- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
GS180PEv3 management VLAN reachable via guest VLAN
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I originally posted this on the Ubiquiti forums, but have determined that my Netgear GS108PEv3 appears to be the issue. Details of my network and problem are below:
I have setup a Ubiquiti Edge Router Lite, and almost everything is working as planned--except my guest vlan has the ability to ping a single address on the management vlan. Specifically, when I log onto the guest wifi, I get a 10.0.20.X ip on vlan 20, which I want. I am not able to ping 10.0.20.1, 10.0.10.1, 10.0.10.3, 10.0.10.4, which I also want...but I AM able to ping the Netgear GS108PEv3 switch at 10.0.10.2, which I don't want.
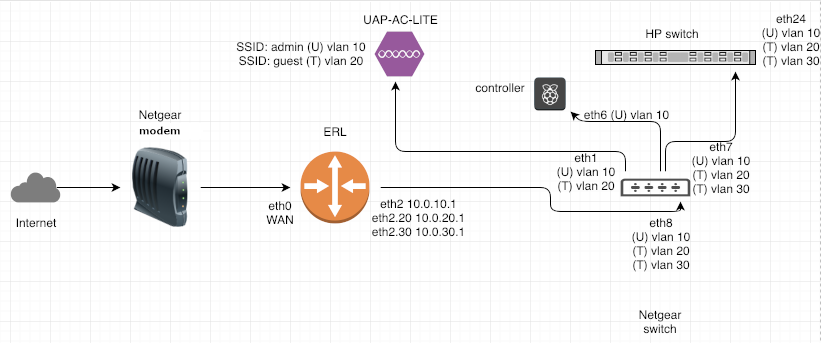
My setup is as followed:
AP
I have two SSID:
Admin Untagged on VLAN 10
Guest Tagged on VLAN 20
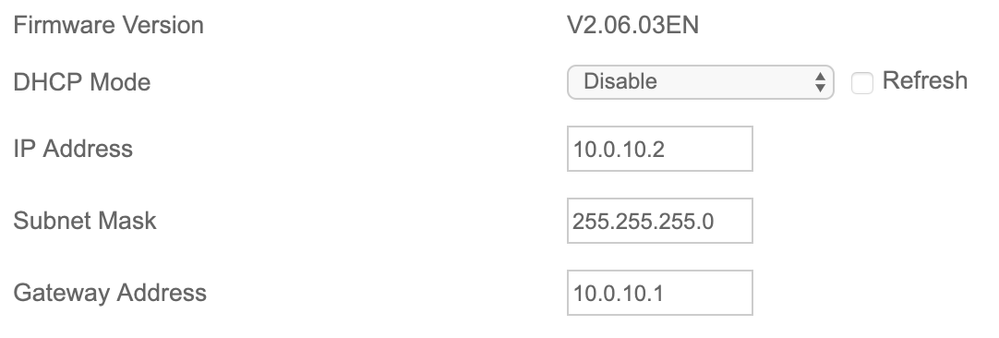
Netgear switch ip 10.0.10.2
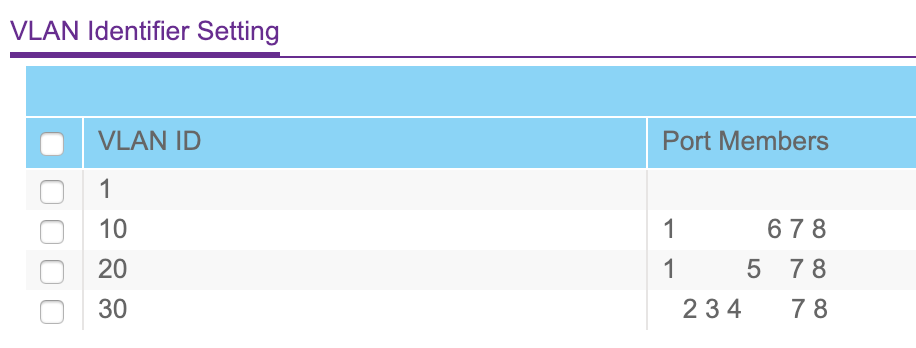
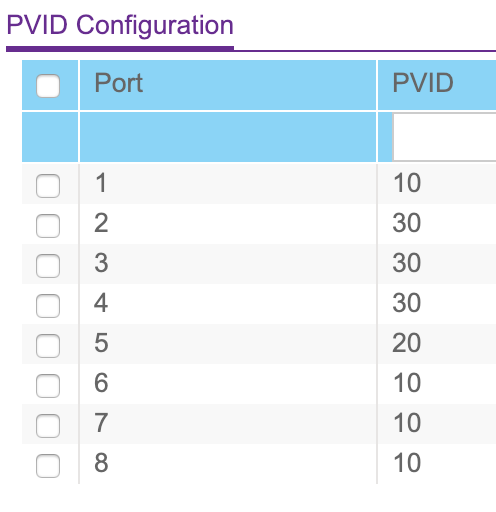
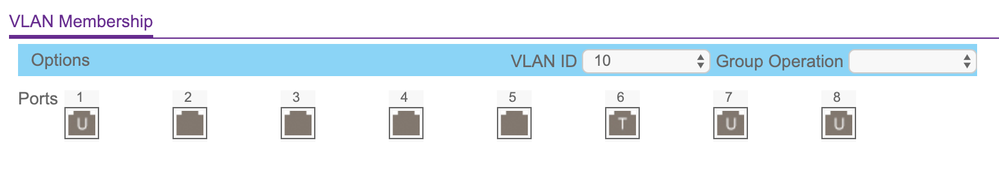
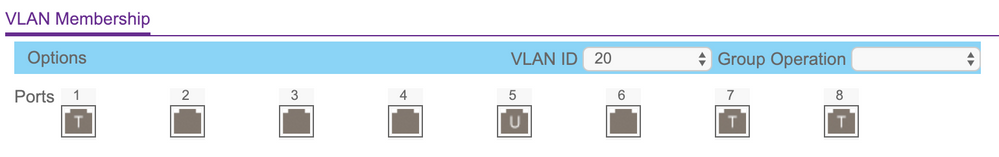
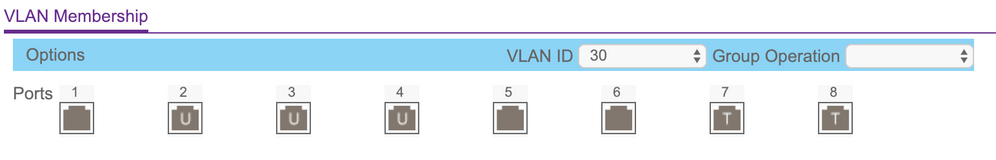
Port 1: Untagged VLAN 10, Tagged VLAN 20 (to AP ip via DHCP)
Port 6: Untagged VLAN 10 (to controller at 10.0.10.4)
Port 7: Untagged VLAN 10, Tagged VLAN 20, Tagged VLAN 30 (to HP switch at 10.0.10.3)
Port 8: Untagged VLAN 10, Tagged VLAN 20, Tagged VLAN 30 (to ERL router at 10.0.10.1)
HP switch ip 10.0.10.3
Port 24: Untagged VLAN 10, Tagged VLAN 20, Tagged VLAN 30
ERL Router
eth0: WAN
eth2: 10.0.10.1 Untagged VLAN 10
eth2.20: 10.0.20.1 Tagged VLAN 20
eth2.30: 10.0.30.1 Tagged VLAN 30
Some additional photos of my settings in the Netgear switch:
My firewall rules:
firewall {
all-ping enable
broadcast-ping disable
group {
network-group RFC1918_RANGES {
description "All possible private addresses"
network 192.168.0.0/16
network 172.16.0.0/12
network 10.0.0.0/8
}
}
ipv6-receive-redirects disable
ipv6-src-route disable
ip-src-route disable
log-martians enable
name CAMS_IN {
default-action drop
description "CAMS to eth2.10"
rule 10 {
action accept
description "Allow VLAN 10 connection"
destination {
address 10.0.10.0/24
}
protocol all
source {
}
state {
established enable
related enable
}
}
}
name CAMS_LOCAL {
default-action drop
description "Drop CAMS to router"
}
name GUEST_IN {
default-action accept
description "GUEST to WAN"
rule 10 {
action drop
description "Drop GUEST to any private address on other interface"
destination {
group {
network-group RFC1918_RANGES
}
}
protocol all
}
}
name GUEST_LOCAL {
default-action drop
description "Drop GUEST to router"
}
name WAN_IN {
default-action drop
description "WAN to LAN for established/related"
rule 10 {
action accept
description "Allow established/related packets"
state {
established enable
related enable
}
}
rule 20 {
action drop
description "Drop invalid packets"
state {
invalid enable
}
}
}
name WAN_LOCAL {
default-action drop
description "WAN to router for established/related"
