- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Brute force attack on ReadyNAS 316
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Brute force attack on ReadyNAS 316
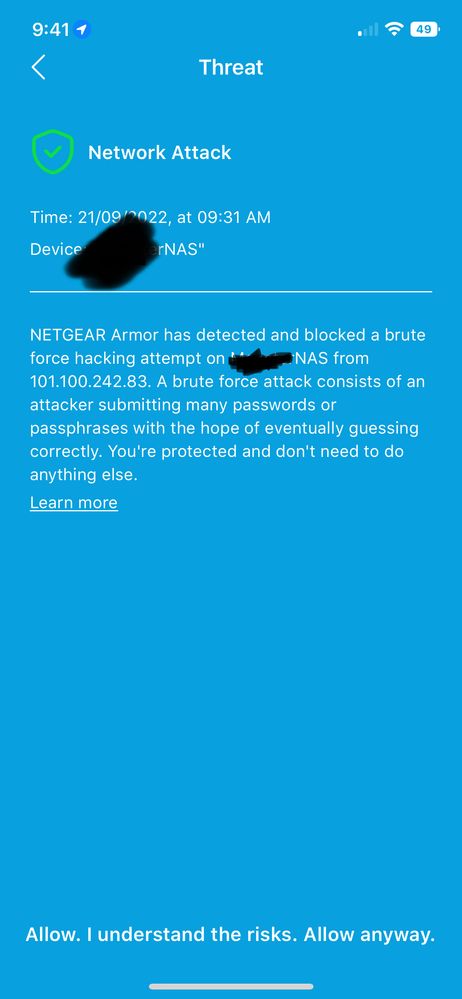
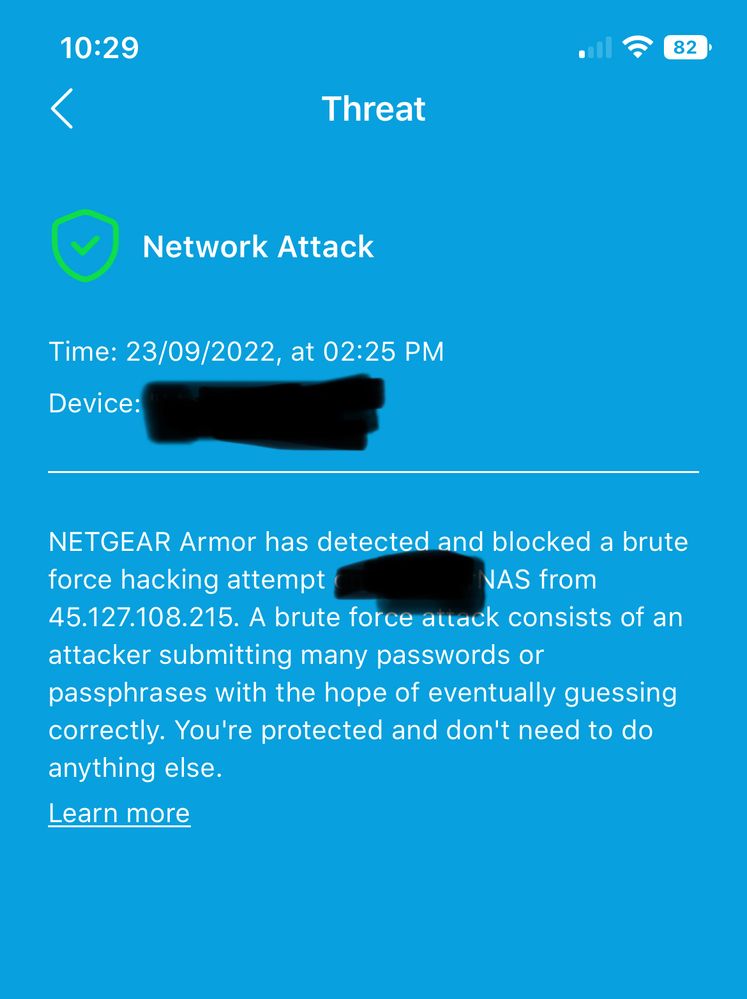
im been getting these alerts from Netgear Armor
my setup : orbi rbr850 and readynas 316
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
@neoprodigy wrote:
im been getting these alerts from Netgear Armor
my setup : orbi rbr850 and readynas 316
- Are you forwarding any ports to the NAS from the router?
- Is the upnp service enabled on the router?
