- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Re: R8000P FRAGGLE ATTACK FROM UNKNOW every 2mins 5 seconds
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
R8000P FRAGGLE ATTACK FROM UNKNOW every 2mins 5 seconds
Amongst the general chatter in the log, my R8000P AC4000 has entries every 2 minutes and 5 seconds :-
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Thursday, Sep 09,2021 12:07:21
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Thursday, Sep 09,2021 12:05:16
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Thursday, Sep 09,2021 12:03:11
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Thursday, Sep 09,2021 12:01:06
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Thursday, Sep 09,2021 11:59:01
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Thursday, Sep 09,2021 11:56:56
The port number does vary.
I am connected to a Vigor 130 modem and found that this has the IGMP_PROXY set to enabled with a period of 125000ms (or 2 minutes and 5 seconds)!
Coincidence IT SEEMS however!!!!
Disabling the IGMP_PROXY on the Vigor 130 does not stop the log entries on my R8000P.
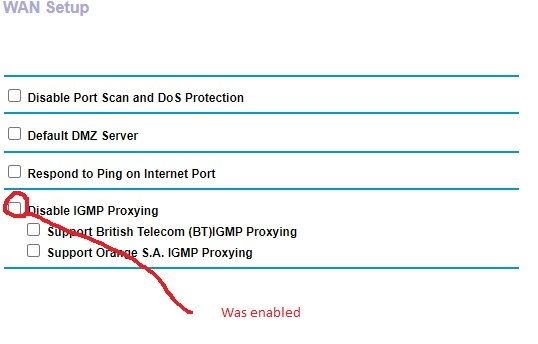
However, using this info I checked the settings on my R8000P and under WAN there is a "Disable IGMP_Proxying" box which was ticked. (So seemingly the IGMP proxy was disabled?!?!)
Unticking this box stops the "Fraggle Attack messages from appearing in the log every 2 minutes and 5 seconds. I also left the other 2 sub boxes unticked.
There are still other warning messages but seemingly without any pattern to them. The log may now actually be of some use now that it is not full of junk.
It seems to be slightly counter intuitive that unchecking the box and therefore enabling the proxy has a this effect unless this box is mislabeled and uncheckng it actually disables the proxy rather than the double negative.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R8000P FRAGGLE ATTACK FROM UNKNOW every 2mins 5 seconds
Unfortunately this was a red herring - I do not know why this IGMP setting seemed to temporarily fixed the log entries but looking back a few days later they are back again. Every 2 minute and 5 seconds ..............
I'll have to back track to see if I changed anything else at the same time which may have accounted for it.
Doh!!
@Scorpio123 wrote:Amongst the general chatter in the log, my R8000P AC4000 has entries every 2 minutes and 5 seconds :-
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Thursday, Sep 09,2021 12:07:21
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Thursday, Sep 09,2021 12:05:16
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Thursday, Sep 09,2021 12:03:11
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Thursday, Sep 09,2021 12:01:06
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Thursday, Sep 09,2021 11:59:01
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Thursday, Sep 09,2021 11:56:56
The port number does vary.
I am connected to a Vigor 130 modem and found that this has the IGMP_PROXY set to enabled with a period of 125000ms (or 2 minutes and 5 seconds)!
Coincidence IT SEEMS however!!!!
Disabling the IGMP_PROXY on the Vigor 130 does not stop the log entries on my R8000P.
However, using this info I checked the settings on my R8000P and under WAN there is a "Disable IGMP_Proxying" box which was ticked. (So seemingly the IGMP proxy was disabled?!?!)
Unticking this box stops the "Fraggle Attack messages from appearing in the log every 2 minutes and 5 seconds. I also left the other 2 sub boxes unticked.
There are still other warning messages but seemingly without any pattern to them. The log may now actually be of some use now that it is not full of junk.
It seems to be slightly counter intuitive that unchecking the box and therefore enabling the proxy has a this effect unless this box is mislabeled and uncheckng it actually disables the proxy rather than the double negative.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R8000P FRAGGLE ATTACK FROM UNKNOW every 2mins 5 seconds
What Firmware version is currently loaded?
