- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Re: R9000 block ssl-vpn connection ( port 443)
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
i have issue with connecting to SSL VPN on port 443,
i have R9000 router,
i use firmware v1.0.1.36
When i tryed to connect to my work with Cisco Anyconnect that use port 443 i get denied.
When i check in logs i recognize theat Router thinking that this IP is Dos Attack: RST Scan
[DoS Attack: RST Scan] from source: XX.XXX.XX.XXX, port 443, Sunday, May 28, 2017 09:20:18
[DoS Attack: RST Scan] from source: XX.XXX.XX.XXX, port 443, Sunday, May 28, 2017 09:18:04
Of course the XX.XXX.XX.XXX is public ip that i'm trying to connect.
Without netgear router evrything work as expected.
Thanks,
Ruslan.
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
Just to Update,
Reload the router and SSL VPN worked correctly.
May be was some issue with MTU like TheEther say...
Will continues to monitor if it will happen again will update.
Thanks for you all for trying to help.
Ruslan.
All Replies
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
What is the ISP Modem and model?
Set up any Port Fowarding rules set up on the router?
Might disable any wan side protection features and test.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Hi,
thanks for reply.
ISP Modem is D-link ( bridge mode)
no Port Fowrading rules exist on the router.
R9000 don't have any option to disable protetion.
i think the algorith that R9000 use to recognize DDOS is incorrect.
Ruslan.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
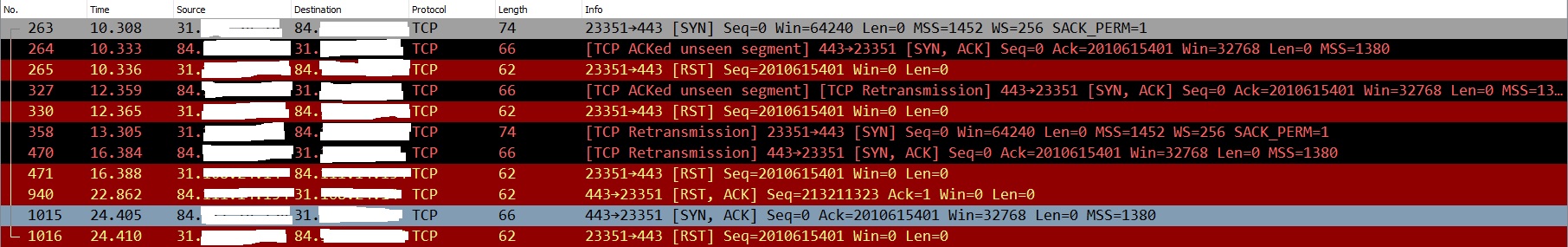
we can see on the packet capture that was take from the router,
R9000 Reset the connection after get response from remote peer 84.XXX.XXX.XXX
Source 31.XX.XXX.XXX
i think if i will restart the router everything wil work correctly...but i don't belive is such solutions.:)
few weeks ago everything worked correctly.
If need more info update me.
Thanks.
Ruslan.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Oh boy, the Wireshark trace is a tale of dueling TCP RST exchanges.
You can see in frame 264 that the remote peer has replied with the wrong ACK number (2010615401) in response to the local host's TCP SYN request in frame 263. Wireshark flags this as ACKed unseen segment. The local host immediately sends a TCP RST (Reset) to tear down the connection in frame 265.
The remote peer retransmits frame 264 again as frame 327 in spite of the TCP RST in frame 265. It's almost as if the remote peer didn't receive the RST. The local host sends another RST in frame 330. The remote peer does this two more times in frame 470 and 1015. Each time the local host sends a RST in 471 and 1016.
Frame 940 is where we see a RST out of the blue from the remote peer. This RST doesn't seem to match up with any of the other frames. Frame 940 is probably what Netgear is flagging as a RST Scan.
