vlan pvid 500
vlan participation auto 1
vlan participation include 500
vlan tagging 500
exit
interface 2/0/47
vlan pvid 500
vlan participation auto 1
vlan participation include 500
vlan tagging 500
exit
interface 2/0/48
vlan pvid 500
vlan participation auto 1
vlan participation include 500
vlan tagging 500
exit
interface vlan 1
routing
ip address dhcp
exit
router rip
exit
router ospf
trapflags state-change if-state-change
trapflags state-change neighbor-state-change
exit
ipv6 router ospf
exit
service dhcp
exit
(M4300-52G-PoE+) #
==============================================
And for the M4100, the configuration is:
!Current Configuration:
!
!System Description "M4100-50G ProSafe 48-port Gigabit L2+ Intelligent Edge Managed Switch, 10.0.2.20, B1.0.1.1"
!System Software Version "10.0.2.20"
!Additional Packages QOS,IPv6 Management,Routing
!
enable password 8fbe5e2eded09692e1d8f96f8ea8a3d3038eb85e8fb528c5a83bfeccd5390a8f49cb5f269f0ed555fe823a122495453ab76464824d6930681f576ede873a8a1e encrypted
vlan database
vlan 500
vlan name 500 "RSPAN 1"
vlan routing 1 1
exit
vlan 500
remote-span
exit
interface 0/45
vlan pvid 500
vlan participation auto 1
vlan participation include 500
vlan tagging 500
exit
interface 0/46
description 'RSPAN port for SELKS IDS/IPS'
vlan pvid 500
vlan participation auto 1
vlan participation include 500
vlan tagging 500
exit
interface 0/47
description 'RSPAN port for OpenFPC'
vlan pvid 500
vlan participation auto 1
vlan participation include 500
vlan tagging 500
exit
interface 0/48
description 'RSPAN port for Ntop-NG'
vlan pvid 500
vlan participation auto 1
vlan participation include 500
vlan tagging 500
exit
interface vlan 1
routing
ip address dhcp
exit
exit
(M4100-50G) #
==================================================
Thank you for looking into this!
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi jg75996,
According your network topology and configuration, we think RSPAN function not take affect actually.
On M4300 scenario, Server can monitor the traffic from Cisco SG-300 switch, it's just because M4300 forwarding the traffic from port 2/0/47 to port 2/0/45&46&48.
But on M4100 scenario, Server cannot monitor the traffic, you can check whether port 0/45 receice traffic or not?
