- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
R7000 open vulnerability with unencrypted logon
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R7000 seems to accept unencrypted (plain text) logins? This is also a vulnerability notification from anyone running Bitdefender Box scanning router. When logging into router there is no encryption both LAN or from remote when editing router functions from IP "Genie not used", other routers have certificate or https abilities when logging into a router. Why?
Running latest firmware 1.0.9.26 but also same on older.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Well, maybe something NG will look at. Would be up them to make changes. I presume some of this would be customer or how many instances of bad experiences with this issue. Haven't seen a ton of issues where people are abusing this issue. May not be something to worry too much about, since this has been the norm regarding the UI for a long time. Up to the Mfrs though.
All Replies
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
I am no expert, but not sure what you expect? Even if there were encryption, it would be the same for all users, which defeats the purpose as if it were figured out, it would work for all users. However, Encryption can use certificates, but I think you'd have to buy one, and that probably would mean everyone would have to buy one to use the router to have unique encryption.
If you worry about this, get Wireshark and look at the TCP/IP packets that are sent out when you get e-mail.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
https to the router ip address
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
https://routerlogin.net (and of course http://routerlogin.net) works for me on R7800
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
Don't think so, I entered in Firefox https://192.168.1.1/, and this is what I get:
==========
Unable to connect
Firefox can’t establish a connection to the server at 192.168.1.1.
The site could be temporarily unavailable or too busy. Try again in a few moments.
If you are unable to load any pages, check your computer’s network connection.
If your computer or network is protected by a firewall or proxy, make sure that Firefox is permitted to access the Web.
============
http://192.168.1.1 works fine. Does it work for you?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
I tried https://routerlogin.net/ on Firefox and got the same error? http://routerlogin.net/ works fine? It even fails on MS Edge?
Does the OS have something to do with this? Or the F/W version? I'm on W10 V1709 and the V1.0.9.26 F/W.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
Be careful what you wish for. We all know how NG handles Firmware updates, right?
I'd rather have SMB1 usage removed from the R7000 and upgraded to SMB3 for instance than this. Have you ever used something like a TCP/IP packet capture program and see how your e-mail client works? Plain text... I'd more worry about that than how one works with the router.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
If your email client is sending and receiving emails unencrypted, then you only have yourself to blame (for being over a decade behind the times). All modern email clients support encrypted communications with the server, but only if you set it up that way!
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
True I guess, still use POP3... I'm old fashioned...
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
encryption for POP3 is very common -- look for that option in your email program (google it)
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
@IrvSpwrote:I'd rather have SMB1 usage removed from the R7000 and upgraded to SMB3 for instance than this.
Yes, both SMB 2.x and SMB 3.0 support, similar as already available on the R9000. Plus a WSD discovery client of course to make it visible in WIndows Explorer as a PC/Server properly.
@IrvSp wrote:Have you ever used something like a TCP/IP packet capture program and see how your e-mail client works? Plain text... I'd more worry about that than how one works with the router.
At least the recent Netgear Nighthawk firmware implemented SMTP client does allow using SMTP submission port like 587/TCP supporting TLS automatically - I hope this applies ot the R7000, too.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
Pretty sure logs in on the LAN side are only plain text log ins since it's a LAN side access. If remote management is enabled then of course HTTPS would be used using the public IP address and a pre-assinged port address. Web UI access log ins to the routers web page on the LAN side isn't needed. Unless you think someone on the LAN side is trying to gain access.
Most router Mfrs don't use HTTPS on the web UI log in. Maybe some newer models. I have 3 new NG routers. All use HTTP to access UI for the log in.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
@schumaku, yes, the logs are sent with port 587.
I just checked my Thunderbird setting, I'm using 587 there too. Also 995 out.
I was thinking back 'many many' years when I was managing a port of the old Netscape Navigator to another OS. Was checking what was going out using a packet sniffer. I was very surprised to see my UID, PW, and message go out in plain text. Old POP3 then. I'm OK now...
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
Most log ins are hidden. At least the PW is when you type it in. Dots are seen, not actual characters. Usually users who are managing the router is or should be alone if there typing in PWs.
I do see some Mfrs that have the option to hid or no hid the PW as well. It's up to the Mfr I presume to let the user choose this option.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
@SirThomaswrote:
But NG should fix this in a firmware update so that logon information is not easily seen even on LAN side.
We buy a product based on the product specifications on the box and the related documents like a data sheet. There is no word of a secured management interface.
@SirThomas wrote:
This is a security vulnerability, that and having to pay for product support from NG!
No, it's not a vulnerability. Well, the term "trusted network" is a commonly accepted mitigation. Making a https access and disable the http would make your "expensive" security system to shut up.
Of course, you are a happy camper at this point, too.
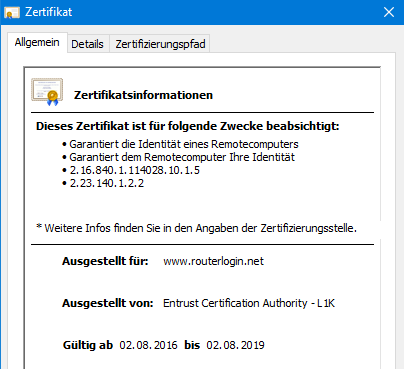
I'm not. Because I know that the most critical information in this "secure" connection is not secure enough: My router private key is well known. And so is the Entrust signed certificate. All similar routers out there make use of the same private key, the same certificate serial number, and the very same fingerprint.
This "green" https connection is not any better than the plain text http connection on my trusted network. But it's OK because it's my private network again. Figure.
And no - I'm not aware we pay NTGR for software maintenance, enhancements, new services, new features.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
I know. I know some don't understand the HTTP vs HTTPS and password field opertion and what it all means being on the LAN side of the router and what real vulnerabilities are.
@schumakuwrote:@FURRYe38, it does not matter if the UI does kind of hide the password field, or if there is some kind of obfuscation code in place.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R7000 open vulnerability with unencrypted logon
I'm sure most of the additional apps and features are not vulnerable as they use secure connections. Just having the UI access is debatable. Most routers Mfrs don't use HTTPS for the LAN side log in. Again, they do for WAN side access. I presume Mfr could make the log in more secure. However, on a average or daily basis, usually not needed. Are there a croud hanging around you while your trying to log in or have someone with nefarious ideas of trying to hack in to your routers log in the LAN side? How often does this happen? If they wanted in, they would just reset the router and blow the configuration away, if they had physical access.
Just saying.
• What is the difference between WiFi 6 and WiFi 7?
• Yes! WiFi 7 is backwards compatible with other Wifi devices? Learn more