NETGEAR is aware of a growing number of phone and online scams. To learn how to stay safe click here.
Forum Discussion
MasterPhil
Feb 04, 2017Tutor
M4300 12x12f no vlans while stacking failover
Hello community, I have two m4300-12x12f as core switches which are stacked with enabled NSF. The member should be in standby until the master fails. Then the standby core should work. I tested the...
MasterPhil
Feb 05, 2017Tutor
Hello LaurentMa!,
thank you for your advices. First of all Im writing from Germany so may my grammar is not perfect ;-).
Sure I thought that the right 'core' switch is in standby and not active. I don't understand the stacking feature - there are options called stack member, standby and NSF. What should I use to stack the cores? Actually standby and NSF are configured, but no LAG. I thought because of standby the one core is inactive. So both ports (on the left and right switch) should be added to a LAG? The core switches are stacked with one wire.
The s3300 switches are the access layer. In some racks there are two switches stacked with one wire. One switch is the master, the other is configured as stack member. From the master one cable is connected to the master core switch and from the other s3300 one cable is connected to the member core. Now I have to configure between the master and member s3300 a LAG too?
The VLAN:
I will test it later, but yesterday I saw that on the Web GUI the vlan is configured on both ports (1/0/15 and 2/0/15) and the PVID is the same. All settings should be the same for vlan for both cores. May I have to set the switches to factory defaults?
I have a few other questions:
-when I use the built in dhcp on the core do I have to enable dhcp Relay on every access switch and what do I have to configure? The manual didn't help me.
-when I use an external dhcp do I have to activate dhcp Relay on the core and on every access switch and what do I have to configure?
-is the dhcp active on both cores because of stacking? Do I have to configure something to prevent dhcp on both switches at the same time?
-while vlans are configured they can communicate among themselves. I have to restrict it by using ACLs?
Kind Regards
thank you for your advices. First of all Im writing from Germany so may my grammar is not perfect ;-).
Sure I thought that the right 'core' switch is in standby and not active. I don't understand the stacking feature - there are options called stack member, standby and NSF. What should I use to stack the cores? Actually standby and NSF are configured, but no LAG. I thought because of standby the one core is inactive. So both ports (on the left and right switch) should be added to a LAG? The core switches are stacked with one wire.
The s3300 switches are the access layer. In some racks there are two switches stacked with one wire. One switch is the master, the other is configured as stack member. From the master one cable is connected to the master core switch and from the other s3300 one cable is connected to the member core. Now I have to configure between the master and member s3300 a LAG too?
The VLAN:
I will test it later, but yesterday I saw that on the Web GUI the vlan is configured on both ports (1/0/15 and 2/0/15) and the PVID is the same. All settings should be the same for vlan for both cores. May I have to set the switches to factory defaults?
I have a few other questions:
-when I use the built in dhcp on the core do I have to enable dhcp Relay on every access switch and what do I have to configure? The manual didn't help me.
-when I use an external dhcp do I have to activate dhcp Relay on the core and on every access switch and what do I have to configure?
-is the dhcp active on both cores because of stacking? Do I have to configure something to prevent dhcp on both switches at the same time?
-while vlans are configured they can communicate among themselves. I have to restrict it by using ACLs?
Kind Regards
LaurentMa
Feb 05, 2017NETGEAR Expert
Hi MasterPhil
All good questions here, I'm sure it will be of fair interest for many other members in our Community.
Let me answer your questions the one after the other.