(Via CLI command:
clear counters all
show interface counters
Via web GUI:
'Monitoring-->Ports-->Port Statistics'
)
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
From the web GUI, here are the detailed port statistics since yesterday, when the counters were cleared:
Interface 0/45
MST ID CST
ifIndex 45
Port Type Normal
Port Channel ID Disable
Port Role Alternate
STP Mode Enable
STP State Discarding
Admin Mode Enable
Flow Control Mode Disable
LACP Mode Enable
Physical Mode Auto
Physical Status 1000 Mbps
Link Status Link Up
Link Trap Enable
Packets RX and TX 64 Octets 13035563
Packets RX and TX 65-127 Octets 6238375
Packets RX and TX 128-255 Octets 6148778
Packets RX and TX 256-511 Octets 3128981
Packets RX and TX 512-1023 Octets 4783335
Packets RX and TX 1024-1518 Octets 13656666
Packets RX and TX 1519-2047 Octets 0
Packets RX and TX 2048-4095 Octets 0
Packets RX and TX 4096-9216 Octets 0
Octets Received 27043987429
Packets Received 64 Octets 13035563
Packets Received 65-127 Octets 6237552
Packets Received 128-255 Octets 6147956
Packets Received 256-511 Octets 3128981
Packets Received 512-1023 Octets 4783335
Packets Received 1024-1518 Octets 13656666
Packets Received > 1518 Octets 0
Total Packets Received Without Errors 46990053
Unicast Packets Received 46642886
Multicast Packets Received 55593
Broadcast Packets Received 291574
Receive Packets Discarded 0
Total Packets Received with MAC Errors 0
Jabbers Received 0
Fragments Received 0
Undersize Received 0
Alignment Errors 0
Rx FCS Errors 0
Overruns 0
Total Received Packets Not Forwarded 0
802.3x Pause Frames Received 0
Unacceptable Frame Type 0
Total Packets Transmitted (Octets) 232723
Packets Transmitted 64 Octets 0
Packets Transmitted 65-127 Octets 823
Packets Transmitted 128-255 Octets 822
Packets Transmitted 256-511 Octets 0
Packets Transmitted 512-1023 Octets 0
Packets Transmitted 1024-1518 Octets 0
Packets Transmitted > 1518 Octets 0
Maximum Frame Size 1518
Total Packets Transmitted Successfully 1645
Unicast Packets Transmitted 0
Multicast Packets Transmitted 1645
Broadcast Packets Transmitted 0
Transmit Packets Discarded 0
Total Transmit Errors 0
Total Transmit Packets Discarded 0
Single Collision Frames 0
