- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
The handling of untagged packets across a physical network
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I should be getting two GS308T units tomorrow.
Glancing at this forum and the owners manual, I feeling mystified about the handling of untagged packets, and the notion of packets "defaulting to VLAN1". In my case, I want to retain the flow of untagged packets across the physical network, in addition to adding two VLANs across the same physical network.
I have a Sonicwall TZ300, and easily configured three unique firewalled-zones/subnets, and binded them all to a single RJ-45 port with tagging/untagging as follows:
- Guest Subnet 192.168.0.0/24 - untagged packets
- Home Subnet 192.168.1.0/24 - V500 tagged packets
- Special Subnet 192.168.2.0/24 - V700 tagged packets
I also have a Ubuiquiti UAP-LR WAP, and easily configured it's single RJ-45 port with untagging/tagging as follows:
- untagged packets -> Guest SSID
- V500 tagged packets -> Home SSID
- V700 tagged packets -> Special SSID
I assume the TZ300 <-> Uniquiti CAT6 is properly called a "trunk", and that a proper trunk can have both tagged AND UNTAGGED packets?
With the GS308T tied into a second port off the SonicWall, WILL I BE ABLE TO HAVE:
- untagged packets -> GS308T RJ-45 ports 2-3
- V500 tagged packets -> GS308T RJ-45 ports 4-5
- V700 tagged packets -> GS308T RJ-45 ports 6-7
- the SonicWall will connect into GS308T port 1
The devices connected to GS308T ports 2-7 would be untagged, as the end devices are VLAN ignorant.
I'm mostly looking for early feedback of "yep it can be done", "might I suggest another approach" or "nope/LOL". I think my concern is the untagged packet handling.
For bonus points, if VLAN assingments are done by MAC addresses (instead of ports), and a GS308T port is tied to an ordinary unmanaged 8-port switch with 7 devices hanging off it, will the GS308T be ok with seeing 7 MACs on one port, and potentially having those MACs assigned to differing VLANs? (each MAC would only belong to one VLAN).
Thanks,
Thomas Gilg
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats the ah-haa I wanted to happen!
On a switch, and by design you have one or multiple VLAN on a physical network.
On the links, e.g. a Ethernet link, a LAG, ... a VLAN can be tagged (one or many), or untaged. A port where you want to connect a system for VLAN 123, is only an untagged member of VLAN 123, the PVID 123 does make untagged frames to enter the VLAN 123. The traffic in a VLAN is not VLAN "tagged" - while this is not fully correct,also QoS information can be part of a tag. How the frames are coming out of a port, with or without VLAN tags, is defined at the switch boundary. Where untagged frames are assigned to does also happen as defined by the PVID at the switch boundary.
Similar for the wireless access point - there the VLAN is always* untagged on the SSID. (*Again, highly sophisticated designs allow one SSID and multiple VLANs, depending on the 802.1x authentication the VLAN membership can be assigned).
All Replies
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: The handling of untagged packets across a physical network
Hallo Thomas,
Sure you can - both solutions are workable and can be implemented.
Don't be confused about terms like trunk or access port. sure a trunk port can carry untagged and tagged frames, while an access port just carries untagged frames for a single VLAN. The trunk term is also used in the context of LAG/bonding/port trunking where multiple physical ports of the same speed and latency are combined into a trunk.
By default, the ports on these switches are configured to the VLAN 1
VLAN 1 [U]ntagged ... what makes the switch remove the tag from the frame when leaving the switch , and
PVID 1 ... what makes incoming VLAN untagged frames to be associated to the VLAN 1.
When creating a port connecting to the VLAN 500 resp. VLAN 700, ensure the PVID is also set to 500 resp. 700, and the port is removed from the default VLAN 1 by an [ ]empty entry.
Regards,
-Kurt
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: The handling of untagged packets across a physical network
Thanks Kurt! Very helpful.