Based on the above, it seems to me that the remote peer at 84.xxx.xxx.xxx is not behaving properly, although I guess we can't rule out the possibility that the router is totally mangling the traffic. It would be interesting to see simultaneous Wireshark captures from both sides of the router (i.e. WAN and LAN). This would provide insight into what the router is doing to the traffic pre- and post-NAT.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Something changed somewhere if it had been working...
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Hi The Ether,
thanks for answer,
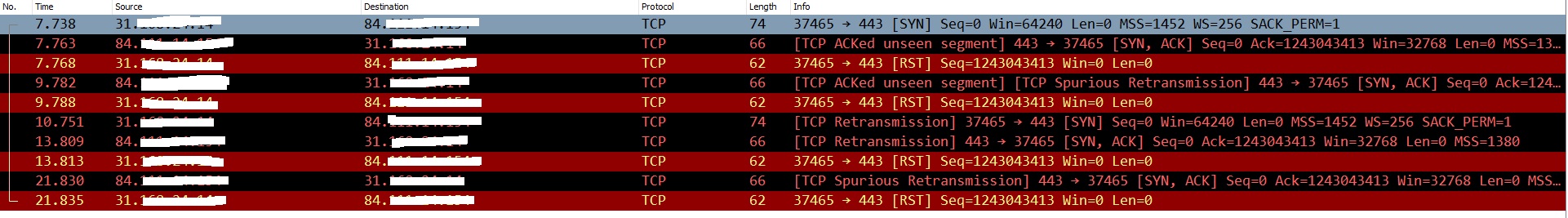
of course i can provide LAN and WAN capture on the router,
please see picture below:
WAN:
My Home IP:31.XXX.XXX.XXX
Remote Peer: 84.XX.XXX.XXX
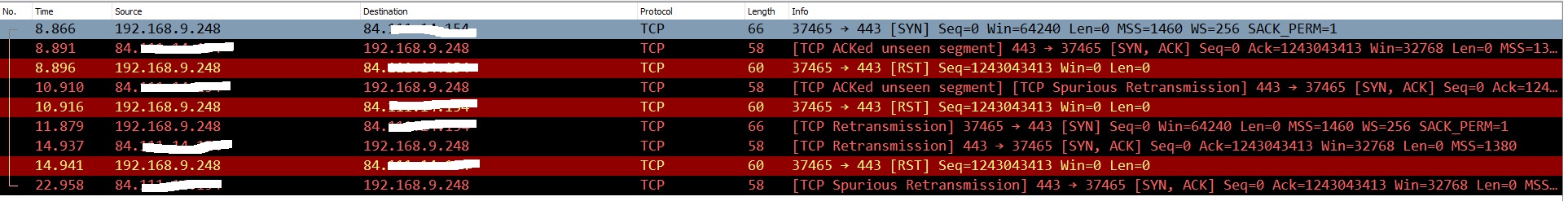
LAN:
PC:192.168.9.248
Remote Peer: 84.XXX.XXX.XXX
Of couse i have acces to remote peer it's Cisco ASA Firewall,
same pc 4G or modem directly connected i can succesfully conect to vpn.
i also added some files from R9000 ( basic_debug_log,console.log)
May be it will help.
