NETGEAR is aware of a growing number of phone and online scams. To learn how to stay safe click here.
Forum Discussion
IrvSp
Oct 11, 2015Master
R7000 Log MAC address issue, can't locate?
I keep seeing this MAC address in my e-mailed log, F0:A2:25:04:27:37, and it is NOT in my list of ALLOWED devices or ATTACHED DEVICES for the router?
From the logs sent:
[DHCP IP: (192.168.1.6)] to MAC address F0:A2:25:04:27:37, Sunday, Oct 11,2015 03:59:38
[DHCP IP: (192.168.1.6)] to MAC address F0:A2:25:04:27:37, Sunday, Oct 11,2015 03:24:39
[DHCP IP: (192.168.1.6)] to MAC address F0:A2:25:04:27:37, Saturday, Oct 10,2015 03:59:37
[DHCP IP: (192.168.1.6)] to MAC address F0:A2:25:04:27:37, Saturday, Oct 10,2015 03:24:39
Even weeks ago
[DHCP IP: (192.168.1.6)] to MAC address F0:A2:25:04:27:37, Wednesday, Sep 16,2015 03:59:39
[DHCP IP: (192.168.1.6)] to MAC address F0:A2:25:04:27:37, Wednesday, Sep 16,2015 03:24:40
Web Searches and engines that search the address show it as PRIVATE?
Always the same time too it seems. This a function within the R7000? I have NO devices attached to 192.168.1.6 either nor any MAC Address even close the that? If a function of R7000 others would see this too I guess?
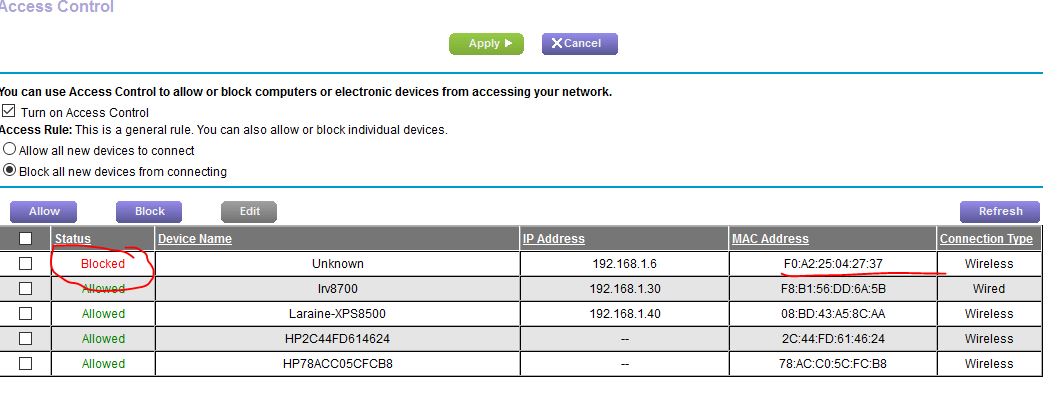
If this 'device' did get access shouldn't is show somewhere in the Browser under ADVANCED -> SECURITY -> ACCESS CONTROL?
I've turned on ACCESS CONTOL (With all its problems) to see if I can identify it and block it?
Any ideas?
Changed them but I'm wondering if it could be the USB drive attached to the Router? I use it as a Media Server (DLNA). However that has a different MAC address, c4:04:15:29:8f:3d, and I've never seen that in the log? The drive 'share' doesn't have a MAC address though.
Test will be tomorrow morning I guess?
Just discovered a Kindle that was sleeping...
Also I just looked at the log, IT IS HERE somewhere?
