NETGEAR is aware of a growing number of phone and online scams. To learn how to stay safe click here.
Forum Discussion
spaceobh
Sep 27, 2015Aspirant
How to configure FVS318N to transmit NAT'ed LAN IP in FTP tranfers in stead of Firewalls WAN-IP.
I'm having this problem. Remote site is connected to the internet in a fixet, multiple IP-adress MPLS setup. The LAN side is presently protected by a Zyxel Zywall, but for a variety of reasons I...
- Oct 14, 2015
Hi Samir
Apologies for my delayed response.
I'll try to test the setup you are suggesting the next time I'm at the location, but since it's in east Greenland there are no planned trips - I only go there when absolutely necessary.
I will need to close my post here for now, and I'd like to thank all of you for your help.
When I initially opened the case I thought I had just missed to set a checkmark somewhere, and that I could sort of just "copy-paste" the rules etc. from the Zyxel to the netgear.
Cheers
SamirD
Oct 08, 2015Prodigy
If there's no server on the netgear lan, there's no need for any rules for ftp to work (unless you have a double nat, but it doesn't sound like you do). I think the incoming rule may actually be the issue. Could you try removing it and see what happens? In fact, just connect the netgear behind the zyxel--even though it's a double nat scenario, if you're using passive mode it shouldn't be an issue.
spaceobh
Oct 09, 2015Aspirant
"If there's no server on the netgear lan, there's no need for any rules for ftp to work (unless you have a double nat, but it doesn't sound like you do)."
That's what I was thinking - no outgoing rules needed. (yes, no double NAT)
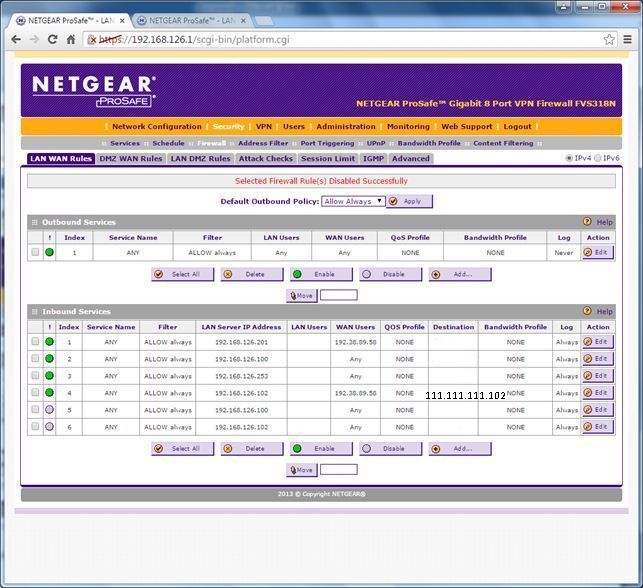
I need incoming rules to filter unwanted traffic, right?
My initial configuration was any-any for outgoing, plus the desired incoming rules in order to filter unwanted traffic and setup NAT.
"I think the incoming rule may actually be the issue. Could you try removing it and see what happens?"
No, can't do that - the unit is at the remote (very remote) location, and I don't want to risk intrusion, in a situation where I'm not present at the site.
"In fact, just connect the netgear behind the zyxel--even though it's a double nat scenario, if you're using passive mode it shouldn't be an issue."
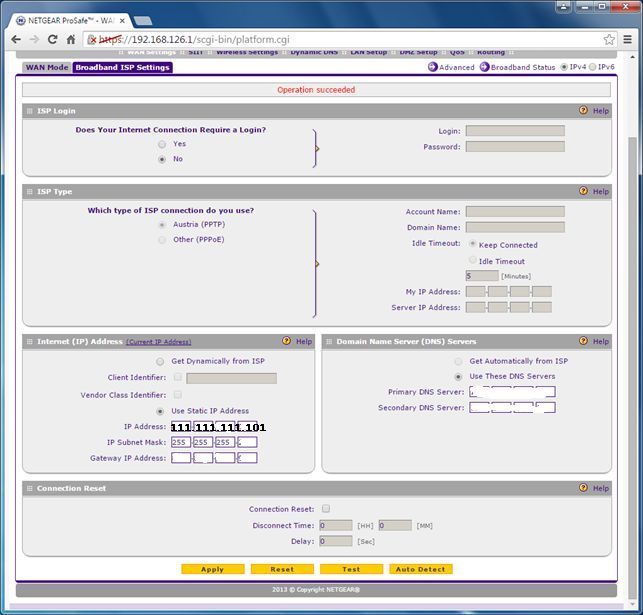
Can't do that either, the netgear is configured with a fixed WAN-IP (same as the Zyxel, obviously) so I don't see that can be done?