Thanks for help,
Ruslan.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Basic_debug_log:
ath0 Link encap:Ethernet HWaddr 9C:3D:CF:E2:B1:23
inet6 addr: fe80::9e3d:cfff:fee2:b123/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:12678460 errors:0 dropped:0 overruns:0 frame:0
TX packets:28120983 errors:46868 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:2126025531 (1.9 GiB) TX bytes:273754668 (261.0 MiB)
ath1 Link encap:Ethernet HWaddr 9C:3D:CF:E2:B1:21
inet6 addr: fe80::9e3d:cfff:fee2:b121/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:42582219 errors:1 dropped:1 overruns:0 frame:0
TX packets:67680490 errors:74509 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:3272440133 (3.0 GiB) TX bytes:1880228954 (1.7 GiB)
br0 Link encap:Ethernet HWaddr 9C:3D:CF:E2:B1:21
inet addr:192.168.9.254 Bcast:192.168.9.255 Mask:255.255.255.0
inet6 addr: fe80::9e3d:cfff:fee2:b121/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:107647059 errors:0 dropped:652 overruns:0 frame:0
TX packets:166335214 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:30349962889 (28.2 GiB) TX bytes:189145974449 (176.1 GiB)
brwan Link encap:Ethernet HWaddr 9C:3D:CF:E2:B1:22
inet6 addr: fe80::9e3d:cfff:fee2:b122/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:160004128 errors:0 dropped:0 overruns:0 frame:0
TX packets:99264210 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:187053650462 (174.2 GiB) TX bytes:30812712705 (28.6 GiB)
eth0 Link encap:Ethernet HWaddr 9C:3D:CF:E2:B1:25
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
eth1 Link encap:Ethernet HWaddr 9C:3D:CF:E2:B1:21
inet6 addr: fe80::9e3d:cfff:fee2:b121/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:58972233 errors:0 dropped:0 overruns:0 frame:0
TX packets:80139346 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1367066474 (1.2 GiB) TX bytes:2512704123 (2.3 GiB)
eth2 Link encap:Ethernet HWaddr 9C:3D:CF:E2:B1:22
inet6 addr: fe80::9e3d:cfff:fee2:b122/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:160004128 errors:0 dropped:0 overruns:0 frame:0
TX packets:99264219 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2370056734 (2.2 GiB) TX bytes:3667115706 (3.4 GiB)
ethlan Link encap:Ethernet HWaddr 9C:3D:CF:E2:B1:21
inet6 addr: fe80::9e3d:cfff:fee2:b121/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:58972233 errors:0 dropped:13785 overruns:0 frame:0
TX packets:80139340 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:18546935658 (17.2 GiB) TX bytes:80924567912 (75.3 GiB)
ethwan Link encap:Ethernet HWaddr 9C:3D:CF:E2:B1:22
inet6 addr: fe80::9e3d:cfff:fee2:b122/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:160004128 errors:0 dropped:0 overruns:0 frame:0
TX packets:99264213 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:187053650462 (174.2 GiB) TX bytes:30812712935 (28.6 GiB)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:65536 Metric:1
RX packets:34721163 errors:0 dropped:0 overruns:0 frame:0
TX packets:34721163 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1391686211 (1.2 GiB) TX bytes:1391686211 (1.2 GiB)
ppp0 Link encap:Point-to-Point Protocol
