- Mark as New
- Bookmark
- Subscribe
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
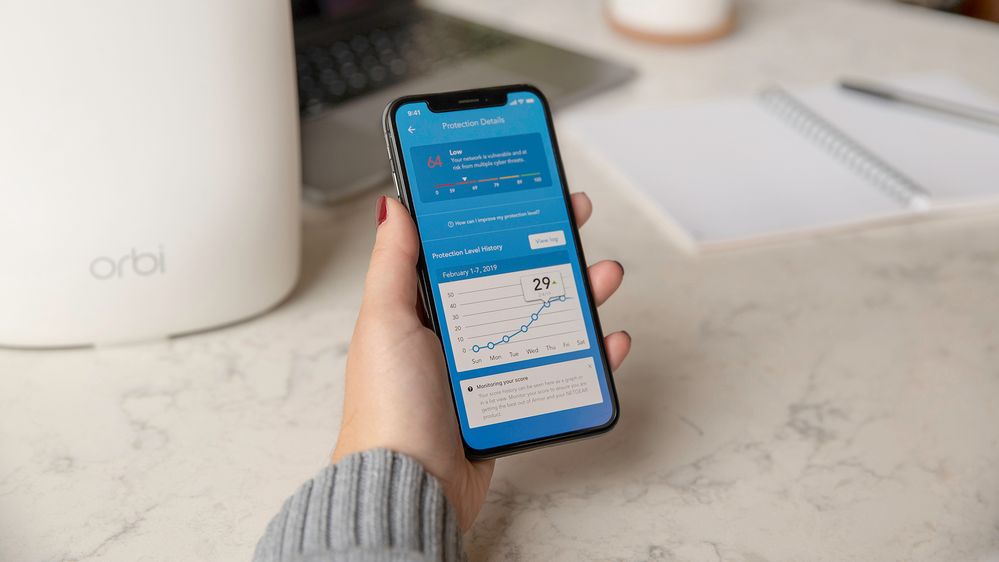
What is the NETGEAR Armor Protection Score?
The NETGEAR Armor Protection Score ranks the security of your home network and its connected devices. This ranking is shown as a protection level score and ranges from 0 (critical) to 99 (excellent). Security tips and suggestions are displayed depending on your protection level score to help NETGEAR Armor users ensure they participate in maintaining the highest level of security.
How is the NETGEAR Armor Protection Score Calculated?
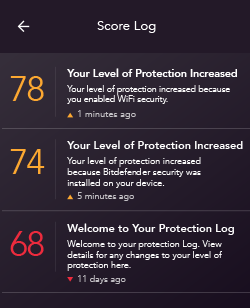
Scores are calculated using many different pieces of information. The majority of the score takes into consideration the following:
Is NETGEAR Armor currently on? If your NETGEAR Armor service is on you don’t have to worry. This ensures that the router will block the traffic to Phishing links and scan your Smart Home devices.
Is your router on the latest firmware? NETGEAR releases new firmware regularly for its routers. Having the latest firmware not only fixes some known security issues but may also enhance your router’s performance. Updating the firmware to the latest available version boosts your protection score!
Is Bitdefender Security installed on all personal devices? This is important since NETGEAR Armor provides multi-layered cybersecurity on your smartphones, computers, smart TVs, security cameras, and anything else connected in your home.
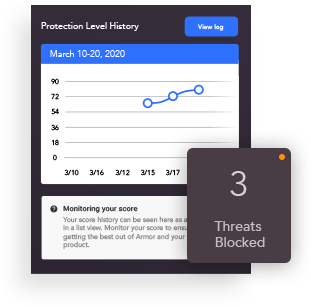
How vulnerable is your network to threats and vulnerabilities? Good network security begins with good habits. If you have a lot of insecure activity in your home network such as clicking on links that are considered targeted phishing attacks or spam attacks, then your score is lowered. The best way to boost your score is to clean up any infected devices or make sure you take action to remove the source of threats.
Additional elements of the NETGEAR Armor Protection score include:
- How well are your network and devices password-protected, particularly IoT devices like cameras, thermostats, refrigerators, etc? Default passwords should always be changed for more security.
- Does your network have Guest WiFi enabled so that visitors do not have access to your main or primary network? Doing so helps keep your files, data, and personal information safe, improving network security.
- Is remote management allowed from your app so that you can address notifications or recommendations when away from your network?
- Are Parental Controls on? Parental Controls further help protect your network by managing sites that your child can visit while limiting their exposure to malicious content and software threats.
- Is your app push notifications on to allow alerts of vulnerabilities or threats that might need immediate attention?
- Is 2-step verification in place?
What are some common threats and vulnerabilities I can be exposed to?
Phishing
Phishing is a cybercrime in which a target is contacted by email, phone or text message by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking & credit card details and passwords.
Malware
Short for "malicious software", this is the general term covering threats to your computer safety such as viruses, spyware, worms, trojans, rootkits.
Spam
One of the defining characteristics of spam is that it’s sent out in bulk, often to thousands or even millions of recipients all at once. Most spam is not particularly well-targeted. Instead of taking the time to figure out who might be interested in a particular product, spammers find it easier and cheaper to pitch their products to every email address they can get their hands on.
Ransomware
Ransomware is a type of malicious software designed to block access to a computer system or computer files until a sum of money is paid. Most ransomware variants encrypt the files on the affected computer, making them inaccessible, and demand a ransom payment to restore access.
Trojan
Strictly speaking, a Trojan is not a virus, although it is often thought of as such. Really, they are programs that enter computers appearing to be harmless programs, install themselves, and carry out actions that affect user confidentiality.
Virus
Viruses are programs that can enter computers or IT systems in a number of ways, causing effects that range from simply annoying to highly-destructive and irreparable.
Password Stealer
A program that obtains and saves confidential data, such as user passwords (using keyloggers or other means). This program can publish the list, allowing third-parties to use the data to the detriment of the affected user.
Fraud
Fraudulent pages use deceptive techniques with the intent of obtaining unlawful gain. For example, a fake online shop can trick the victim into sending money in advance without delivering the order.
Exploit/Infected/Untrusted
Untrusted pages exhibit suspicious behavior or particularities we deem risky, therefore you should avoid accessing them to keep your data unharmed.
Miner
This type of page is related to cryptocurrency mining and may attempt to use your device's resources for this purpose, thus impacting its performance and life span.
PUA
This type of page contains or may serve PUA (Potentially Unwanted Apps). These apps exhibit behaviors that impact the privacy and security of the device they get installed on.
Do you know your NETGEAR Armor Protection Score? How often do you check to see how well your network is protected? Tell us in the comments below!