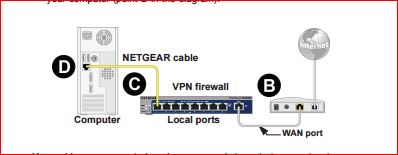
This is the setup:
Rules
WAN-IP
- SamirDOct 09, 2015Prodigy
Thank you for the diagrams as it makes it very clear. I wish others could do that in their threads!
So normally (and probably your current setup), the zyxel is in place of the netgear in the diagram showing the computer on the lan, correct? If so, you can plug a [i]default configuration[/i] 318n wan port into the lan port of the zyxel and then the computer on the lan into the lan port on the 318n. By default, the 318n will allow traffic to pass to the zyxel which will in turn pass it on to the Internet. This should work without an issue.
All those rules and services may be the issue. By default, the netgear will pass ZERO traffic to your lan, so you're actually punching holes in the firewall rather than securing the device.
If you have remote management configured on the netgear and someone there who could physically make the cable changes, you can easily test without physically being there.
- spaceobhOct 09, 2015Aspirant
SamirD wrote:
Thank you for the diagrams as it makes it very clear. I wish others could do that in their threads!
Yep, a picture is always good
So normally (and probably your current setup), the zyxel is in place of the netgear in the diagram showing the computer on the lan, correct? If so, you can plug a *default configuration* 318n wan port into the lan port of the zyxel and then the computer on the lan into the lan port on the 318n. By default, the 318n will allow traffic to pass to the zyxel which will in turn pass it on to the Internet. This should work without an issue.
I hear what you are saying, but this make the 318 a simple hub, right?
All those rules and services may be the issue. By default, the netgear will pass ZERO traffic to your lan, so you're actually punching holes in the firewall rather than securing the device.
Yeah, well, that was the intention, allow access for legal external IP adresses, and preventing unwanted.
If you have remote management configured on the netgear and someone there who could physically make the cable changes, you can easily test without physically being there.
I did that too, before I threw the towel, but after the futile attemtps to make the 318 forward the LAN/NAT/WAN-IP of the transmitting unit, I re-inserted the Zyxel.
The local hands are not able to fiddle with the 318, and since it's voluntary aid I don't want to exhaust my goodwill on an activity that will take a rather long time (already have) with little chance of success.
I may even consider getting another make unit for installation at the site.
Thanks for your contributions :smileyhappy:
- SamirDOct 09, 2015Prodigy
No, in this case, it's actually two routers with the netgear being the last router in the chain. But as far as ftp is concerned, all the routers should route the packets correctly. This is how the whole Internet works.
If you want someone from the outside to be able to connect to the computer connected to the netgear lan, then yes, you might need some rules. But let's tackle that after we figure out why a completely normal ftp transfer is acting funny.
I hear you on the voluntary aid. Well, here's what I would do the next time you are able to get there:
- Factory default the Netgear by holding down the reset. You can do this after printing out or noting down the current configuration.
- Connect the wan of the netgear to the lan of the zyxel
- Connect the lan of the netgear to the computer.In effect this will put the netgear in between the computer and the zyxel.
- Try your ftp again. It should work.
- Replace the Zyxel with the Netgear and try the ftp test again. It should work now too.
- Enable remote configuration on the netgear, but don't set up any rules or static routes yet.
- Post here with what you'd like to block/not block and we'll set up the rules via the remote configuration.
Related Content
NETGEAR Academy

Boost your skills with the Netgear Academy - Get trained, certified and stay ahead with the latest Netgear technology!
Join Us!