inet addr:XX.XXX.XX.XX P-t-P:212.179.37.1 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1492 Metric:1
RX packets:14162226 errors:0 dropped:0 overruns:0 frame:0
TX packets:10244988 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:3
RX bytes:15916442983 (14.8 GiB) TX bytes:1913778140 (1.7 GiB)
tap0 Link encap:Ethernet HWaddr 22:93:B8:B4:F9:07
inet6 addr: fe80::2093:b8ff:feb4:f907/64 Scope:Link
UP BROADCAST RUNNING PROMISC MULTICAST MTU:1500 Metric:1
RX packets:946202 errors:0 dropped:285 overruns:0 frame:0
TX packets:2155258 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:616788875 (588.2 MiB) TX bytes:480648553 (458.3 MiB)
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:192.168.10.1 P-t-P:192.168.10.1 Mask:255.255.255.0
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:82 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:0 (0.0 B) TX bytes:6920 (6.7 KiB)
wifi0 Link encap:Ethernet HWaddr 9C:3D:CF:E2:B1:23
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:539
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
Interrupt:166 Memory:f1c00000-f1e00000
wifi1 Link encap:Ethernet HWaddr 9C:3D:CF:E2:B1:21
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:539
RX bytes:0 (0.0 B) TX bytes:0 (0.0 B)
Interrupt:167 Memory:f2000000-f2200000
MemTotal: 1030732 kB
MemFree: 815012 kB
Buffers: 10416 kB
Cached: 28372 kB
SwapCached: 0 kB
Active: 20796 kB
Inactive: 26404 kB
Active(anon): 8772 kB
Inactive(anon): 3996 kB
Active(file): 12024 kB
Inactive(file): 22408 kB
Unevictable: 0 kB
Mlocked: 0 kB
HighTotal: 270336 kB
HighFree: 229356 kB
LowTotal: 760396 kB
LowFree: 585656 kB
SwapTotal: 0 kB
SwapFree: 0 kB
Dirty: 0 kB
Writeback: 0 kB
AnonPages: 8620 kB
Mapped: 4008 kB
Shmem: 4356 kB
Slab: 54340 kB
SReclaimable: 2984 kB
SUnreclaim: 51356 kB
KernelStack: 1560 kB
PageTables: 1224 kB
NFS_Unstable: 0 kB
Bounce: 0 kB
WritebackTmp: 0 kB
CommitLimit: 515364 kB
Committed_AS: 287520 kB
VmallocTotal: 245760 kB
VmallocUsed: 22244 kB
VmallocChunk: 171148 kB
AnonHugePages: 0 kB
HugePages_Total: 0
HugePages_Free: 0
HugePages_Rsvd: 0
HugePages_Surp: 0
Hugepagesize: 2048 kB
PID Uid VmSize Stat Command
1 root 356 S init
2 root SW [kthreadd]
3 root SW [ksoftirqd/0]
5 root SW< [kworker/0:0H]
6 root SW [kworker/u8:0]
7 root SW [migration/0]
8 root SW [rcu_bh]
9 root SW [rcu_sched]
10 root SW [migration/1]
11 root SW [ksoftirqd/1]
13 root SW< [kworker/1:0H]
14 root SW [migration/2]
15 root SW [ksoftirqd/2]
17 root SW< [kworker/2:0H]
18 root SW [migration/3]
19 root SW [ksoftirqd/3]
21 root SW< [kworker/3:0H]
22 root SW< [khelper]
23 root SW [kdevtmpfs]
24 root SW< [writeback]
25 root SW< [bioset]
26 root SW< [kblockd]
27 root SW [kworker/3:1]
28 root SW< [ata_sff]
29 root SW [khubd]
30 root SW [kworker/u8:1]
37 root SW< [md]
38 root SW< [edac-poller]
39 root SW [kworker/2:1]
40 root SW< [rpciod]
41 root SW< [kvm_arch_timer]
43 root SW [kswapd0]
44 root SWN [khugepaged]
45 root SW [fsnotify_mark]
46 root SW [ecryptfs-kthrea]
47 root SW< [nfsiod]
48 root SW< [cifsiod]
49 root SW< [xfsalloc]
50 root SW< [xfs_mru_cache]
51 root SW< [xfslogd]
52 root SW< [crypto]
70 root SW [kworker/1:1]
71 root SW [nvme]
