- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Re: GS324T Port Separation
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have a SG324T that we plan to use as an edge switch. Internet traffic hits it, and then our firewalls plug into it.
I would like to designate ports 1-10 to be isolated and only be able to communicate with each other.
I would like to designate ports 11-20 to be isolated and only be able to communicate with each other.
I will not be able to change the VLAN's that our outside devices operate on; they're all on VLAN 1, and that cannot change.
How can I configure the switch to do this?
Additionally, I would like to be able to keep these two port groups away from the switch's web admin. I've tried setting Admin Mode to Disable on ports 1-20, but all this seems to do is completely disable / turn-off those ports.
Any help would be appreciated!
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
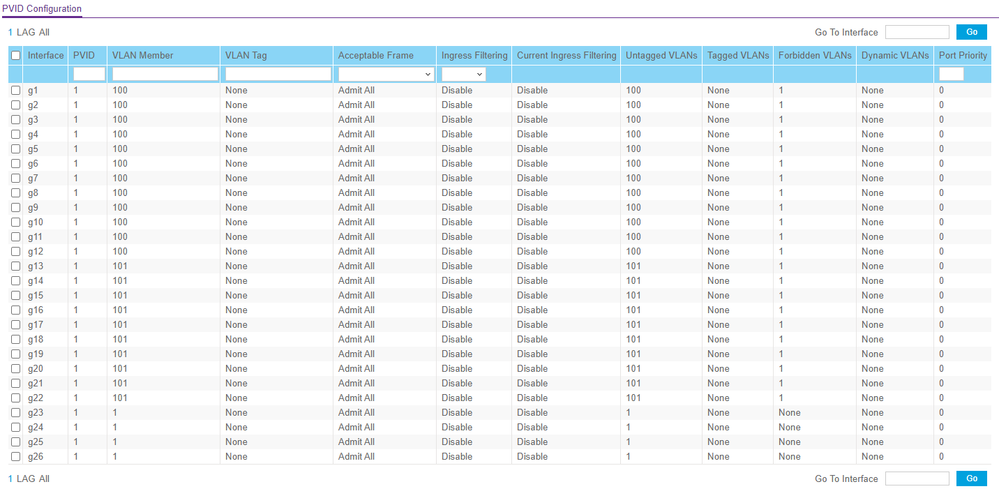
For port 1..12 (VLAN 100 untagged) the PVID must be configured to 100, for port 13...22 (VLAN 101 untagged) the PVID must be configured to 101. Reason: The PVID does define the VLAN where incoming untagged frames are assigned to. That's why you have no communication on the ports you have tested.
All Replies
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: GS324T Port Separation
Hello David,
One possible approach (read more or less the industry standard) is to configure three 802.1q VLANs, make each port group [U]ntaged and PVID to the VLAN intended, change the switch management VLAN to the VLAN intended for management, and last but not least remove the ports from the VLAN 1 membership.
@davidcrowder wrote:
I will not be able to change the VLAN's that our outside devices operate on; they're all on VLAN 1, and that cannot change.
While this isn't a problem as you have many other VLAN IDs available on these switches: Is the VLAN 1 used tagged at all on the Internet side of things?
@davidcrowder wrote:
Additionally, I would like to be able to keep these two port groups away from the switch's web admin. I've tried setting Admin Mode to Disable on ports 1-20, but all this seems to do is completely disable / turn-off those ports.
That's exactly what the Port Admin Mode Disable is for - it does indeed disable the port. The way to do this is to define the switch management VLAN to an existing VLAN where you intend to run the network administration from. This does limit the network management to this specific VLAN only. Good advise (as very useful) is to have a DHCP server on the management VLAN, too.
Regrds,
-Kurt
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: GS324T Port Separation
Kurt,
I believe I have tried as you suggest. However, I'm not having any lucking making that work; if I plug a device into port 1 and another into port 2, they do not communicate.
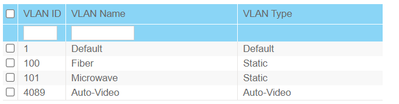
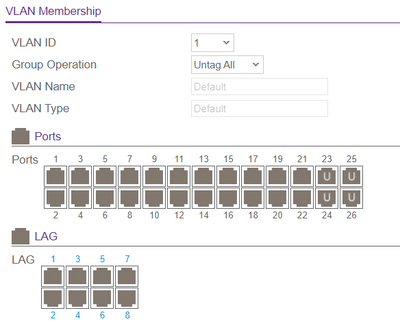
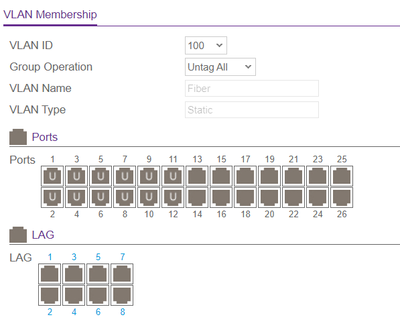
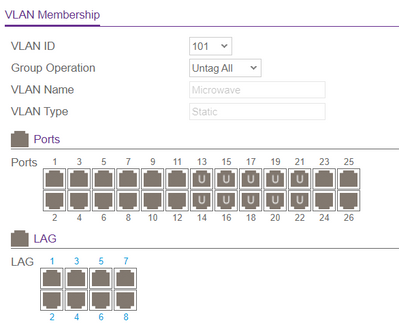
Below are screenshots of the relevant settings. Can you point out where I have gone awry?
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For port 1..12 (VLAN 100 untagged) the PVID must be configured to 100, for port 13...22 (VLAN 101 untagged) the PVID must be configured to 101. Reason: The PVID does define the VLAN where incoming untagged frames are assigned to. That's why you have no communication on the ports you have tested.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content