- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Wireless user separation
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Wireless user separation
wireless 1 says this is the most secure and use for admin. How do i separate users on 2 or 3 and make them as secure as wireless 1 ?
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Wireless user separation
Orbi Pro AX model? Associate the Wireless 2 and 3 profiles with dedicated VLANs for example.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Wireless user separation
how is wifi 1 the safest and how do I make the other networks as safe? I read that vlan has leak vulnerabilities. Is the basic router setup a one lan a vlan in itself? Then setting up additional lan/ vlans further separates the users virtually but not physically. Will the networks 2 and 3 be safer with user separation?
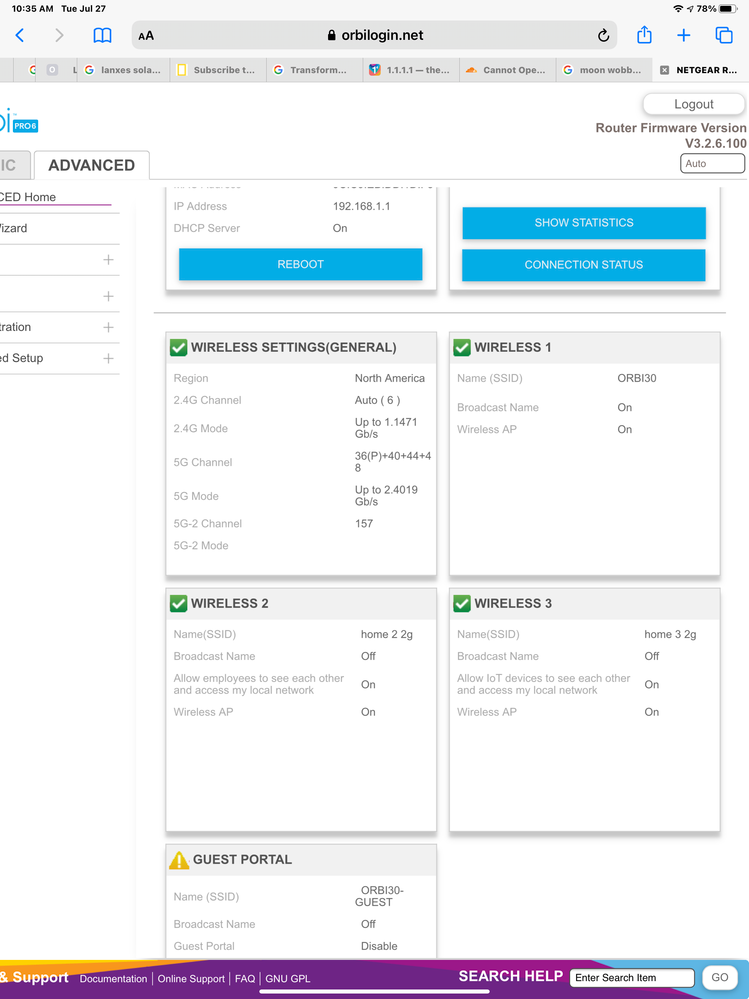
It is Orbi Pro AX6000 WiFi 6 Tri-Band WiFi System. Wireless 2 and 3 say :
| Allow IoT devices to see each other and access my local network | On |
wireless 1 says
| Name (SSID) | ORBI30 |
| Broadcast Name | On |
| Wireless AP | On |
if i use advanced setting lan setup to activate lan 2 and assign a VLAN group; then wireless setup and assign wireless network to a VLAN? How does the advanced vlan/bridge Ethernet port setting correspond with the lan and wireless vlan settings? Then will Users or devices not be able to see one another?
My lan Ethernet ports under vlan/bridge settings are setup as access points for the base and one satellite, and vlan is set as default.
when I assigned vlan in lan and wireless setup , separation did not show on advanced home summary screen.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Wireless user separation
Each VLAN does make a dedicated network. Of course, physically on the same network. Industry standard in the IT industry. Multi-tenant data centers operate VVLAN where each customer has his own full ability to use all VLANs possible. And everything can be on the same physical network. Nothing wrong with this.
The WiFi client separation is a different thing - it does just prohibit by some clever L2 MAC filtering that wireless clients can communicate direct. That's why you don't see this enabled. For most use case, this is not a feature you want on your wireless...
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Wireless user separation
So lan and vlan are a form of network separation or allocation. Network isolation can be on one or all of the lan by way of a designated vlan on that lan.
lan 1 without changes then contains all devices and its default shows no client separation in the vlan bridge settings as default1. And literature says wireless 1 is the most secure and resides on lan1 1 withe the default1 vlan.
would I want to assign any of the switches to a vlan with client isolation? Then any device connected to that switch would be governed by the assigned vlan setting? Also a wireless device?