72 root SW< [fd882000.spi]
73 root SW< [kpsmoused]
110 root SW< [deferwq]
111 root SW [ubi_bgt0d]
112 root SW< [kworker/0:1H]
116 root SW< [kworker/1:1H]
124 root SW< [kworker/2:1H]
181 root SW [ubifs_bgt0_5]
191 root SW [ubi_bgt1d]
208 root SW [ubifs_bgt1_0]
240 root 132 S /bin/sh /etc/init.d/rcS S boot
242 root 356 S logger -s -p 6 -t sysinit
248 root 88 S init
264 root 416 S /bin/sh /sbin/cpu_temperature
561 root 268 S klogd
565 root SW< [kworker/3:1H]
566 root 560 S /bin/datalib
606 root 276 S /sbin/watchdog -t 5 /dev/watchdog
612 root SW< [cfg80211]
629 root SW< [wil6210_wmi]
630 root SW< [wil6210_service]
631 root SW [irq/147-wil6210]
636 root SW< [bond0]
740 root 528 S /sbin/hotplug2 --override --persistent --set-rules-fi
894 root 76 S /sbin/ubusd
1108 root 244 S /usr/bin/detcable 2
2132 root 352 S udhcpd /tmp/udhcpd.conf
3500 root 268 S /usr/sbin/miniupnpd
3768 root 304 S /usr/sbin/ntpclient
3808 root 376 S crond -c /tmp/etc/crontabs -T GMT+8
4375 root SW< [alloc_task_wque]
4580 root 1724 S /usr/sbin/openvpn /tmp/openvpn/server_tap.conf
4583 root 576 S /usr/sbin/openvpn /tmp/openvpn/server_tun.conf
4958 root 316 S /usr/sbin/net-scan
4962 root 272 S lld2d br0
5143 root SW< [alloc_task_wque]
6265 root 856 S hostapd -P /var/run/wifi-ath1.pid -B /var/run/hostapd
6267 root 296 S hostapd_cli -i ath1 -P /var/run/hostapd_cli-ath1.pid
6740 root 856 S hostapd -P /var/run/wifi-ath0.pid -B /var/run/hostapd
6742 root 296 S hostapd_cli -i ath0 -P /var/run/hostapd_cli-ath0.pid
8060 root 356 S /usr/sbin/uhttpd -h /www -r R9000 -x /cgi-bin -t 70 -
8081 root 876 S /usr/sbin/uhttpd -h /www -r R9000 -x /cgi-bin -t 70 -
8083 root 44 S inetd
8119 root 276 S acld
8120 root 68 S aclhijackdns
8307 root 48 S /usr/bin/hd-idle -i 1800
8447 root SW [ telnetDBGD ]
8448 root SW [ acktelnetDBGD ]
8449 root SW [checkSBusTimeou]
8451 root SW [NU TCP]
8452 root SW [NU UDP]
8453 root 160 S /sbin/KC_BONJOUR
8454 root 96 S /sbin/KC_PRINT
8542 root 48 S potval
8590 root SW< [vport-mii]
8781 root 244 S /sbin/traffic_meter
8826 root 48 S /usr/sbin/telnetenable
8863 root 440 S /bin/sh /sbin/11ad_linkloss_wd.sh
8942 root 244 S /usr/sbin/ntgrddns -c /tmp/ntgrdns.conf
9741 root 540 S /usr/sbin/dbus-daemon --system
9748 root 1008 S avahi-daemon: registering [R-Home.local]
10157 root SW [kworker/0:2]
10206 root 1208 S N /usr/sbin/afpd -F /etc/netatalk/afpd.conf -P /var/run
10451 root 424 S /bin/sh /usr/sbin/check_time_machine
11846 root SW [kworker/1:0]
13151 root 364 S /opt/xagent/xagent -w -d --ca_file /opt/xagent/certs/
13153 root 2080 S /opt/xagent/xagent -w -d --ca_file /opt/xagent/certs/
18507 root 108 S sleep 60
19288 root 440 S /bin/sh /sbin/fan_on_off 80 70 90 80 90 80 85 70 85 7
19487 root SW [kworker/2:0]
19957 root 108 S sleep 60
20766 root 112 S sleep 5
20840 root SW [kworker/3:0]
20985 root 108 S sleep 1
21110 root 740 S /usr/sbin/net-cgi
21117 root 356 S /bin/sh -c /sbin/enable_collect_console_log.sh >/dev/
21121 root 356 S /bin/sh /sbin/enable_collect_console_log.sh
21123 root 360 S /bin/sh /sbin/basic_log.sh
21125 root 360 S /bin/sh /sbin/console_log.sh
21126 root 360 S /bin/sh /sbin/wireless_log.sh