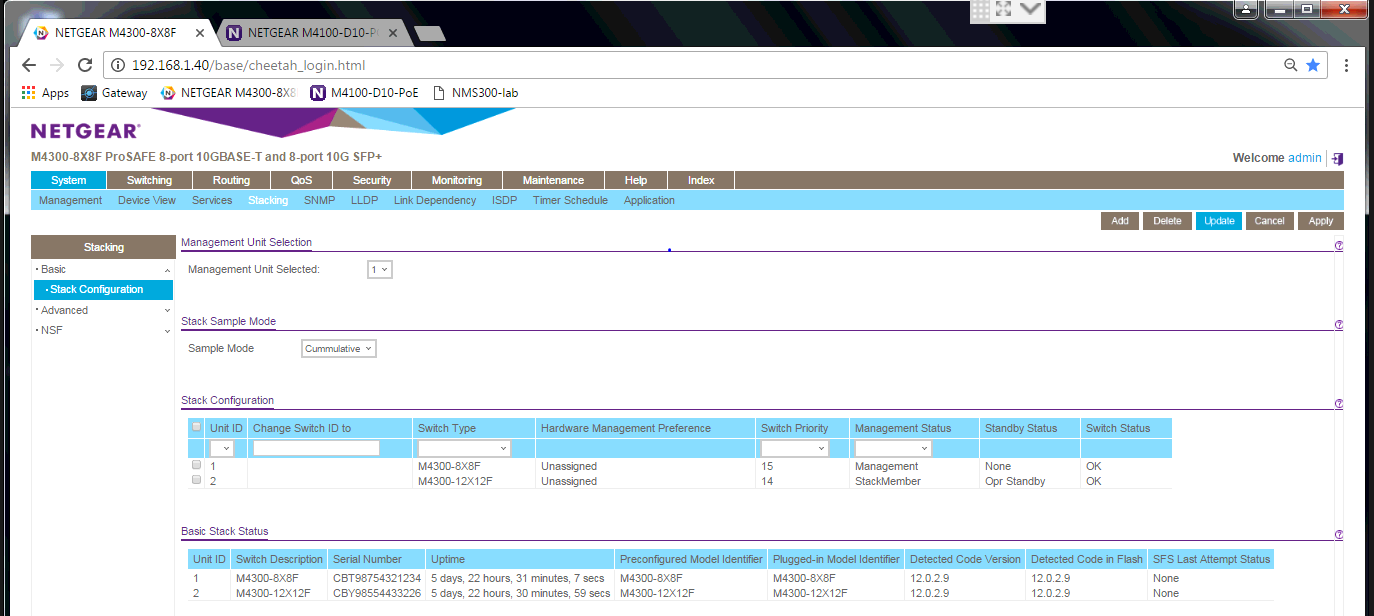
Yes your 'right' core switch is active, not in standby mode in terms of switch operation. When you go to System-->Stacking-->Basic-->Stack Configuration, please control it's like:
In my setup, left switch is unit 1 and right switch is unit 2.
- Left switch (unit 1) is Management unit, so the stack master
- Right switch (unit 2) is StackMember, so a member of the stack.
Next column Standby status shows right switch (unit 2) as 'Opr Standby'. This is normal, in a two-switch stack the second unit is meant to handle the Backup management role. For this, it is standby in terms of Management. But management only! Aside from this management role, the right switch (unit 2) is fully operational, all ports active and forwarding/routing traffic. Yes, NSF is very important, it is enabled by default, it lets the failover and failback happen without traffic disruption across the stack. Please check if your setup is similar to mine. If not, please fix that first.
I see you have S3300 stacks in your network: M4300 core stack is no different for that. Both switches are operational from a network operation standpoint. One switch is the Master (management unit), the other switch is a stack member handling backup management role (Opr Standby). What M4300 brings you on top, is Nonstop forwarding. This is unique to M4300 (no possible service interruption during failover and failback operations).
Yes, as much as you can, you should have your other network devices (servers etc..) and access layer switches dual-homed to your core stack using LACP link aggregation across two switches each time. Why? Because LACP LAGs will automatically handle failover and failback operations in your core - so in case of a switch problem at the core - without any service interruption. This is the whole point of a redundant core: dual-homed connections to that core using LACP for load-balancing and instant failover from one link to the other without breaking UDP/TCP sessions.
If your S3300 stacks at the access layer have one link from each S3300 switch to each M4300 switch at the core without LAG, this is not good. You are creating loops in your network all the way South to North. Hopefully M4300's are gentle enough to handle this automatically with RSTP enabled by default and shutting down the ports where loops are occuring in real time. But you must realize it is a problem, since you have ports shutdown by spanning tree at your core when it shouldn't be, right? With dual-home connections from your S3300 stacks at the edge to your redundant core, what you want is load-balancing, and automatic failover without possible outage. So yes, for that please disconnect your S3300s, and create LAGs on your S3300 stacks, and LAGs on your M4300 core stack. Please enable LACP (dynamic LAGs) on your S3300's since it is disabled by default on Smart managed switches.