Multiple Collision Frames 0
Excessive Collision Frames 0
STP BPDUs Received 0
STP BPDUs Transmitted 0
RSTP BPDUs Received 12526
RSTP BPDUs Transmitted 0
MSTP BPDUs Received 0
MSTP BPDUs Transmitted 0
802.3x Pause Frames Transmitted 0
GVRP PDUs Received 0
GVRP PDUs Transmitted 0
GVRP Failed Registrations 0
GMRP PDUs Received 0
GMRP PDUs Transmitted 0
GMRP Failed Registrations 0
EAPOL Frames Received 0
EAPOL Frames Transmitted 0
Time Since Counters Last Cleared 0 day 6 hr 57 min 29 sec
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi jg75996,
Thanks for your info.
Looks like port 0/45 can receive traffic.
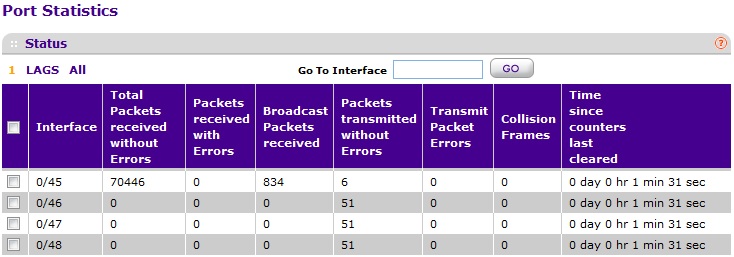
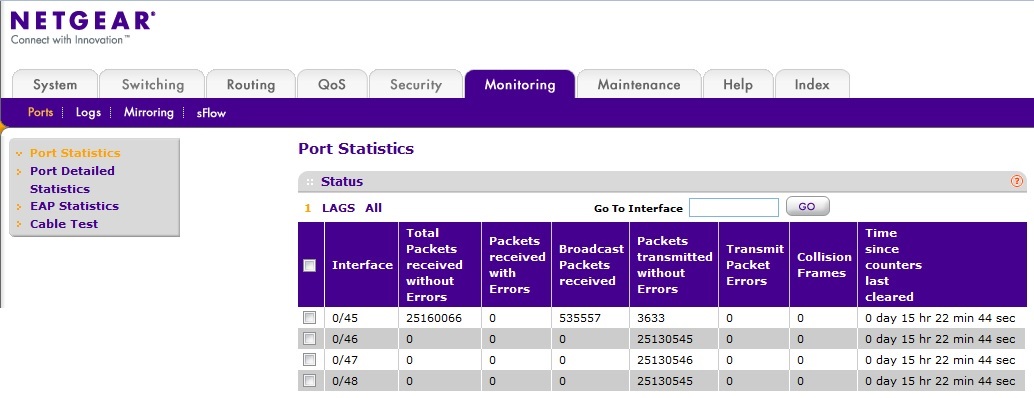
And could you screenshot for 'Port Statistics' via GUI for port 0/45~0/48, no need Port Detailed Statistics, just sumary statistics is ok.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
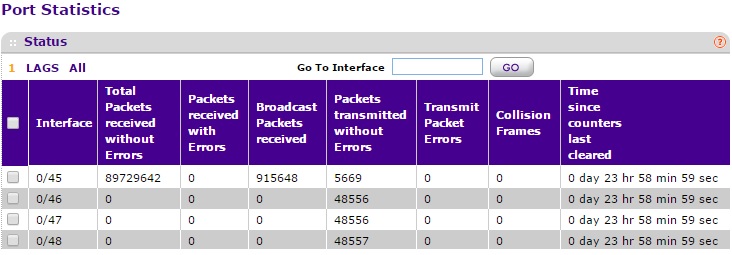
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Sorry about that, EricZ. ![]()
Here is a screenshot of the port statistics for ports 0/45-48 as requested.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
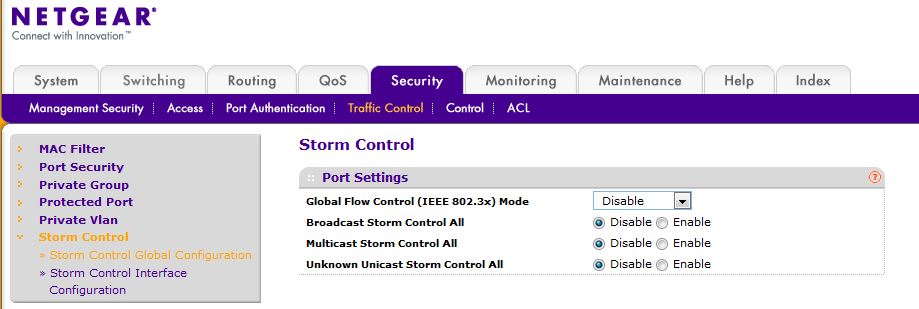
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi jg75996,
Could you check Storm-Control config on M4100. If it's enabled for broadcast/multicast/unknown unicast, please disable all and try again.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi EricZ,
I have disabled Storm Control on the switch...
... cleared port statistics and refreshed after a minute or so ...
Is there anything to look for in regards to the change? At the moment, nothing seems to stand out.
Thanks for continuing to troubleshoot.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
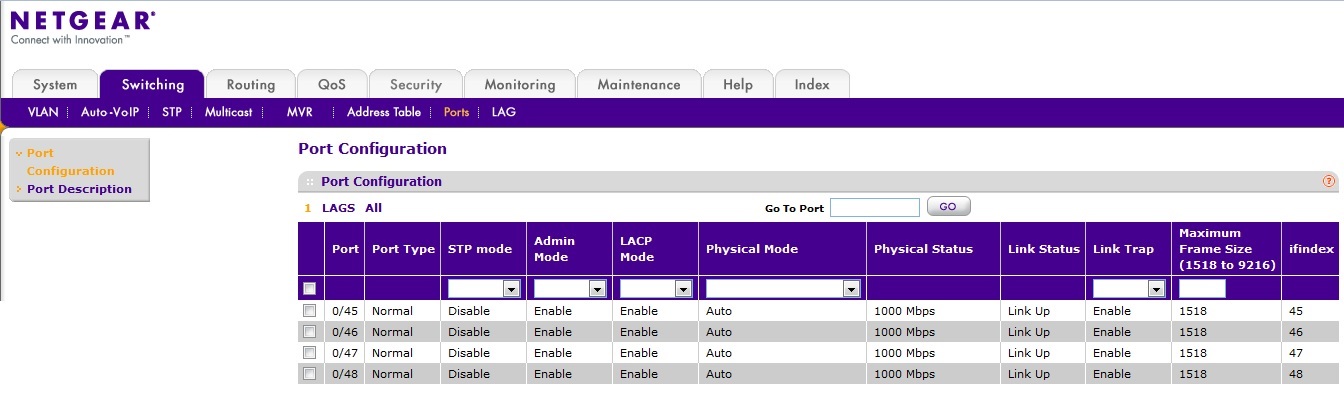
Hi jg75996,
Could you disable STP mode for port 0/45~0/48 on M4100 and try again?
Web GUI go to 'Switching'-->'Ports'-->'Configuration', then select port 0/45~0/48, set STP Mode to 'Disable'.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi EricZ,
I have disabled the ports per your direction...
... and cleared the port statistics. Went home and checked the stats again this morning, and they now show ...
This looks promising!