21127 root 424 S /bin/sh /sbin/capture_packet.sh
21135 root 112 S sleep 1
21150 root 360 R ps
21155 root 112 S sleep 300
21160 root sleep 300
21163 root sleep 300
21165 root sleep 300
21166 root 356 S sh -c /usr/sbin/ethtool eth0 |grep "Duplex"|cut -d :
24182 root SW [kworker/0:1]
28495 root 276 S syslogd -m 0 -T GMT+8 -c 1083
32078 root 336 S pppd call dial-provider updetach
32118 guest 408 S /usr/sbin/dnsmasq --except-interface=lo -r /tmp/resol
total used free shared buffers
Mem: 1030732 216296 814436 0 10416
Swap: 0 0 0
Total: 1030732 216296 814436
nameserver 192.117.235.237
nameserver 62.219.186.7
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default bzq-179-37-1.cu 0.0.0.0 UG 0 0 0 ppp0
192.168.9.0 * 255.255.255.0 U 0 0 0 br0
192.168.10.0 * 255.255.255.0 U 0 0 0 tun0
212.179.37.1 * 255.255.255.255 UH 0 0 0 ppp0
239.0.0.0 * 255.0.0.0 U 0 0 0 br0
IP address HW type Flags HW address Mask Device
192.168.9.228 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.6 0x1 0x0 00:15:65:98:1d:ab * br0
192.168.9.249 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.243 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.214 0x1 0x2 00:50:56:94:fb:0d * br0
192.168.9.29 0x1 0x0 00:34:da:8a:29:52 * br0
192.168.9.245 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.8 0x1 0x0 f8:16:54:cb:79:2e * br0
192.168.9.229 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.7 0x1 0x2 b8:86:87:48:dc:a3 * br0
192.168.9.4 0x1 0x2 f0:99:bf:31:35:da * br0
192.168.9.252 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.30 0x1 0x0 00:34:da:8a:29:52 * br0
192.168.9.241 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.246 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.100 0x1 0x2 98:90:96:dc:37:26 * br0
192.168.9.50 0x1 0x2 00:0c:29:11:eb:b4 * br0
192.168.9.234 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.155 0x1 0x2 02:ba:d0:88:10:20 * br0
192.168.9.9 0x1 0x2 00:ff:5f:2c:47:59 * br0
192.168.9.230 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.251 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.5 0x1 0x0 5c:a3:9d:41:8e:b4 * br0
192.168.9.248 0x1 0x2 98:90:96:b8:af:8e * br0
192.168.9.211 0x1 0x2 00:0c:29:0f:8d:d8 * br0
192.168.9.253 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.31 0x1 0x2 00:34:da:8a:29:52 * br0
192.168.9.136 0x1 0x2 00:0c:29:e6:13:0a * br0
192.168.9.28 0x1 0x0 00:34:da:8a:29:52 * br0
192.168.9.247 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.244 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.235 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.232 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.10 0x1 0x2 fc:92:3b:f4:01:00 * br0
192.168.9.231 0x1 0x0 00:00:00:00:00:00 * br0
192.168.9.144 0x1 0x2 00:0c:29:2c:31:ec * br0
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Console.log
Save the collect log into debug-log.zip and upload to user
Good, No kernel panic found so far... [5284767.137466] device br0 left promiscuous mode
[5284767.142396] device brwan left promiscuous mode
ADDR AID CHAN TXRATE RXRATE RSSI IDLE TXSEQ RXSEQ CAPS ACAPS ERP STATE MAXRATE(DOT11) HTCAPS ASSOCTIME IEs MODE PSMODE