[Admin login] from source 192.168.1.30, Monday, Oct 12,2015 12:00:06
[WLAN access rejected: incorrect security] from MAC 2C:44:FD:61:46:24, Monday, Oct 12,2015 12:00:06
[WLAN access rejected: incorrect security] from MAC 10:AE:60:57:25:06, Monday, Oct 12,2015 12:00:05
[WLAN access rejected: incorrect security] from MAC 78:AC:C0:5C:FC:B8, Monday, Oct 12,2015 12:00:05
[WLAN access rejected: incorrect security] from MAC F0:A2:25:04:27:37, Monday, Oct 12,2015 12:00:05
[WLAN access rejected: incorrect security] from MAC 2C:44:FD:61:46:24, Monday, Oct 12,2015 12:00:05
[WLAN access rejected: incorrect security] from MAC 10:AE:60:57:25:06, Monday, Oct 12,2015 12:00:04
[WLAN access rejected: incorrect security] from MAC 78:AC:C0:5C:FC:B8, Monday, Oct 12,2015 12:00:04
[WLAN access rejected: incorrect security] from MAC F0:A2:25:04:27:37, Monday, Oct 12,2015 12:00:04
[WLAN access rejected: incorrect security] from MAC 2C:44:FD:61:46:24, Monday, Oct 12,2015 12:00:04Now as I change the passphrase to allow devices to connect I should be able to determine WHO it is?
Yeah, it was the Kindle... sheesh:
Allowed it and it connected...
[DHCP IP: (192.168.1.6)] to MAC address F0:A2:25:04:27:37, Monday, Oct 12,2015 12:12:47
Who knew?
11 Replies
A private MAC address is an address where the vendor has opted to register the OUI as private. See this page for reference. You can find the entry for OUI F0:A2:25 in the IEEE OUIs page. Warning, it's a big file.
Note that a private MAC address is different from a locally administered MAC address. A locally administered MAC address has the 2nd least significant bit set in the first octet. See the details on Wikipedia.
At first, I thought that F0:A2:25:04:27:37 was a locally administered MAC address (it's not because the 2nd least significant bit is not set). I know that Apple introduced the use of locally administered MAC addresses with iOS 8 in order to enhance privacy. It's mentioned here and described in further detail here. It turns out that iOS only uses a locally administered MAC address when probing for Wi-Fi networks, not when DHCPing for an IP address. Plus, as I already stated, the address in question is not locally administered, so the mysterious device is probably not an Apple.
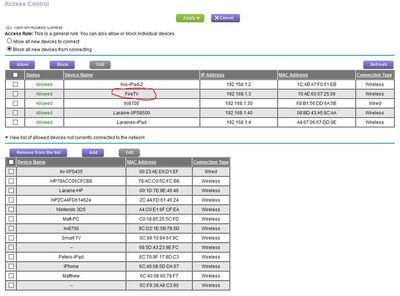
Did you look at the Attached Devices page? If it's not currently attached, then that may explain why it's not showing up in Access Control.
If you are unable to find the device, then I think it's time to change your Wi-Fi passwords. You should probably change the router's admin password just to be safe. And make sure the guest network is disabled.
- IrvSpMaster
We can continue this e-mail if you wish, but I did search the list you referenced:
==========
F0-A2-25 (hex) Private F0A225 (base 16) Private
==========
The Attached Devices of course it wouldn't be on there. However it doesn't show on ANY list (Attached, Allowed, or Blocked) on the Acess Control page either?
Interestingly I found I asked this same question awhile ago, here (old forum) and other places with no resolution:
https://forum1.netgear.com/t5/Nighthawk-WiFi-Routers/Questions-about-my-LOG-entries/td-p/509827
http://www.dslreports.com/forum/r29729174-R7000-Log-entry-questions?group=noreply
The common denominator here is the FireTV stick.
What CAN be connected to the Router...
The Blocked list has a single device, a phone from the ISP's tech from when he was last here.
The difference between those Dec. 2014 reports and today is I was on W8.1 then and there was a way to remove the spurious phone from appearing via a Service change I found.
I suspect, but can't confirm it is related to the FireTV stick. That appears to be the start of that appearing I think?
I am assuming Access Control being turned on will help identify the device as it tries to connect. It should be blocked. Why twice at almost the same time each day (old references above have the same time if you take Daylight Savings time into consideration).
- IrvSpMaster
Should add that Guest Network is OFF and was NEVER on as well as the WPS PIN being OFF.