LAGs you will not use your old current port configuration anymore, so please configure the new LAGs after they are created (VLAN membership). In general, LAGs carry all tagged VLANs as trunks, plus one untagged Native VLAN (PVID) if needed.
The VLAN problem: yes please check, it is very likely you have different configuration between 1/0/15 and 2/0/15 at this stage. Please make it the very same. Please download the configuration file as I said earlier to double-check that, it is sometimes easier to read a text configuration file all the way for spotting mistakes (at least for me).
Your last questions:
- Please refer to this other post in order to use built-in DHCP server pool on your M4300 core stack and 'attach' each DHCP server to each VLAN
- If your have one DHCP Server per VLAN in your M4300 core stack, you can use DHCP Relay agents on your S3300 edge switches. First please check all your LAGs can carry all VLANs properly as trunks for good North-South VLAN proliferation. Second please consult S3300 user manual starting page 93 for enabling L2 DHCP relays on your S3300's for each of your VLANs .
- When you use an external DHCP server on another subnet and where there's no active static route leading to it for a particular switch in your network, you need Layer 3 DHCP (UDP) Relays on each VLAN, which Smart managed switches like S3300s don't provide. Only M4300 Fully managed switches let you configure L3 DHCP UDP relays indicating the IP address of your external DHCP in another subnet using IP Helpers. So in your case, you should make sure your M4300 core stack properly route all VLANs to the subnet where your external DHCP server is; or configure L3 DHCP UDP Relay on your M4300 core stack for each VLAN, indicating the IP address of your external DHCP server. Please consult M4300 User Manual page 98.
- Is the DHCP active on both cores because of stacking? Again there is misunderstanding here, let's clearly explain it. You have only one core, which is a stack of two switches behaving like a unique, virtual big switch. When you configure it, you see it as a big switch. Other devices in the network also see it as a big switch. When you configure local DHCP server pool on it, you do it for the entire stack and for all switches. Your DHCP server is active everywhere across the stack, this is the whole point of such virtual chassis stacking architecture.
Leads me to indicate this is why M4300 spine and leaf stacking architecture is so popular for midsize networks: when you stack M4300 core 10G switches with all M4300 1G edge switches together - in same big switch - then your configuration (DHCP, VLANs, etc.) is very simple. You manage only one big switch - a real collapsed core from the core to the edge. You have only one configuration for the big switch. All VLANs have their embedded DHCP server locally etc.
- Yes, when activating Layer 3 routing, your VLAN Layer 2 boundaries remain for broadcast - that's why it's good network segmentation - but they are gone for all other inter-VLAN communications at L3. So either you restrict inter-VLAN communication using ACLs, either you deploy Private VLANs on top of your existing VLANs.
I would advise you deploy ACLs. For that, please refer to M4300 Software admin manual which is a collection of configuration examples. Please reproduce Use ACLs to Configure Isolated VLANs on a Layer 3 Switch starting page 184.
I hope it will be helpful for you, please let us know how it goes!
Regards,
- MasterPhilFeb 05, 2017Tutor
Hi,
I reconfigured my Switches and know the VLAN works. I also configured a LAG between the two cores and the S3300 Switches. I think my problem was, that I connected my switches to a loop withoud enabling LAG. Now I tested all features with two PCs. One connected to the S3300 and the other connected to one Core. If I unplug one uplink-cable from the Core switch, where my PC is connected, I loose one ping. Then I connected one PC to the Core, which is not Stack Master. If I power off the other Core Switch, which is Stack Master I loose 4-5 pings until it becomes Stack Master. Are these worths OK? I configured the Stacking-Feature as shown in your picture.
I dont know the differnce between the Management Status "Standby" and "Stacking Member". What If I choose "Standby"? I can see, that the Standby Status switches to "Cfg Standby".
I configured the DHCP Server on my M4300 and it works fine. One PC connected to a S3300 became an IP-Address from the M4300, so I don´t have to enable DHCP Relay on the S3300? I thought I must enable it. Is it possible to define a IP-Pool e. g. from 172.16.1.100 to 200?
Related Content
NETGEAR Academy

Boost your skills with the Netgear Academy - Get trained, certified and stay ahead with the latest Netgear technology!
Join Us!