02:ba:d0:88:10:20 3 4 65M 0M 19 4320 0 65535 EPSs 0 f 0 PS 107:04:58 RSN WME IEEE80211_MODE_11NG_HT20 0
f0:99:bf:31:35:da 1 4 65M 63M 31 0 0 65535 EPSs 0 f 0 Q 04:07:32 RSN WME IEEE80211_MODE_11NG_HT20 1
b8:86:87:48:dc:a3 2 4 216M 10024M 51 0 0 65535 EPSs 0 f 0 WPSM 01:24:36 RSN WME IEEE80211_MODE_11NG_HT40 0
00:34:da:8a:29:52 4 4 86M 38M 21 0 0 65535 EPSs 0 f 0 AP 01:21:20 RSN WME IEEE80211_MODE_11NG_HT20 1
### Tx ###
comp_queued : 29126868
comp_delivered : 33193296
msdu_enqued : 80156729
wmm_drop : 0
local_enqued : 52029321
local_freed : 520293 [5323766.326491] device br0 entered promiscuous mode
21
hw_queued : 59881071
hw_reaped : 59881071
[5323766.336431] device brwan entered promiscuous mode
underrun : 24
tx_abort : 0
mpdus_requed : 8431677
excess retries : 643232
last rc : 3
sched self trig : 0
### Rx ###
status_rcvd : 13998154
r0_frags : 0
r1_frags : 123
r2_frags : 125
htt_msdus : 13016607
htt_mpdus : 13016585
loc_msdus : 961533
loc_mpdus : 961533
oversize_amsdu : 0
phy_errs : 0
phy_errs dropped : 77
mpdu_errs : 344919
txrx stats:
tx: -428156905933957414 msdus (0 B)
rx: 9131193878257431835 msdus, 0 bytes
ast_be_xmit : 51989216
ast_be_nobuf : 0
ast_tx_buf_count : 2500
ast_tx_packets : 80150304
ast_rx_packets : 13938312
ast_tx_mgmt : 52029321
ast_tx_nobuf : 0
ast_tx_xretries : 643232
ast_rx_num_data : 12678460
ast_rx_num_mgmt : 441787
ast_rx_num_ctl : 732
ast_tx_rssi : 4294967168
ast_rx_rssi_comb : 12
ast_rx_rssi_chain0 : 5 255 3 0
ast_rx_rssi_chain1 : 8 255 1 0
ast_rx_rssi_chain2 : 7 1 2 0
ast_rx_rssi_chain3 : 253 255 2 0
ast_rx_bytes : 2490355238
ast_tx_bytes : 273754668
tx_compaggr : 6235220
rx_aggr : 2897893
tx_retries : 8431677
tx_xretries : 1343
tx_bawadv : 57870211
tx_compunaggr : 467793
ast_rxorn : 0
ast_txurn : 24
ast_txto : 0
ast_mib : 0
ast_rx_badcrypt : 0
ast_rx_badmic : 0
target assert count : 0
noise floor : -106
Last MSDU unset cnt : 0
Rx MCS STATS:
mcs 0- mcs 4 STATS: 42243,550176,512062,1368603,633998,
mcs 5- mcs 9 STATS:200485,194982,123686,1195037,1425448,
Tx MCS STATS:
mcs 0- mcs 4 STATS: 42765, 92026,298929,900581,784908,
mcs 5- mcs 9 STATS:136957,180137,1180589,797656,1489979,
Save capture lan/wan packet in SDRAM tmp dir
Saving Data...
Done!
end action
[5323767.435165] wil6210 0003:01:00.0 wlan0: WMI size too large: 28 bytes, max is 0
[5323767.444081] wil6210 0003:01:00.0 wlan0: WMI size too large: 28 bytes, max is 0
[5323772.474574] wil6210 0003:01:00.0 wlan0: WMI size too large: 28 bytes, max is 0
[5323772.483551] wil6210 0003:01:00.0 wlan0: WMI size too large: 28 bytes, max is 0
[5323777.514066] wil6210 0003:01:00.0 wlan0: WMI size too large: 28 bytes, max is 0
[5323777.523032] wil6210 0003:01:00.0 wlan0: WMI size too large: 28 bytes, max is 0
[5323782.553419] wil6210 0003:01:00.0 wlan0: WMI size too large: 28 bytes, max is 0
[5323782.562357] wil6210 0003:01:00.0 wlan0: WMI size too large: 28 bytes, max is 0
[5323787.592679] wil6210 0003:01:00.0 wlan0: WMI size too large: 28 bytes, max is 0
[5323787.601598] wil6210 0003:01:00.0 wlan0: WMI size too large: 28 bytes, max is 0
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Hi Furrye38,
nothing changed.
