NETGEAR is aware of a growing number of phone and online scams. To learn how to stay safe click here.
Forum Discussion
XDRich
Feb 15, 2017Guide
STP Leak using Broadcast packet 01:80:c2:00:00:1c
Netgear Support,
Please take note that the community and several customers have discovered a possible flaw in your STP implementation that causes CPU panic and circular broadcasts that disable switches and some other vendor gear.
The effect happens when the packet 01:80:c2:00:00:1c is broadcast from a Ubiquity AP. The scenario is as follows.
If you have two or more switches connected with lags and redundant links in a circular fashion, with STP and MSTP on. the redundant links.
The redundant links show that they are disgarding packets as normal.
However this packet is 01:80:c2:00:00:1c is getting past the stp disgard and continues to circulate around the links in perpetuity and is being constistently reflected by the switches.
The only respit is to remove the redundant link or put a MAC ACL on the lags to prevent the panic.
Please look into this issue.
I am runing the latest FW 6.3.1.16
The issue is well documented on the UBNT forums here, and we are asking both Netgear and UBNT to figure out what is going on and how to repair this ...
Thanks
Rich
LarryV and to others,
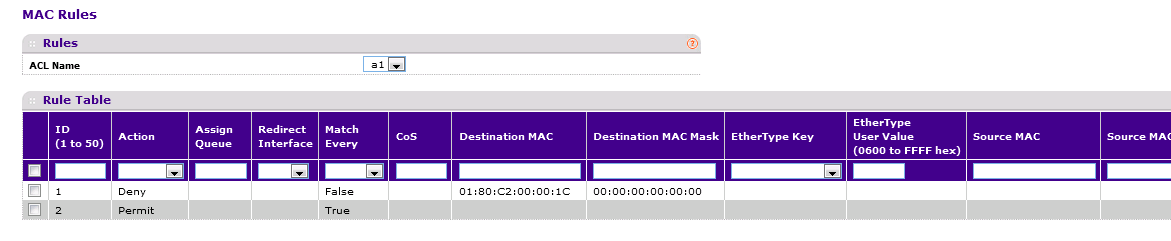
Since a firmware fix is not yet available, the MAC ACL workaround can be used as described on the article below:
Regards,
DaneA
NETGEAR Communtiy Team
38 Replies
- XDRichGuide
Has anyone from Netgear seen this and can comment?
- melkesrAspirant
- LaurentMaNETGEAR Expert
Hi
Thank you for your messages. Please understand that the Community would really need, at very least, the Model Number of the switch presenting the issue. I'm sure this would trigger faster response rate.
But yes, to answer your questions, several key people in NETGEAR Community as well as several NETGEAR employees at Tech Support, Engineering Q&A and PLM heard about this new issue.
I am not sure which switches you have, but in case these are Smart Managed Switches (GS1xxTxx, GS5xxTxx, GS7xxTxx, XS7xxTxx) or above, please use the solution provided in this thread. Please enable Storm Control first. If not sufficient, you can use a MAC Access Control List (ACL) to drop packets with a target hardware address of 01:80:c2:00:00:1c. You can attach this ACL to your ports and your LAGs between your switches.
Please let us know how it goes, while we are investigating on our side.
Regards,
- LaurentMaNETGEAR ExpertPlease be sure Engineering team is working on this issue across our portfolio. So MAC ACL is temporary workaround only. But very efficient.
Yes please apply the MAC ACL discarding these packets, on all ports which are connecting the Access Points. It is not necessary to bind the ACL with other ports.