FWIW, the IP address in your picture is in Singapore.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
1. dont think so
2. dont think so
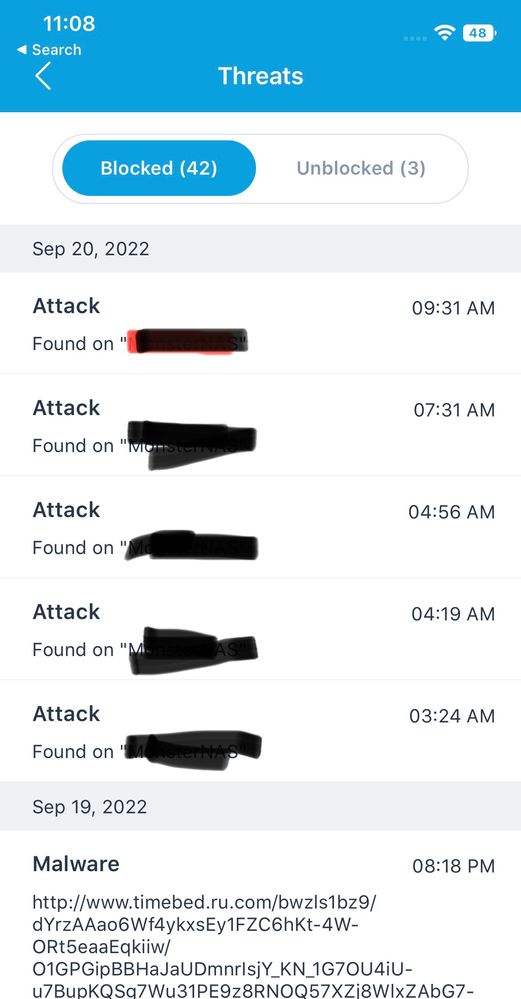
I check my netgear armor been constant attack. and they are all different ip addresses.
let me know what I need to do. thanks
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
@neoprodigy wrote:
1. dont think so
2. dont think so
You need to know for sure.
Go into the Orbi web ui. Select "advanced" at the top, and then select "advanced" again from the side menu.
- Select UPnP from the left menu. If "Turn UPnP" is checked, then uncheck it and select "Apply".
- Then select Port Forwarding/Port Triggering from the same left menu. See if there is anything forwarded to the NAS. Make sure you click "Port Triggering" after you've checked "Port forwarding".
@neoprodigy wrote:
let me know what I need to do. thanks
Also, let us know what apps are running on the NAS. A torrent app is one possible vector for these attacks (but there could be others).
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
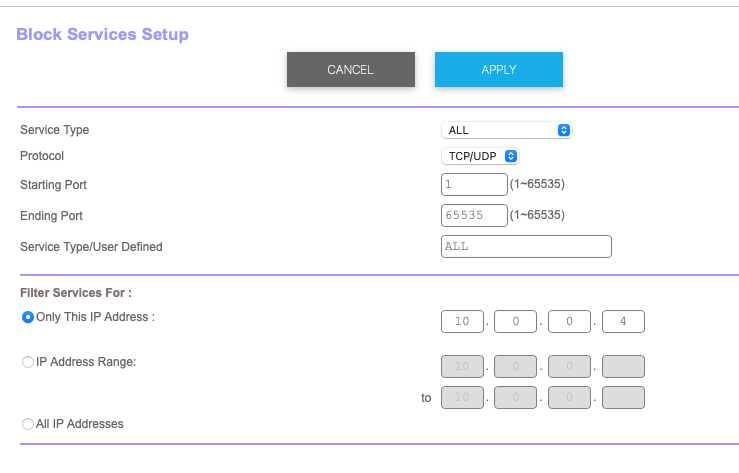
seem like this one works?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
@neoprodigy wrote:
seem like this one works?
Did you check the upnp and forwarding/triggering as I suggested?
Also, did you look at the apps you installed on the NAS? Any torrent app could expose you to these attacks, and perhaps others as well.
Blocking all services is a bit extreme. You are blocking both NTP (time synchronization), and check-for-updates. While you could do this as a stop-gap, it would be better to understand what is allowing these attacks in the first place, and close the underlying vulnerability.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
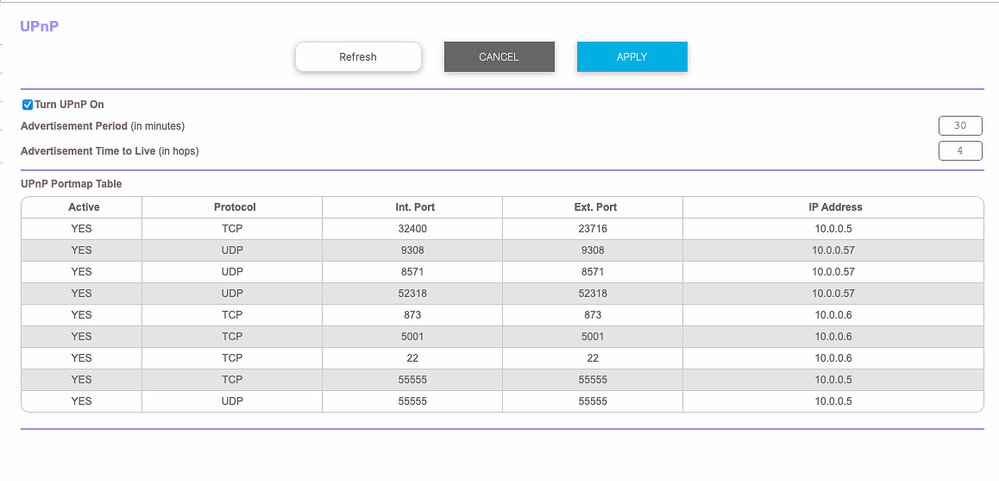
1. I dont see 10.0.0.4 using UPnP
10.0.0.5 = plex server
10.0.0.6 = synology nas
10.0.0.57 = PS5
2. no apps running
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
@neoprodigy wrote:
1. I dont see 10.0.0.4 using UPnP
2. no apps running
Good. And nothing under port forwarding or port triggering?
