NETGEAR is aware of a growing number of phone and online scams. To learn how to stay safe click here.
Forum Discussion
XDRich
Feb 15, 2017Guide
STP Leak using Broadcast packet 01:80:c2:00:00:1c
Netgear Support, Please take note that the community and several customers have discovered a possible flaw in your STP implementation that causes CPU panic and circular broadcasts that disable sw...
- Jun 07, 2017
LarryV and to others,
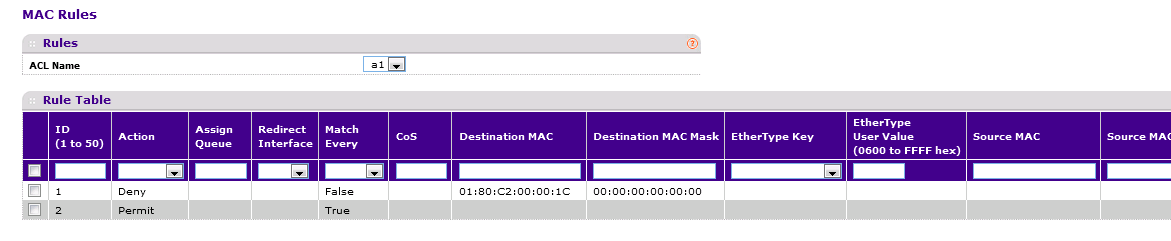
Since a firmware fix is not yet available, the MAC ACL workaround can be used as described on the article below:
Regards,
DaneA
NETGEAR Communtiy Team
XDRich
Feb 23, 2017Guide
Has anyone from Netgear seen this and can comment?
melkesr
Feb 23, 2017Aspirant
- LaurentMaFeb 23, 2017NETGEAR Expert
Hi
Thank you for your messages. Please understand that the Community would really need, at very least, the Model Number of the switch presenting the issue. I'm sure this would trigger faster response rate.
But yes, to answer your questions, several key people in NETGEAR Community as well as several NETGEAR employees at Tech Support, Engineering Q&A and PLM heard about this new issue.
I am not sure which switches you have, but in case these are Smart Managed Switches (GS1xxTxx, GS5xxTxx, GS7xxTxx, XS7xxTxx) or above, please use the solution provided in this thread. Please enable Storm Control first. If not sufficient, you can use a MAC Access Control List (ACL) to drop packets with a target hardware address of 01:80:c2:00:00:1c. You can attach this ACL to your ports and your LAGs between your switches.
Please let us know how it goes, while we are investigating on our side.
Regards,
- XDRichFeb 23, 2017Guide
Thanks for the consideration and looking into it.
I currently have the MAC acl on and that prevents the packets. But that is not a long term fix.
I have two GS716Tv3 and one GS110TP all running the latest firmware.
The three switches run 5 vlans and STP (MSTP) is running.
All interconncected.
Hope that helps diagnose it.
- LaurentMaFeb 24, 2017NETGEAR Expert
Thank you XDRich, yes it helps.
We can reproduce the issue now. The offending packet is a multicast packet with MAC destination address of “01:80:c2:00:00:01c” that was generated by Ubiquiti’s new wifi AP software 3.7.37 release. The switch would react negatively as you’d reported when it received such packet, but there is no long term impact to the switch.
We’ll test all Netgear switches to ensure if any other models might be affected to this same issue and for affected series, we will provide permanent fix without requiring filtering out these packets using MAC ACL.
We will regularly update the team here on our progress.
Regards,
Laurent Masia
NETGEAR Senior Product Line Manager, Smart Switches & Managed Switches
- LarryVMay 25, 2017Aspirant
We have hundreds of Netgear switches and hundreds of UniFi APs under management at various sites. We're only having this problem with one GSM7224 (not listed in the pulldown above). It is not stacked. We have another identical switch in another building at this site and it is not exhibiting the issue. I found that the good one was running 8.0.1.26 firmware while the broken on was at 8.0.1.36. Downgrading to the older firmware on that switch did not resolve the issue however. We've implemented the temp fix as recommended here and are wating for something permanent.
- LaurentMaMay 30, 2017NETGEAR Expert
Hi
Sorry for this issue. Is your GSM7224 a M4100 GSM7224v2h2 (M4100-26G) for which we are releasing 10.0.2.25?
Regards,
- LarryVJun 06, 2017Aspirant
Nope. This is an old-fashioned GSM7224V2 running 8.0.1.26. I had downgraded from 8.0.1.36 because we have another identical switch at this location that was not impacted by the UniFi upgrade. That didn't resolve the problem and I have no idea why one switch is fine and the other is problematic.
Related Content
NETGEAR Academy

Boost your skills with the Netgear Academy - Get trained, certified and stay ahead with the latest Netgear technology!
Join Us!