only uptime is 61 day..:)
Thanks for help,
Ruslan.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Well, the same thing is happening on the LAN side. The remote peer is not responding correctly to the TCP 3 way handshake. This seems to rule out the router. Perhaps you can capture the packet exchange without the router, since you claim things work.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
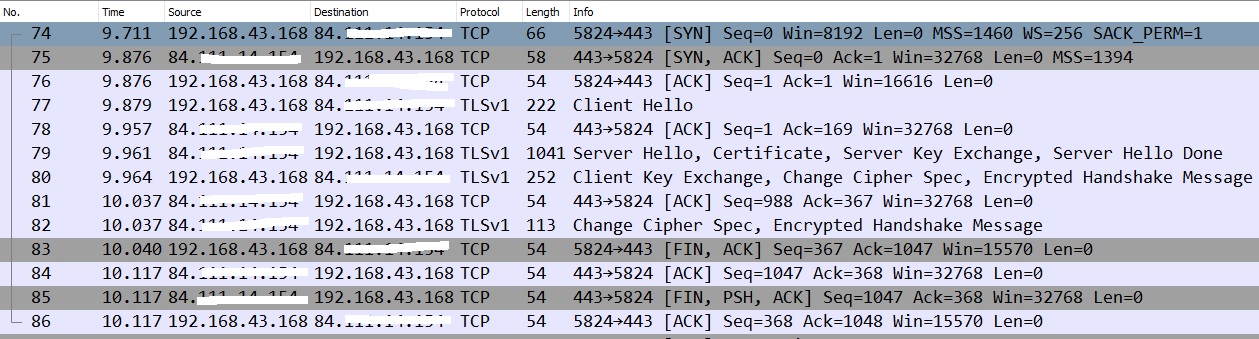
Re: R9000 block ssl-vpn connection ( port 443)
thanks for trying to help investigate this stange issue,
Sure, please see picture below:
if you need more info please update me,
if course if needed i can give all pcaps files or other info.
Just update me what need.
Thanks,
Ruslan.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Are you using a VPN service or VPN application? Might contact either Mfr of these service for additional help and info. Seems this maybe a VPN service/app issue possibly.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
The latest capture looks like a healthy connection establishment. There is one odd thing. The source address is 192.168.43.168. With the router removed, I would have expected the source address to be 31.x.x.x, as before. Where is this private address coming from?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Hi FURRYe38,
Yes i use VPN applicaton Cisco Anyconnect.
i manage the remote peer,
like i wrote without R9000 the connection worked ok.
i forgot to wrote also when i trying to browse to this vpn https://XX.XX.XX.XX netgear recognize this like DDOS and blocking the connection.
Thanks for trying to help,
Ruslan.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Hi TheEther,
i was using 4G connection from phone,
That why was address 192.168.43.168
if need i can do PPPoE directly and show you the results.
Ruslan.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Feel free to run it. If it looks the same as the last one, there's no need to post it. Do you have another router that you could test?
If you want to put the pcap files some place that I can access, I can take a look.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: R9000 block ssl-vpn connection ( port 443)
Hi TheEther,
yes it's look like the same one.
Yes i have the old Cisco 861W and i check with it and SSL VPN worked correctly.
when you will have time look at files and update me if you find something if not i will reboot the router probably all will work.
the link to dropox i send you privately.
Thanks,
Ruslan.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
Just to Update,
Reload the router and SSL VPN worked correctly.
May be was some issue with MTU like TheEther say...
Will continues to monitor if it will happen again will update.
Thanks for you all for trying to help.
Ruslan.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
• What is the difference between WiFi 6 and WiFi 7?
• Yes! WiFi 7 is backwards compatible with other Wifi devices? Learn more