The iPad's do renew their leases before the odd one occurs:
[DHCP IP: (192.168.1.6)] to MAC address F0:A2:25:04:27:37, Sunday, Oct 11,2015 03:59:38 [DHCP IP: (192.168.1.6)] to MAC address F0:A2:25:04:27:37, Sunday, Oct 11,2015 03:24:39 [DHCP IP: (192.168.1.4)] to MAC address A4:67:06:57:DD:0E, Sunday, Oct 11,2015 03:13:24 [DHCP IP: (192.168.1.2)] to MAC address 1C:AB:A7:F0:61:EB, Sunday, Oct 11,2015 03:06:55
Those are the .2 and .4 addresses. However there is a time difference so I don't think we could relate the .6's to each iPad.
[DHCP IP: (192.168.1.6)] to MAC address F0:A2:25:04:27:37, Saturday, Oct 10,2015 03:59:37 [DHCP IP: (192.168.1.6)] to MAC address F0:A2:25:04:27:37, Saturday, Oct 10,2015 03:24:39 [DHCP IP: (192.168.1.4)] to MAC address A4:67:06:57:DD:0E, Saturday, Oct 10,2015 03:02:39 [DHCP IP: (192.168.1.2)] to MAC address 1C:AB:A7:F0:61:EB, Saturday, Oct 10,2015 02:52:09
Only that it does happen after each iPad gets the lease renewal.
I've decided to add F0:A2:25:04:27:37 to the BLOCKED list and see what happens rather than wait for Access Control to put something in the log. I guess it is possible that a neighbor's device found my signal stronger and tried to connect but the time makes me think that wouldn't be the case? However the neighbor's bedroom is probably closer to my router than his is (I've helped him on occassion and know where his router is. Still it would be impossible for him to connect without my password(s). He's never been here connecting either. Would a Phone's MAC address be registered to the vendor too?
As a test if the blocking doesn't show me something tomorrow morning I think I'll disconnect the FireTV. At that hour ONLY the 2 iPad's and the FireTV are powered on. We do have a SmartTV but that is off but I guess there is the possibility of it doing it even if off as AC is connected?
I really don't think it is outside my house though?
- netwrksMaster
Or give the Fire TV a static ip address and see what shows up in the logs..
- Like I said, Access Control is enforced after DHCP. And DHCP occurs after the Wi-Fi paraphrase is accepted. Ergo, that rogue device either has the correct paraphrase or it's plugged in via Ethernet.
I'm glad you finally decided to change your paraphrase. That's what I originally suggested.- IrvSpMaster
Changed them but I'm wondering if it could be the USB drive attached to the Router? I use it as a Media Server (DLNA). However that has a different MAC address, c4:04:15:29:8f:3d, and I've never seen that in the log? The drive 'share' doesn't have a MAC address though.
Test will be tomorrow morning I guess?
Just discovered a Kindle that was sleeping...
Also I just looked at the log, IT IS HERE somewhere?
[Admin login] from source 192.168.1.30, Monday, Oct 12,2015 12:00:06
[WLAN access rejected: incorrect security] from MAC 2C:44:FD:61:46:24, Monday, Oct 12,2015 12:00:06
[WLAN access rejected: incorrect security] from MAC 10:AE:60:57:25:06, Monday, Oct 12,2015 12:00:05
[WLAN access rejected: incorrect security] from MAC 78:AC:C0:5C:FC:B8, Monday, Oct 12,2015 12:00:05
[WLAN access rejected: incorrect security] from MAC F0:A2:25:04:27:37, Monday, Oct 12,2015 12:00:05
[WLAN access rejected: incorrect security] from MAC 2C:44:FD:61:46:24, Monday, Oct 12,2015 12:00:05
[WLAN access rejected: incorrect security] from MAC 10:AE:60:57:25:06, Monday, Oct 12,2015 12:00:04
[WLAN access rejected: incorrect security] from MAC 78:AC:C0:5C:FC:B8, Monday, Oct 12,2015 12:00:04
[WLAN access rejected: incorrect security] from MAC F0:A2:25:04:27:37, Monday, Oct 12,2015 12:00:04
[WLAN access rejected: incorrect security] from MAC 2C:44:FD:61:46:24, Monday, Oct 12,2015 12:00:04Now as I change the passphrase to allow devices to connect I should be able to determine WHO it is?
Yeah, it was the Kindle... sheesh:
Allowed it and it connected...
[DHCP IP: (192.168.1.6)] to MAC address F0:A2:25:04:27:37, Monday, Oct 12,2015 12:12:47
Who knew?