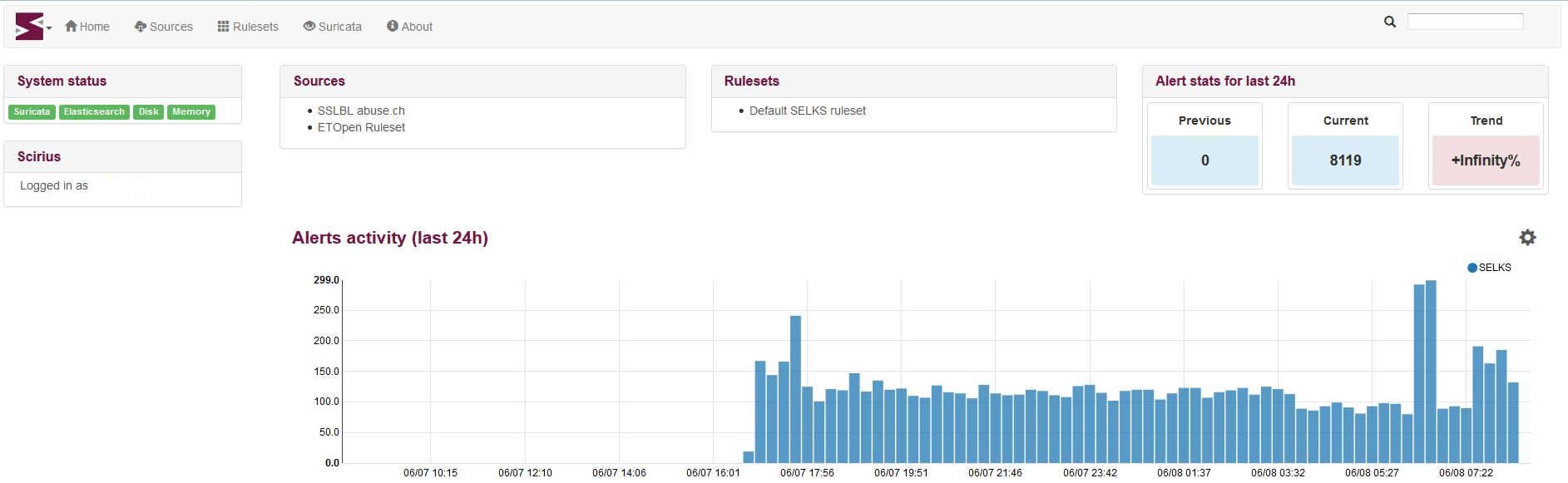
I then checked our servers, Ntop-NG, SELKS, and OpenFPC and am now able to see traffic coming in to the systems. For example, here is a screenshot from the Scirius server that is plugged into port 0/47:
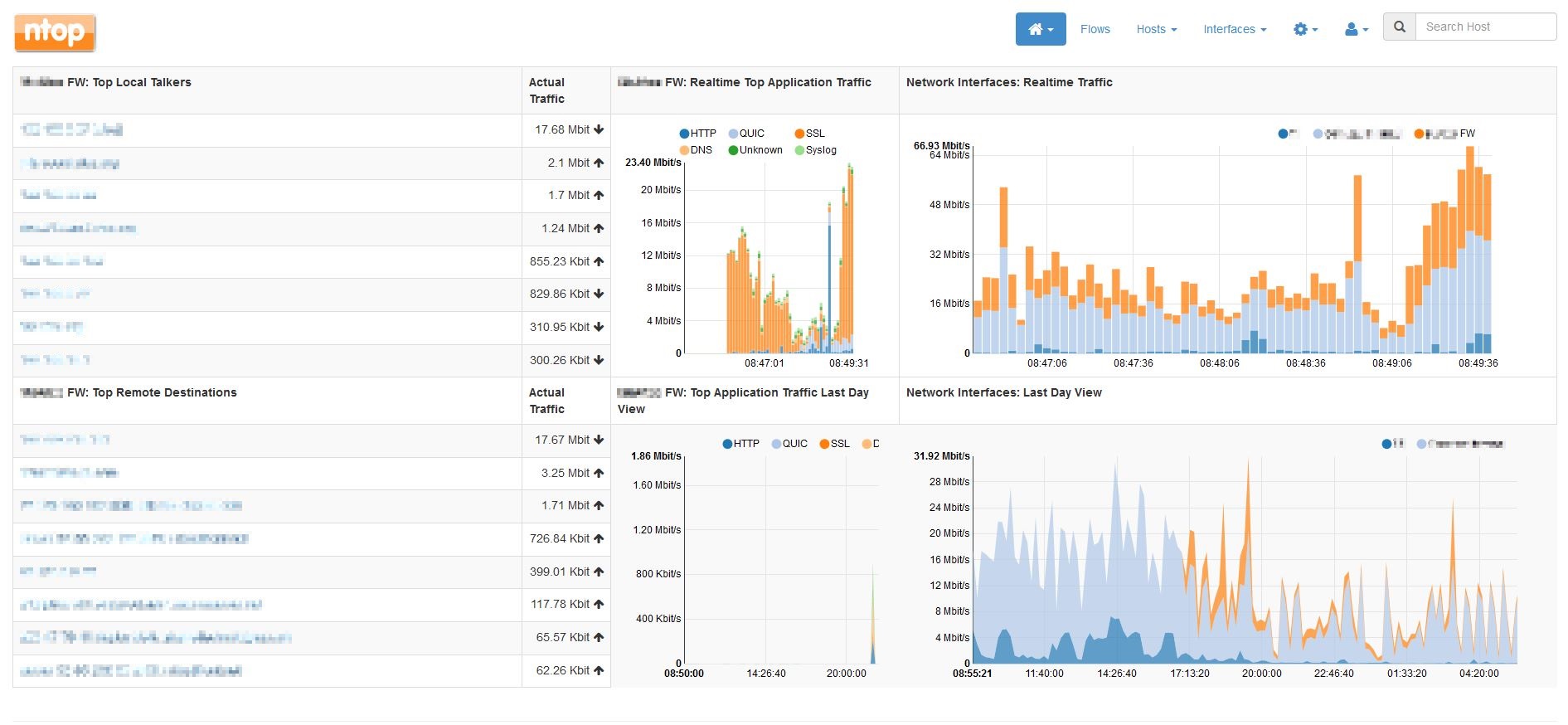
... and here's one from Ntop-NG on port 0/48 (the traffic from the firewall is in orange)...
I think that change has solved my issue.
Now that it seems to be working, I would like to know if enabling RSPAN for VLAN 500 is still a requirement for this particular setup?
Thank you very much!
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi jg75996,
I'm glad to hear it working now.
I think it's not necesssary to enable RSPAN for VLAN500.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hello EricZ,
I'd like to let you know that I disabled RSPAN on VLAN 500, cleared the statistics on ports 0/45-48, and noticed that the number of packets on ports 0/46-48 significantly dropped again.
Thinking that the change that I made, affected that, I re-enabled RSPAN for VLAN 500, but I don't see the number of packets being duplicated anymore.
Can this issue be re-visited?
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi jg75996,
Ok, well. Could you please provide detailed information as below:
1. Pls screenshot the port statistics for 0/45~48
2. Pls screenshot the Spanning-tree port status for 0/45~48 by GUI 'Switching'-->'STP'-->'Advanced'-->'CST Port Status'
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi EricZ,
I am trying to reply back with screenshots, however, I no longer have the ability to insert images.
Let me see if I can describe to you what I see.
For Item #1, after clearing port statistics and then refreshing after a minute:
Port 0/45: 175235 Total Packets received without Errors
Port 0/46: currently disconnected
Port 0/47: 2983 Packets transmitted without Errors
Port 0/48: 2983 Packets transmitted without Errors
For Item #2:
Port 0/45: Port Forward State - Manual forwarding
Port 0/46: currently disconnected
Port 0/47: Port Forward State - Manual forwarding
Port 0/48: Port Forward State - Manual forwarding
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi jg75996,
Looks like port 0/47 and 0/48 not forwarding the packet any more. Could you show running config for M4100?
I want to double check the configurations.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hello EricZ,
Sorry for taking so long to respond to your last post.
Here is the running confirugration of the switch as requested:
(M4100-50G) #show running-config
!Current Configuration:
!