Also, do you have ReadyCloud or other cloud services running on the NAS?
Unfortunately, Armor doesn't seem to be providing any information on what ports the attackers are trying to reach.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
where do I disable those?
"ReadyCloud or other cloud services running on the NAS?"
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
@neoprodigy wrote:
where do I disable those?
"ReadyCloud or other cloud services running on the NAS?"
Look on the cloud page of the web ui.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
I think those are all off...
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
I closed everything and this still came up????
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
Maybe contact Armor and see if they can give you any more tangible information on the exact attack?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
It would be best to apply the latest FW to your NAS which has fixes for security vulnerabilities. This will enhance the NAS security also, uPnP lets devices on LAN to discover each other which might be causing for the attack to show up though the NAS is not listed as shown.
If ever you update to the latest FW version 6.10.8, please let us know if you are still getting that message.
HTH
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
I did an update yesterday... and I still get the brute force attack
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
@neoprodigy wrote:
I did an update yesterday... and I still get the brute force attack
I suggest disabling upnp in the router as a test. See if that eliminates the messages.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
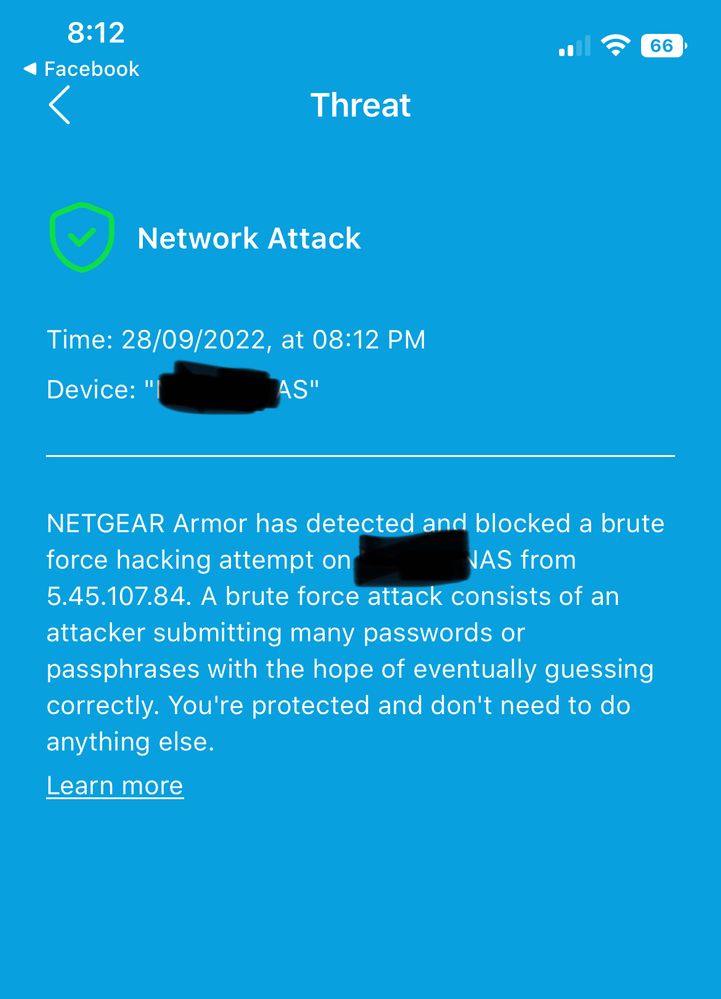
Re: Brute force attack on ReadyNAS 316
it didnt work.. same message.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
@neoprodigy wrote:
it didnt work.. same message.
Do you use ReadyCloud on the NAS?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Brute force attack on ReadyNAS 316
@neoprodigy wrote:
seem like this one works?
Depends for what. First we need to understand that this massive blocking does connect outgoing connections from your LAN, 10.0.0.5 (.4) or whatever the ReadyNAS has) to the outside world. All reports however show connection attempts from the wild Internet -to- some internal system, probably the ReadyNAS, probably a different device with exposed services. Cumbersome is the reports are not very (read: NOT) helpful at all. Sure, of this NAS would be affected by malware, the filter might block it to call home to some CCC system
Doe this vendor providing the Netgear Armor system (or Netgear) realize that these threat information is just scaring, does but help nothing in finding which system on the LAN is affected, which protocol (like tcp) or which service resp. port like http 80, https 443, ssh 22, ... is affected? Incredible! Was this ever tested and reviewed? @Blanca_O @KevinLiT - trigger your Armor PMs.
And then, worse than ever, @Blanca_O @KevinLiT the rputer design does still let even senior users like @StephenB expect this service blocking is a control over incoming connections: It's not! And late 2022, there is still no firewall control on these routers for Internet->LAN (beyond of the basic port forwarding).
The feature potential for these routers and armor would be huge. However, Netgear is still sleeping well, still promoting wonky features ...