The switch settings show a vlan menu, so the communication of wired devices or wireless devices connected to the switch will be affected by the vlan choice and it's setting and will ass
so if assigned to a vlan then network three, for example, would be on a separate lan with the assigned characteristics of the vlan I'd associated with that lan? Otherwise all wireless networks and wired devices would be on lan 1 and governed by its default or assigned vlan profile?
if a wireless network has the vlan activated then it will be assigned to the lan that has the chosen vlan id?
if i wanted to prevent a wired desktop, or a unauthorized wireless device from communicating with a device on wireless three, for example, or wireless three devices from communicating with one another then a isolation would be useful?
i I found these instructions for separation but only through insight app(I did not want to use insight because seems like remote administration and additional,vulnerability) but bot as simple in web interface.
To set up client isolation on your wireless access point using the Insight Cloud Portal:
- Log in to the Insight Cloud Portal.
- If you have an Insight Pro account, select a organization.
- Select a location.
- Select Wireless > Settings > WiFi and Captive Portal.
- On the far right of your SSID, click the pencil (Edit) icon.
- Select Settings.
- Click the Enable radio button.
- Click the Broadcast SSID radio button.
- Click the Client Isolation radio button.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Wireless user separation
Step back a little bit from this "most secure" wording a little bit and reflect this:
The idea of the product design and the implementation and the related specific naming of certain controls or status came from the idea to provide a trust model:
Wireless 1 (highest trust) >> Wireless 2 (BYOD, medium trust) >> Wireless 3 (IoT, low trust)
This does not mean that the Wireless 1 must have the most strict settings in place - you simply won't give systems access to that network where you don't have the highest trust and confidence.
Now let's talk about your question ref. the switches. Assume you think about lightly configurable Plus, smart managed Pro, or even managed switches. Most of these have the ability to configure a management VLAN. This is the VLAN you use for the switch management. No doubts, in an enterprise and expensive business environment, you would operate a dedicated management VLAN. This would make it impossible for the typical workplace computer, and even less for BYOD, guests, .... to reach the network management. This would map to an extended trust model like this:
Network Management (extreme trust) >> Wireless 1 (highest trust) >> Wireless 2 (BYOD, medium trust) >> Wireless 3 (IoT, low trust) >> Guests (zero trust, restricted Internet only)
All this does come however with a lot of practical impact. Users need to print. You as the network admin would like to discovery network devices and use management Web and Apps. Mobile devices need discovery and access of media players for playback or screen mirroring. Wireless light and climate/heating controllers need to talk to the related actors (there it goes the isolation for IoJ - you don't want to depend on Internet and cloud availability for these, do you?). And of course you would like to use the nice mobile Apps for light and climate/heating. The network admin needs Web and probably App access to the network devices, and also needs SNMP, TFTP, .... Any many more. Said all that: Of course this does not limit the switch primary intention for dealing with multiple VLANs, tunks or access ports.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: Wireless user separation
Yes, I see a detailed network. The access controls and default settings prevent access to wireless 1 and lan 1 admin capability and devices. The firewall is fixed also this Orbipro.
I would like to explore features but is difficult to see controls. Understandably conveniently configured for ease of deployment and employment.
My network is only 4-7 computer devices(1 wired), two wired Apple TV's one to the router the other to the satellite , a wired hue light hub.
The area is crowded multi family embedded in crowded commercial district with unsecure street. Much interference with obstructive buildings and electromagnetic and wireless.
my main concern is network device infiltration, exfiltration, lan device to device. So the firewall is default configuration , and partly configurable from cloud remote insight application.
tried the Insight app, did not explore it much because it seemed to dissable my web administrative login. Had to reset the router to get back web interface.
I read of cross vlan and device vulnerability so i deactivated all lan except lan 1. Probably should at least use the employeee or Iot for web access, employee says is tighter than iot. I activated wireless 2 assigned to lan 2 with employee vlan. Says this that isolates networks and devices, prevented login to lan 1 wireless 1. Still shows allow iot devices to communicate with one another and connect to internet. Not sure if that means all networks, router switches and satellite switches. I don't think i want to complicate any further by changing the vlan assignments of the router or satellite.
I want to protect one wireless client on 2 or 3 from the wan, wired desktop, other wireless users on same network, from wired and wireless vulnerabilities from the same network, hosted networks, and wired devices on the router and satellite.
would i have to use the Insight app to further isolate wireless 2 from other wireless clients or users on wireless 2 , and explore firewall features?
i assigned wireless 2 to lan 2 and the employee vlan configuration. Then lan 1 is secure ? And explains why i could not login to the wireless 1 from wireless 2. I could still stream to wired Apple TV with default 1 vlan.
Thank you for your advice.
If have a thr