Per your reply, an ah-ha seems to be... the "1" in "VLAN 1" does not imply packets vtagged with a 1. It seems the descriptor (token) "VLAN 1" could have been named "VLAN UNTAGGED" so as not to imply a vtag of 1.
Edit/hum - do untagged packets OUTSIDE the switch get tagged with 1 for internal handling purposes within the switch? Outwardly I have untagged packets, but for brief periods within the switch they get mapped/unmapped from said "VLAN 1".
My units should arrive today, and it will be fun to get hands on and pound it out.
Thomas Gilg
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thats the ah-haa I wanted to happen!
On a switch, and by design you have one or multiple VLAN on a physical network.
On the links, e.g. a Ethernet link, a LAG, ... a VLAN can be tagged (one or many), or untaged. A port where you want to connect a system for VLAN 123, is only an untagged member of VLAN 123, the PVID 123 does make untagged frames to enter the VLAN 123. The traffic in a VLAN is not VLAN "tagged" - while this is not fully correct,also QoS information can be part of a tag. How the frames are coming out of a port, with or without VLAN tags, is defined at the switch boundary. Where untagged frames are assigned to does also happen as defined by the PVID at the switch boundary.
Similar for the wireless access point - there the VLAN is always* untagged on the SSID. (*Again, highly sophisticated designs allow one SSID and multiple VLANs, depending on the 802.1x authentication the VLAN membership can be assigned).
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: The handling of untagged packets across a physical network
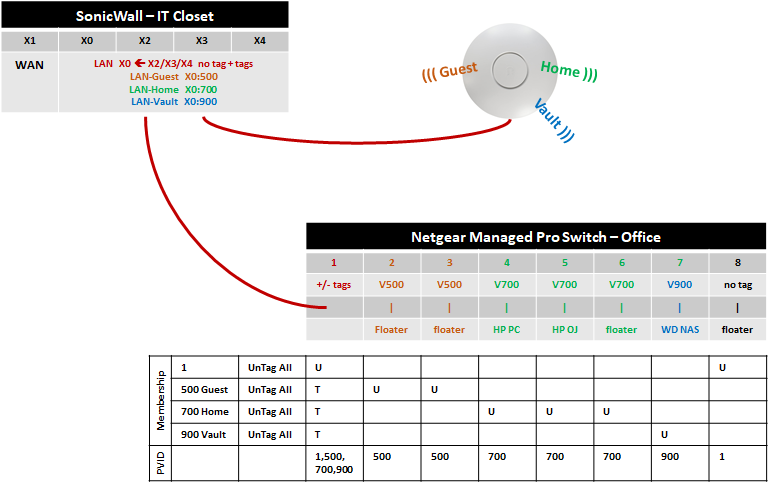
Everything seems to be working fine. Attached is a visual of the winning settings.
The only real question is... I have untagged and tagged traffic coming into g1 from the SonicWall, and presumably only the untagged traffic from the SonicWall is popping out on g8.
Thanks again.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: The handling of untagged packets across a physical network
@siletzspey wrote:I have untagged and tagged traffic coming into g1 from the SonicWall, and presumably only the untagged traffic from the SonicWall is popping out on g8.
Sure, this is how it has to be - the g8 port is a connection into the VLAN 1. The VLAN 1 is logically yet another VLAN which is accessible to untagged frames on g1 and g8. Again: The VLAN tagging on the links does exist just to mark the frame is a member of another network, different from the untagged frames. Tagging does not "make" the VLAN.
To avoid confusion: The PVID information on the table shown for switch g1 is wrong - only one PVID can be set, and this must be PVID 1 in this config.
Last but not least, the old rule not to use the VLAN 1 (coming from crappy design from certain vendors having a default primary VLAN "0" spanning all ports and without any control) does not apply here, unless people forget to unmark the ports from VLAN 1. further on, if adding more switches daisy chained to this one, ensure the VLAN 1 untagged is part of the trunks - features like STP/RSTP (valid for the complete physical network, all VLANs) do always run on the untagged network.