rule 10 {
action accept
description "Allow established/related packets"
state {
established enable
related enable
}
}
rule 20 {
action drop
description "Drop invalid packets"
state {
invalid enable
}
}
}
receive-redirects disable
send-redirects enable
source-validation disable
syn-cookies enable
}
Here is the link to the UBNT forum with lots of TCPDumps as well:
Netgear switch responding to pings from guest VLAN
TLDR;
My Netgear GS108PEv3 appears to respond to pings and is reachable via browser from guest vlan when my firewall rules and router config appear to be correct. Maybe I am missing (or messed up) a setting on the GS108PEv3 switch? I've removed the switch and replaced it with a cheap Zyxel managed switch and I am NOT able to reach the management VLAN from the guest VLAN, which is what I want. I upgraded the firmeware, factory reset the Netgear router, and reconfigured it, only to be able to hit the Netgear switch from guest VLAN--which is what I do NOT want. How can I ensure this switch is NOT reachable via a guest VLAN? Did I possibly misconfigure this switch?
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, this is a limitation of the platforms used for most Smart Managed Plus switches (GSxxxE) - the CPU port can't be restricted to a certain VLAN only. Bet you have no such control for a management VLAN on the UI (only few Smart Managed Plus have, like the XS724EM). And just based on the IP address the switch won't "magically" add a VLAN config or ACL - the management IP is active on all VLANs on these models aimed to be very lightly managed, that's all.
Wonder why you posed on the other vendor forum - it's clearly a (well known, many times) discussed and explained limitations of these very simple managed switch family.
All Replies
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, this is a limitation of the platforms used for most Smart Managed Plus switches (GSxxxE) - the CPU port can't be restricted to a certain VLAN only. Bet you have no such control for a management VLAN on the UI (only few Smart Managed Plus have, like the XS724EM). And just based on the IP address the switch won't "magically" add a VLAN config or ACL - the management IP is active on all VLANs on these models aimed to be very lightly managed, that's all.
Wonder why you posed on the other vendor forum - it's clearly a (well known, many times) discussed and explained limitations of these very simple managed switch family.
- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Re: GS108PEv3 management VLAN reachable via guest VLAN
Thank you so much for the help. This was actually the first time I setup my router from scratch, so I posted on the Ubiquiti forum initially thinking my firewall rules were the problem. This was also the first time I've setup VLANs, so I wasn't sure where to look for help. Once I realized my switch was the issue, I came here. Thanks again. BTW, do you have a recommended switch for my needs? A POE switch with 8-16 ports, preferably rack mountable?