What is the Mfr and model# of the Internet Service Providers modem/ONT the NG router is connected too?
So you don't see a IP address where UNKNOWN is displayed anywhere in the logs?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R8000P FRAGGLE ATTACK FROM UNKNOW every 2mins 5 seconds
Hi
I am on the latest FW according to the site - V1.4.1.82_1.3.40
The modem is a Draytek Vigor 130.
Correct, for these particular attack messages you see no IP address.
The original problem I had was a FRAGGLE attack every 10 seconds from source UNKNOW but always a different port.
I tracked this down to a 'feature' of the Vigor130 sending status updates to the LAN. Disabling this management option on the Vigor 130 stopped them. I found those by using Wireshark on the modem itself and matching the ports to the Netgear log. (Only useful if you own a Draytek router as well)
With those gone I then saw the every 2 mins 5 second FRAGGLE warnings from source UNKNOW. (I then had a red herring where I thought I had stoppped them ONCE but they just stopped of their own accord for a while - see later note)
However after months and month of them being there - currently there are none of these in the log!!
There are other attacks with IP addresses listed now but with no fixed time pattern. (See below)
During the process of investigating this, the modem/router was rebooted and assigned a new dynamic IP address by my ISP (B.T.) and I now suspect that some ranges of IP addresses are just targeted especially those of big ISP providers. So those FRAGGLE attacks were real but not possible to say the source (UNKNOW). I think my current IP address is a 'quiet one'.
John
[DHCP IP: (192.168.1.20)] to MAC address E4:04:39:EA:A3:73, Saturday, Sep 18,2021 10:13:57
[DoS attack: snmpQueryDrop] from source 192.241.220.147,port 41643 Saturday, Sep 18,2021 10:07:11
[DHCP IP: (192.168.1.24)] to MAC address 10:C3:7B:6D:4E:C1, Saturday, Sep 18,2021 10:06:54
[DoS attack: RST Scan] from source 147.135.36.175,port 443 Saturday, Sep 18,2021 09:48:53
[DoS attack: RST Scan] from source 147.135.36.175,port 443 Saturday, Sep 18,2021 09:47:49
[DoS attack: RST Scan] from source 147.135.36.175,port 443 Saturday, Sep 18,2021 09:45:25
[DoS attack: RST Scan] from source 147.135.36.175,port 443 Saturday, Sep 18,2021 09:44:46
[DoS attack: RST Scan] from source 147.135.36.175,port 443 Saturday, Sep 18,2021 09:44:24
[DoS attack: RST Scan] from source 147.135.36.175,port 443 Saturday, Sep 18,2021 09:41:28
[DoS attack: RST Scan] from source 147.135.36.175,port 443 Saturday, Sep 18,2021 09:41:16
[DoS attack: RST Scan] from source 86.189.96.24,port 443 Saturday, Sep 18,2021 09:34:00
[DoS attack: RST Scan] from source 54.171.54.67,port 7070 Saturday, Sep 18,2021 09:30:02
[DoS attack: RST Scan] from source 176.34.142.148,port 7070 Saturday, Sep 18,2021 09:30:02
[DoS attack: RST Scan] from source 54.171.54.67,port 7070 Saturday, Sep 18,2021 09:30:01
[DoS attack: RST Scan] from source 176.34.142.148,port 7070 Saturday, Sep 18,2021 09:30:01
[DoS attack: RST Scan] from source 54.172.45.244,port 6871 Saturday, Sep 18,2021 09:27:49
[DoS attack: RST Scan] from source 151.101.61.16,port 443 Saturday, Sep 18,2021 09:04:00
[DoS attack: RST Scan] from source 52.85.142.25,port 443 Saturday, Sep 18,2021 09:04:00
[DoS attack: RST Scan] from source 52.31.202.1,port 443 Saturday, Sep 18,2021 08:45:29
[DoS attack: RST Scan] from source 52.54.8.68,port 443 Saturday, Sep 18,2021 08:43:54
[DoS attack: RST Scan] from source 81.130.98.57,port 443 Saturday, Sep 18,2021 08:04:50
[DoS attack: RST Scan] from source 45.57.90.1,port 443 Saturday, Sep 18,2021 08:04:50
[DoS attack: RST Scan] from source 143.204.197.16,port 443 Saturday, Sep 18,2021 08:00:00
[DoS attack: RST Scan] from source 86.189.96.24,port 443 Saturday, Sep 18,2021 07:59:30
[DoS attack: RST Scan] from source 34.251.215.151,port 7070 Saturday, Sep 18,2021 07:39:56
[DoS attack: RST Scan] from source 44.195.21.183,port 6113 Saturday, Sep 18,2021 07:33:22
etc
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R8000P FRAGGLE ATTACK FROM UNKNOW every 2mins 5 seconds
Is the modem running in bridge mode or is it handling the ISP connection?