!System Description "M4100-50G ProSafe 48-port Gigabit L2+ Intelligent Edge Managed Switch, 10.0.2.20, B1.0.1.1"
!System Software Version "10.0.2.20"
!System Up Time "6 days 16 hrs 15 mins 50 secs"
!Additional Packages QOS,IPv6 Management,Routing
!Current SNTP Synchronized Time: Jun 22 16:17:08 2017 UTC
!
vlan database
vlan 200,500
vlan name 200 "Firewall-to-LinkBalancer"
vlan name 500 "RSPAN 1"
vlan routing 1 1
exit
configure
sntp server "0.north-america.pool.ntp.org"
sntp server "1.north-america.pool.ntp.org"
sntp server "2.north-america.pool.ntp.org"
clock timezone -4 minutes 0 zone "EST"
time-range
line console
exit
line telnet
exit
line ssh
exit
no storm-control broadcast
!
interface 0/1
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/2
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/3
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/4
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/5
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/6
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/7
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/8
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/9
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/10
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/11
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/12
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/13
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/14
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/15
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/16
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/17
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/18
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/19
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/20
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/21
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/22
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/23
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/24
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/25
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/26
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/27
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/28
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/29
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/30
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/31
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/32
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/33
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/34
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/35
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/36
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/37
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/38
storm-control broadcast level 5
no storm-control broadcast
description 'Uplink to VMware server @ 192.168.10.4'
vlan tagging 1
exit
interface 0/39
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/40
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/41
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/42
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/43
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/44
storm-control broadcast level 5
no storm-control broadcast
exit
interface 0/45
storm-control broadcast level 5
no storm-control broadcast
description 'RSPAN port FROM network tap of the Firewall'
no spanning-tree port mode
vlan pvid 500
vlan participation auto 1
vlan participation include 500
vlan tagging 500
exit
interface 0/46
storm-control broadcast level 5
no storm-control broadcast
description 'RSPAN port for SELKS IDS/IPS'
no spanning-tree port mode
vlan participation auto 1
vlan participation include 500
vlan tagging 500
exit
interface 0/47
storm-control broadcast level 5
no storm-control broadcast
description 'RSPAN port for OpenFPC'
no spanning-tree port mode
vlan participation auto 1
vlan participation include 500
vlan tagging 500
exit
interface 0/48
storm-control broadcast level 5
no storm-control broadcast
description 'RSPAN port for Ntop-NG'
no spanning-tree port mode
vlan pvid 500
vlan participation auto 1
vlan participation include 500
vlan tagging 500
exit
interface 0/49
storm-control broadcast level 5
no storm-control broadcast
description 'Trunk link to Netgear M4300 port 7/0/41'
vlan tagging 1
exit
interface 0/50
storm-control broadcast level 5
no storm-control broadcast
exit
interface vlan 1
routing
ip address dhcp
exit
exit
(M4100-50G) #
=======================================================================
Thank you for continuing to look into this issue!
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi jg75996,
Looks like for Port 0/46 and 0/47, missed configuration for 'vlan pvid 500'. Please add this command and try again.
If it still not ok, I suggest remove command 'vlan tagging 500' for port 0/45~0/48.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi Ericz,
I've added the 'vlan pvid 500' setting back into ports 0/46, 0/47 and 0/48. Cleared the stats on the ports and checked back later in the day after 5 hours.
Here are the results:
Port 0/45: Total Packets received without Errors - 37319568; Packets transmitted without Errors - 1365
Port 0/46: Disconnected.
Port 0/47: Total Packets received without Errors - 0; Packets transmitted without Errors - 433454
Port 0/48: Total Packets received without Errors - 0; Packets transmitted without Errors - 433454.
Looks like it did no have the desired effect.
I will remove the 'vlan tagging 500' for those ports tomorrow.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Re-creating an RSPAN VLAN on an M4100-50G switch
Hi EricZ,
I ended up not taking out the 'vlan tagging 500' command for those ports, thinking it might affect traffic on the default VLAN, VLAN1.
What I did do, was re-enable RSPAN for VLAN 500, then went to Switching -> Ports, re-enabling STP mode for ports 0/45 - 0/48, and then disabling STP mode. After refreshing the statistics for those ports, I can see that packets are being duplicated again as before.
Not sure why I needed to do this type of procedure, but I am now seeing the traffic as I would like it to be.
Thank you for staying up on this topic until now.