NETGEAR is aware of a growing number of phone and online scams. To learn how to stay safe click here.
Forum Discussion
AndrewJohn
Mar 01, 2017Aspirant
Edge Browser Certificate Error
We've moved to using Microsoft EDGE browser as standard (tired of using 3 browsers one for each "thing" it does best. Trying to muscle through this transition. This should be an "easy find" in the ...

- Mar 02, 2017
AndrewJohn wrote:
Seriously, this is something that should not happen in world-class software and commercial hardware. Don't you agree?
I wish that were the case.
One challenge with internet security is authentication. You want to know that the server you are connecting to is really the server it claims to be. You don't want to go to a fake banking site, and enter your password credentials for instance.
Certificates are part of the solution to that problem. A CA-signed certficate accomplishes two things - it enables encrypted connections to the server, and it tells the client that the CA believes the server is what claims to be. That second half is the authentication piece. The client needs to trust the CA, it has no way to verify that claim on its own.
The problem with CA-signed certs is that getting them is pretty complicated. You need to get a domain, set up a server to use it. Then you need to contact a CA, and convince them that you are who you say you are. They give you a signed certificate, and you need to install it on your server yourself.
This is way too hard for consumers, and it's often a challenge for IT folks too. So there's a simpler variation on the cert - which is self-signed. The self-signed cert can be created by anybody. It enables encryption, but it can't authenticate you - since you generate it yourself. That's what the NAS uses. The reason is pretty simple - Netgear doesn't know if you are who claim to be, and it would be foolish for them to give you their own certificate. If they did, you'd be able to claim you were Netgear - and you aren't.
To overcome the authentication warnings with a self-signed cert, you need to install it in the trusted root certification store of the OS. When you do that, you are telling the computer that you know where this cert comes from, and that you trust it. So you need to find a way to do that on your machines. Or you need to get a signed cert that you'd install on the NAS.
Installing the self-signed certs into the root store used to be much easier. But with the rise of cybercrime, there are a lot of fake sites that abuse the self-signed certs. So the browser folks were forced to put in much stronger warnings, and they intentionally made this process more difficult. It's a bit like the changes in airport security - actions by bad actors had consequences that inconvenience everyone.
In the specific case of Edge - it is a newcomer to the browser world and some of the cert management features that other browsers had weren't implemented (at least not yet). So it's actually missing some features related to this.
There are some new solutions to all this emerging. One is https://letsencrypt.org/ which uses newly standardized tools to automated certificate installation, and which offers free signed certificates from a certificate authority. It'd be great if the ReadyNAS installation included getting and installing one of these free certs. That's in the idea exchange, but so far Netgear hasn't touched it.
In any event, I haven't actually tried to install a self-signed cert on Windows 10. So you probably do need to find an on-line guide to help. I believe Chrome does let you export the cert, and there are tools (msc I think) that will let you install it to the trusted root store.
AndrewJohn
Mar 02, 2017Aspirant
Thank you StephenB for replying.
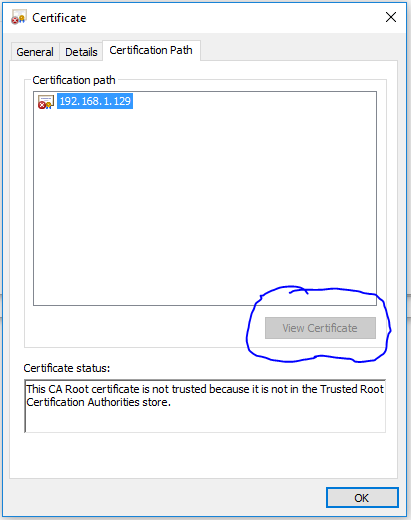
I tried this before - and that is a great link for installing certificates..., but it fails for ReadyNAS devices at this point because, the certification path root has no certificate to "View" so the "View Certificate" buton is grayed out, which, in the tutorial, is the place where you find and install that certificate for that site/device. But wait, who's IP address is that?
(See screen capture below.)
Of course, reading the "Certificate Status" message: "Theis CA Root certificate is not trusted because it is not in the Trusted Root Certification Authorities store." seems to imply that something is missing - either by accident (my user error?) or missing by design (Netgear engineers not thinking that this was important, and ultimately a PITA for administrators and users with the unintended, but obvious, consequences of inefficiency, confusion and concern by everyone having to "click through the warning."
Seriously, this is something that should not happen in world-class software and commercial hardware. Don't you agree?
Has no one found a solution? And, I have to say..., I'm beginning to really like EDGE over Chrome and FireFox. Cleaner, faster, and no "junk" consuming memory (Chrome). I know, my opinion is not universal - but I'm on EDGE for now, like it or not.
StephenB
Mar 02, 2017Guru
AndrewJohn wrote:
Seriously, this is something that should not happen in world-class software and commercial hardware. Don't you agree?
I wish that were the case.
One challenge with internet security is authentication. You want to know that the server you are connecting to is really the server it claims to be. You don't want to go to a fake banking site, and enter your password credentials for instance.
Certificates are part of the solution to that problem. A CA-signed certficate accomplishes two things - it enables encrypted connections to the server, and it tells the client that the CA believes the server is what claims to be. That second half is the authentication piece. The client needs to trust the CA, it has no way to verify that claim on its own.
The problem with CA-signed certs is that getting them is pretty complicated. You need to get a domain, set up a server to use it. Then you need to contact a CA, and convince them that you are who you say you are. They give you a signed certificate, and you need to install it on your server yourself.
This is way too hard for consumers, and it's often a challenge for IT folks too. So there's a simpler variation on the cert - which is self-signed. The self-signed cert can be created by anybody. It enables encryption, but it can't authenticate you - since you generate it yourself. That's what the NAS uses. The reason is pretty simple - Netgear doesn't know if you are who claim to be, and it would be foolish for them to give you their own certificate. If they did, you'd be able to claim you were Netgear - and you aren't.
To overcome the authentication warnings with a self-signed cert, you need to install it in the trusted root certification store of the OS. When you do that, you are telling the computer that you know where this cert comes from, and that you trust it. So you need to find a way to do that on your machines. Or you need to get a signed cert that you'd install on the NAS.
Installing the self-signed certs into the root store used to be much easier. But with the rise of cybercrime, there are a lot of fake sites that abuse the self-signed certs. So the browser folks were forced to put in much stronger warnings, and they intentionally made this process more difficult. It's a bit like the changes in airport security - actions by bad actors had consequences that inconvenience everyone.
In the specific case of Edge - it is a newcomer to the browser world and some of the cert management features that other browsers had weren't implemented (at least not yet). So it's actually missing some features related to this.
There are some new solutions to all this emerging. One is https://letsencrypt.org/ which uses newly standardized tools to automated certificate installation, and which offers free signed certificates from a certificate authority. It'd be great if the ReadyNAS installation included getting and installing one of these free certs. That's in the idea exchange, but so far Netgear hasn't touched it.
In any event, I haven't actually tried to install a self-signed cert on Windows 10. So you probably do need to find an on-line guide to help. I believe Chrome does let you export the cert, and there are tools (msc I think) that will let you install it to the trusted root store.
- AndrewJohnMar 02, 2017Aspirant
Thank you StephenB for that great review.
I'll still be holding on for a "world-class" solution - as this must get easier. It's a barrier (not unlike password proliferation.)
Maybe when retina scanning is ubiquitous..., (not holding my breath).
Thank you,
AJ
Related Content
NETGEAR Academy

Boost your skills with the Netgear Academy - Get trained, certified and stay ahead with the latest Netgear technology!
Join Us!