Regards, - RedTechieAspirant
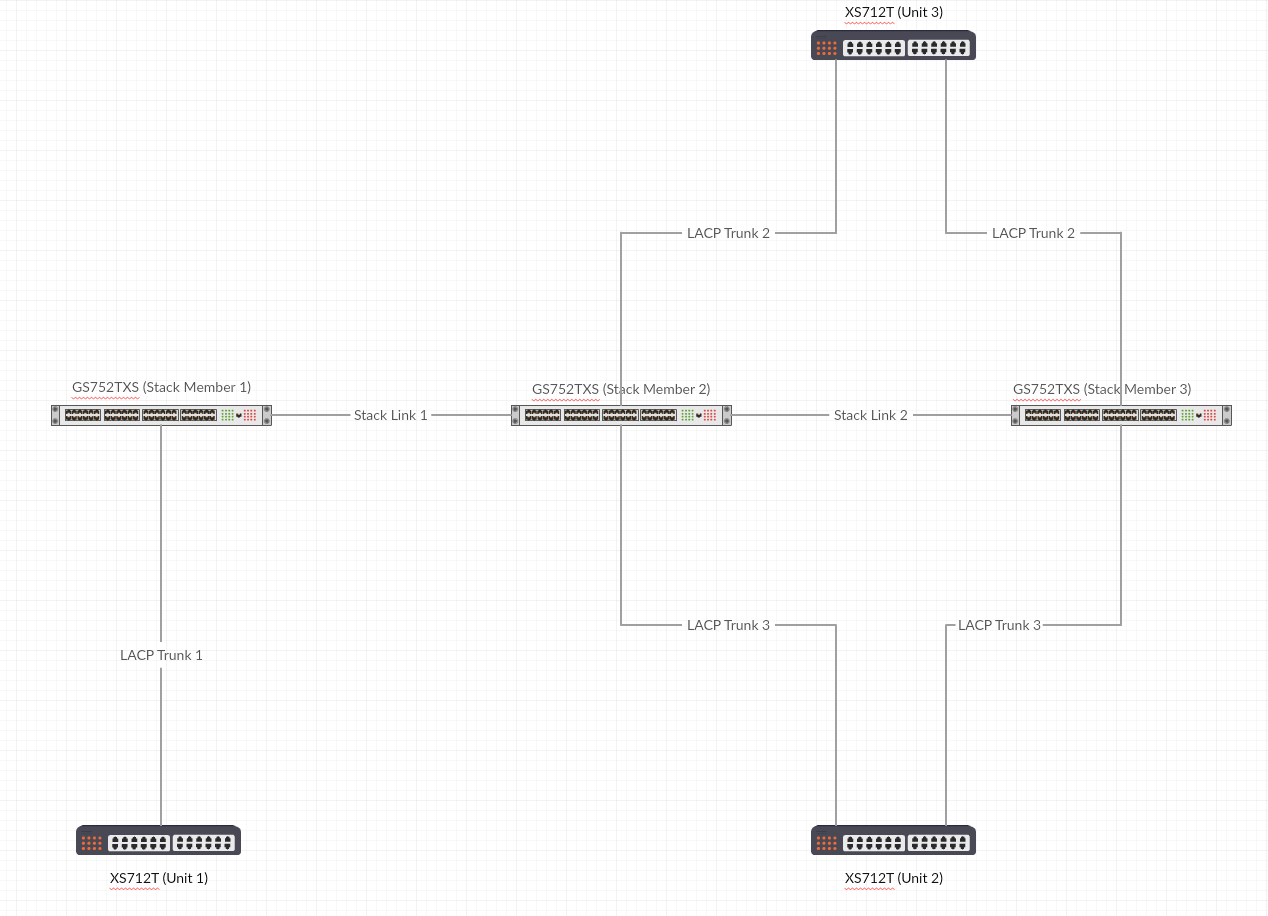
XDRich Could you further explain "Pick one of the lags that create your circular network and add it there. That prevents the reflection in the network while allowing the packet to get out and be used."? I just recently bought a second UAP-AC-HD and would like to take advantage of the quick roaming (802.11r) feature but not have my network melt at the same time :) (See attached image for switch topology) What link should I enable the ACL on? Just one of the Stack links, multiple? what about the LACP trunks?
LaurentMa Any update on the pending firmware fix from engineering?
Thanks!
Related Content
NETGEAR Academy

Boost your skills with the Netgear Academy - Get trained, certified and stay ahead with the latest Netgear technology!
Join Us!