NETGEAR is aware of a growing number of phone and online scams. To learn how to stay safe click here.
Forum Discussion
Sarevian
Aug 09, 2015Aspirant
Trying to disable WPS (bringing the topic to the top of lists again)
So - I've had my R6300v2 for a day. I've fiddled with most settings and I'm happy that for most things it'll do what I need. ALL EXCEPT WPS! A week ago I ordered a D-Link which shocked me whe...
- Aug 11, 2015
You don't have a checkbox to disable WPS in Advanced Wireless Settings?
TheEther
Oct 11, 2015Guru
TL;DR Disable the Router's WPS PIN. Then all you have to worry about is physically securing the router. WPS will only be enabled for 2 minutes after the WPS button is physically pushed.
Ok, I did some research.
There are two methods WPS can be used on many routers, including Nighthawks.
- By entering the router's WPS PIN from a client.
- By pushing either the physical button or the soft push button in ADVANCED > WPS Wizard
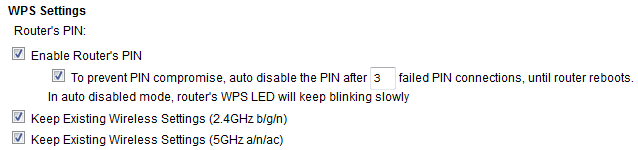
The WPS PIN in method #1 has been proven to be easy to hack. Netgear provides additional protection against PIN hacking by automatically disabling #1 if it detects 3 failed connections by the PIN method. It is also possible to disable #1 altogether as I have shown in my previous post by unchecking Enable Router's PIN.
The method you demonstrated is #2. You and netwrks are correct that it cannot be disabled, except by disabling SSID broadcast. The soft push button can only be accessed by logging into the router, so that's relatively secure. That leaves just the physical button on the router itself. If you can physically secure the router against prying hands, then you should be safe. WPS is not active when the PIN is disabled and is only active for 2 minutes after the push button is pressed.
If you are inclined, I suppose you could physically modify the router and remove/disable the push button. Personally, I think that would be overkill. If someone can physically access the router, then it would easier to connect to one of the Ethernet ports.
Sarevian
Oct 12, 2015Aspirant
Thanks again for your reply.
TheEther wrote:TL;DR Disable the Router's WPS PIN. Then all you have to worry about is physically securing the router. WPS will only be enabled for 2 minutes after the WPS button is physically pushed.
Ok, I did some research.
There are two methods WPS can be used on many routers, including Nighthawks.
- By entering the router's WPS PIN from a client.
- By pushing either the physical button or the soft push button in ADVANCED > WPS Wizard
The WPS PIN in method #1 has been proven to be easy to hack. Netgear provides additional protection against PIN hacking by automatically disabling #1 if it detects 3 failed connections by the PIN method. It is also possible to disable #1 altogether as I have shown in my previous post by unchecking Enable Router's PIN.
The method you demonstrated is #2. You and netwrks are correct that it cannot be disabled, except by disabling SSID broadcast. The soft push button can only be accessed by logging into the router, so that's relatively secure. That leaves just the physical button on the router itself. If you can physically secure the router against prying hands, then you should be safe. WPS is not active when the PIN is disabled and is only active for 2 minutes after the push button is pressed.
If you are inclined, I suppose you could physically modify the router and remove/disable the push button. Personally, I think that would be overkill. If someone can physically access the router, then it would easier to connect to one of the Ethernet ports.
"Then all you have to worry about is physically securing the router."
And that's my problem. This was for my daughter at uni. The guest feature looked great for enabling her to share the connection when and with whom she chose, and to share access to files on USB as she decided. But WPS makes setting up a connection very quick and - note my previous message - disabling the PIN actually makes no difference (at least on my R6300).
So, I guess it'll have to be the hidden SSID after all.
The lesser of two evils really.
One last thought - WPS really shouldn't be active permanently anyway. In most (domestic) setups, once you've used WPS to make the connections you need you don't need it again. Scans of my neighbourhood and other places I go show the majority of routers have WPS enabled. A simple Google search shows lots of articles about using an active WPS to gain access although it's also clear that some routers are more vulnerable than others. But it shouldn't be too surprising as you're removing the need for (an up-to) 63 character WPA password with a simple numerical PIN.
Enough from me, thanks for the replies. I'm going to mark this as solved and move on.
Next I need to find a place to moan about using biometrics for security. (In case it isn't obvious I'd better say I'm joking.)
- TheEtherOct 12, 2015Guru
Are you saying that the PIN still worked even though it was disabled in configuration? I would consider that a bug.
If your daughter is in a dorm, she should be careful about setting up her own wireless network. Many colleges have policies that prohibit that. It's not too hard for them to zero in on the location of a router.
- SarevianOct 12, 2015Aspirant
Thanks again for the reply.
TheEther wrote:
Are you saying that the PIN still worked even though it was disabled in configuration? I would consider that a bug.
If your daughter is in a dorm, she should be careful about setting up her own wireless network. Many colleges have policies that prohibit that. It's not too hard for them to zero in on the location of a router.
Indeed. PIN/No PIN works wonderfully well (!). A bug - I think you're right.
Thanks too for the warning about uni policies. Did check.
EXTRA EDIT :
With visiting this thread so often I'm now getting shown quite a few other forum discussions on a similar theme in the sidebar.
Some I saw before I started my post but I managed to miss this one before -
Haven't had time to try these ideas out but worth a go some time.
Over and out.
- HitPointOct 20, 2015Aspirant
Why do you need WPS off completely when you have to physically hit the button anyway to allow access. The only way a bruteforce can get through your router is through the PIN, which when disabled removes any security threats through WPS... I think the only thing that might be an issue is if you have a guest/family member in your household that you're trying to prevent access and they're somehow getting to the WPS button, then I would understand your dilemma to a point, but still there is ways of preventing such acts with a few simple steps ---
1. Move the router to your room and hide it from plain sight
2. Ask your guest politely to leave the router alone
3. Stop being paranoid, no one is trying to hack your router (circumstantial).
WPS itself is a security feature to allow other means of supplying network access without SSID broadcast (most secure feature on the router). Netgear giving the option to disable WPS completely would only make security worse for you and your network. Not to mention WPS itself is built into the router without a circuit switch so that option is not possible in the first place unless it was added with newer models.
Again, if you want total physical control over security from within your network then you need to take the necessary steps I listed above. It's not Netgear's problem to fix your networking dilemma within your household, that's between you and your family/guests. Anyways, I hope you get through your issue and hopefully find eventual peace. I'm a network security nut myself and take pride in securing every hole and every vulnerability.
-Mike
- TheEtherOct 21, 2015Guru
I am in agreement with you about physically securing your router, but you lost me with your assertion that WPS is the "most secure feature on the router". It has been well known since 2011 that the WPS PIN is fundamentally insecure. There are only 11,000 combinations for the PIN. (Source: Wikipedia). Moreover, devices that provide WPS must support PIN as a baseline requirement! I suppose we should be thankful that Netgear provided options to protect the PIN against bruteforce attacks as well as disable the PIN, but why not offer the option to disable it altogether?
The best way to secure Wi-Fi is to use WPA2 with a strong password. It should be long and it should include upper and lower case letters, numbers and special characters. WPS was conceived to simplify the task of joining a Wi-Fi network. That's a noble idea, but unfortunately the design is broken.