I would presume that your Draytrek modem had a role ot play in that then. Seems like if your not seeing these anymore then the problem seem to have disappeared...for now.
Might try a different modem and see if the issue appears again...
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R8000P FRAGGLE ATTACK FROM UNKNOW every 2mins 5 seconds
The modem is in the default PPPoE pass through mode with the NG in router mode passing the BT credentials to it.
The diference between the 2 FRAGGLE attacks was that the 10 second ones had different ports each time and the traffic was visible on the LAN connection of the modem using wireshark and then in the router logs so was evidently being generated in the modem but reported by the router as a FRAGGLE attack.
The 2 min 5 second ones had no corresponding traffic on the LAN connection of the modem so seemed to be coming from the WAN.
As far as I can tell no configuration changes have now been made on either device and yet for now the FRAGGLE reports have stopped.
They stopped once before briefly when I thought something I had changed had an effect but after further reboots they came back. The only distinguishable difference is the change of the WAN IP address after the modem/router reboots. If the direct cause was the modem or router then I would expect them still to be there. (I've always hated intermittent problems ....)
I've taken a note of the current IP and when it changes again, see if the FRAGGLE reports come back. We've had a few dropped VDSL connections recently so I may not have to wait long ....
I'm not overly disturbed by the issue - just intrigued mainly. If rebooting to a different IP does have an effect then swapping modems could give a false indication (and I don't have one to hand) - unless the reports reappear with the new modem (and if so I'm not sure that would help track the cause anyway). I think I had a BT HH5 initially - not sure if I can configure that to just being a modem but at the moment it is lost in the loft somewhere.....
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R8000P FRAGGLE ATTACK FROM UNKNOW every 2mins 5 seconds
Well gues what ....... I forgot the modem was connected to a hub which was on a separate powerstrip so I could connect the ethernet to a laptop and the router and unplugged the power strip and severed the internet connection, so I now have a new dynamic IP address after the modem reconnected.
and the FRAGGLE attacks are back in the log every 2mins5secs...... Hee, hee!
[DoS attack: Fraggle Attack] from source UNKNOW,port 7070 Monday, Sep 20,2021 14:02:53
[DoS attack: Fraggle Attack] from source UNKNOW,port 7070 Monday, Sep 20,2021 14:00:48
[DoS attack: Fraggle Attack] from source UNKNOW,port 7070 Monday, Sep 20,2021 13:58:43
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Monday, Sep 20,2021 13:56:38
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Monday, Sep 20,2021 13:54:33
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Monday, Sep 20,2021 13:52:28
[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Monday, Sep 20,2021 13:50:23
[[DoS attack: Fraggle Attack] from source UNKNOW,port 443 Monday, Sep 20,2021 13:48:18
old IP address was an 86.156.x.y, new is 109.158.j.k
• What is the difference between WiFi 6 and WiFi 7?
• Yes! WiFi 7 is backwards compatible with other Wifi devices? Learn more